Overview
Petra Security’s primary focus is to detect account compromises. There are many benign cases of VPN and proxy use, and Petra differs from other security tools by performing deep analysis to weed out benign VPN and proxy use. However, there are many cases where VPN and proxy use can demonstrate deep analysis and launch important conversations with your stakeholders. We preserve and spotlight these benign VPN and proxy uses to help you deeply understand your environment.All proxy and VPN use outlined here is benign. Malicious VPN/proxy use is a small fraction,
and is classified as an incident.
Two Investigation Methods
Petra offers two primary ways to investigate proxy and VPN use:- Reporting Interface - Quick overview of uncommon proxy activities
- Logs Viewer - Detailed analysis with advanced filtering capabilities
Using the Reporting Interface
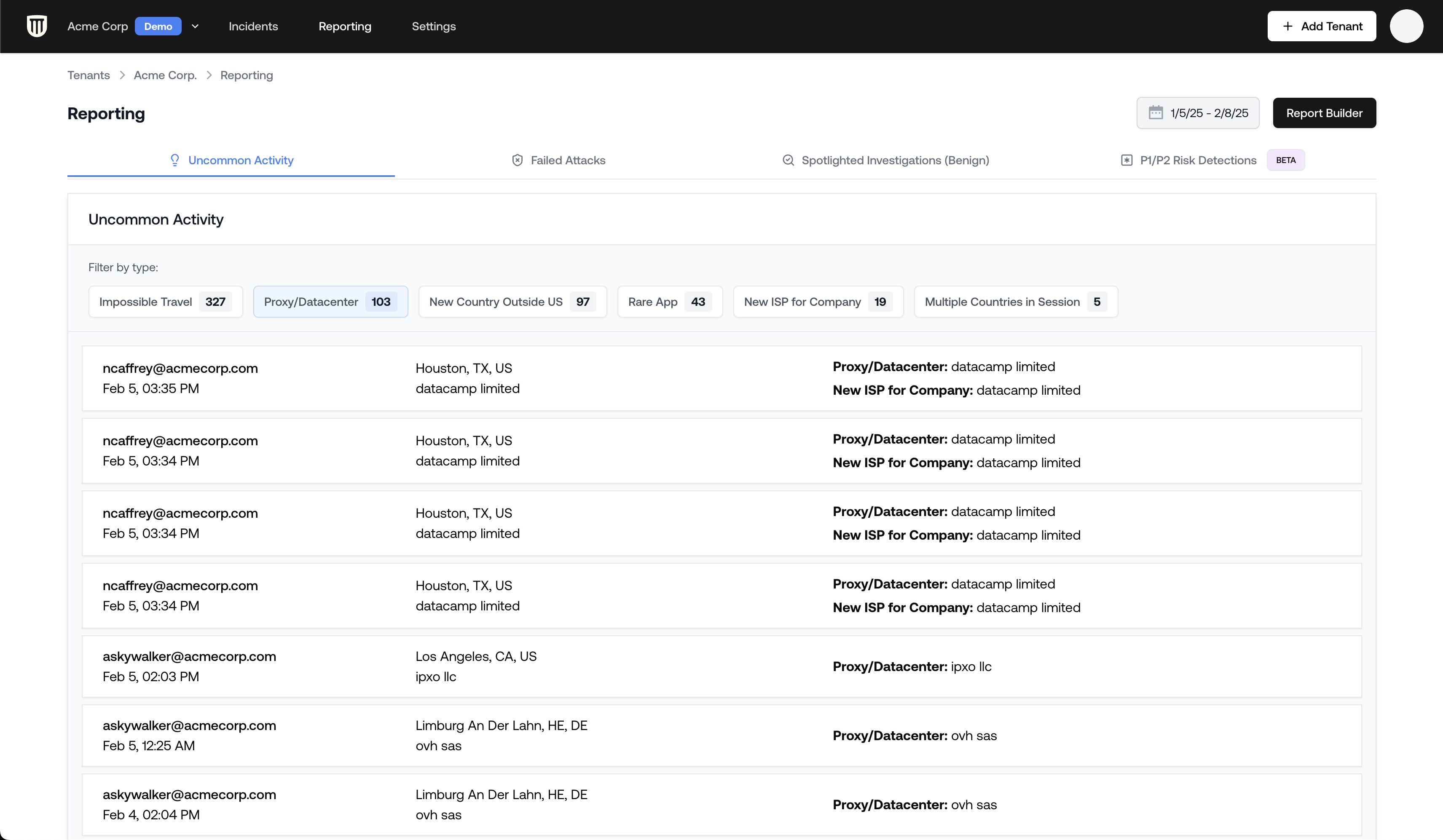
The reporting interface provides a straightforward (and stakeholder-friendly) view of uncommon proxy activities:- Navigate to your tenant by selecting it from the top left corner
