Why Monitor Non-United States Activity?
Your clients and your employees probably see red flags from activity originating outside the US. While this isn’t always the case, it can make valuable collateral for clients and stakeholders. Petra makes it easy to investigate activity coming from outside the US.Method 1: Using the Reporting Tab