- Click on the Reporting tab in the top navigation bar
- Select the Uncommon Activity tab
- Filter by Type: “Proxy and Data Center Use”
- User information
- Time of access
- Proxy/data center details
Detailed Analysis with Logs Viewer
For more in-depth investigation:- Navigate to your tenant’s main page
- Scroll down to the Activity panel
- Apply filters:
- Set Proxy: Yes to show only proxy traffic
- Add Login Status: Successful to focus on successful logins
Advanced Filtering Options
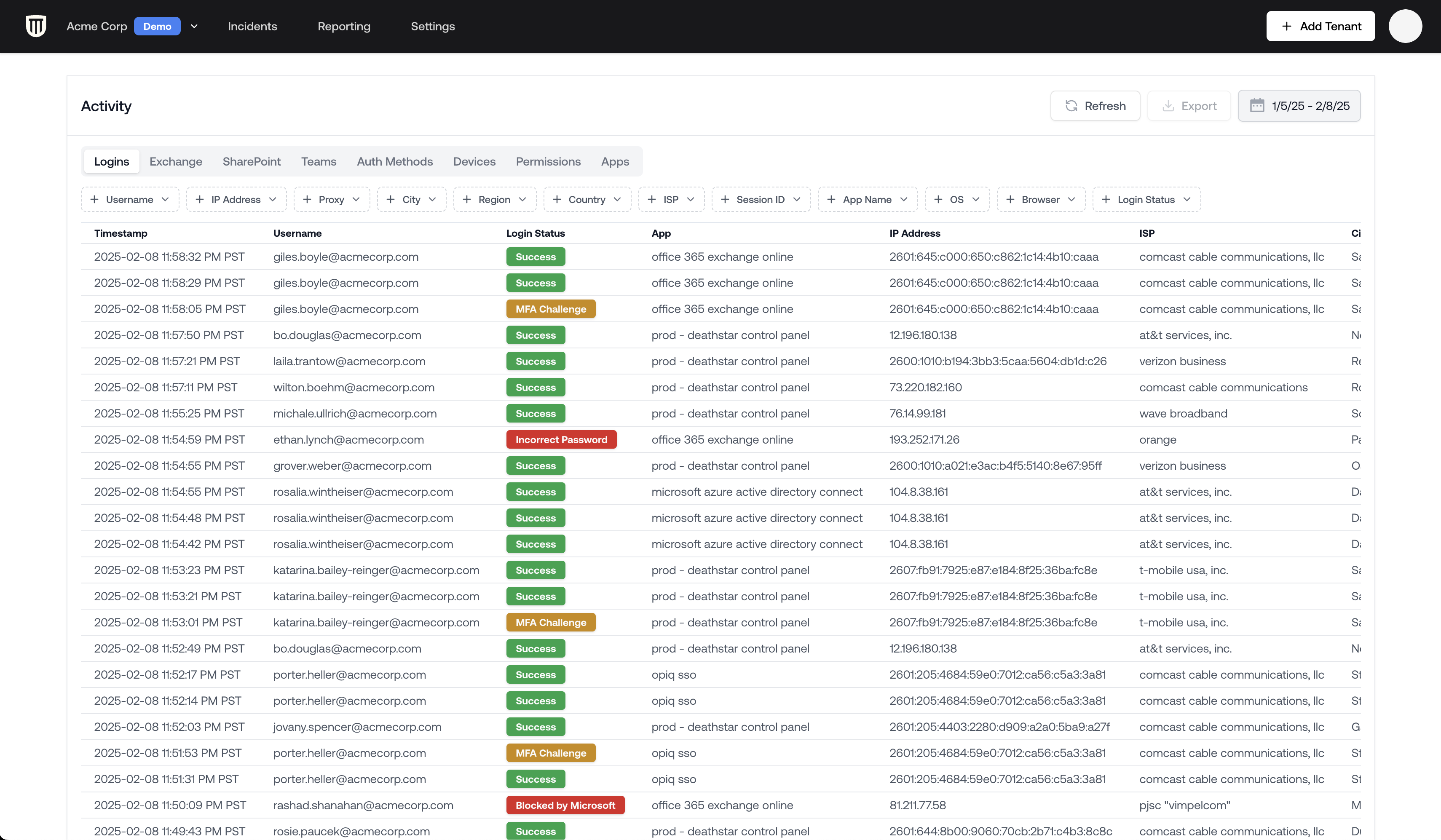
The Logs Viewer is always the best way to investigate. It offers powerful filtering capabilities:Filter by User
- Right-click on a username
- Select Include
- This applies a username filter to all logs
Filter by ISP or Proxy Type
You can exclude specific ISPs (like Cloudflare) to focus on other proxy types:- Right-click on the ISP field
- Select Exclude
- This removes entries from that specific provider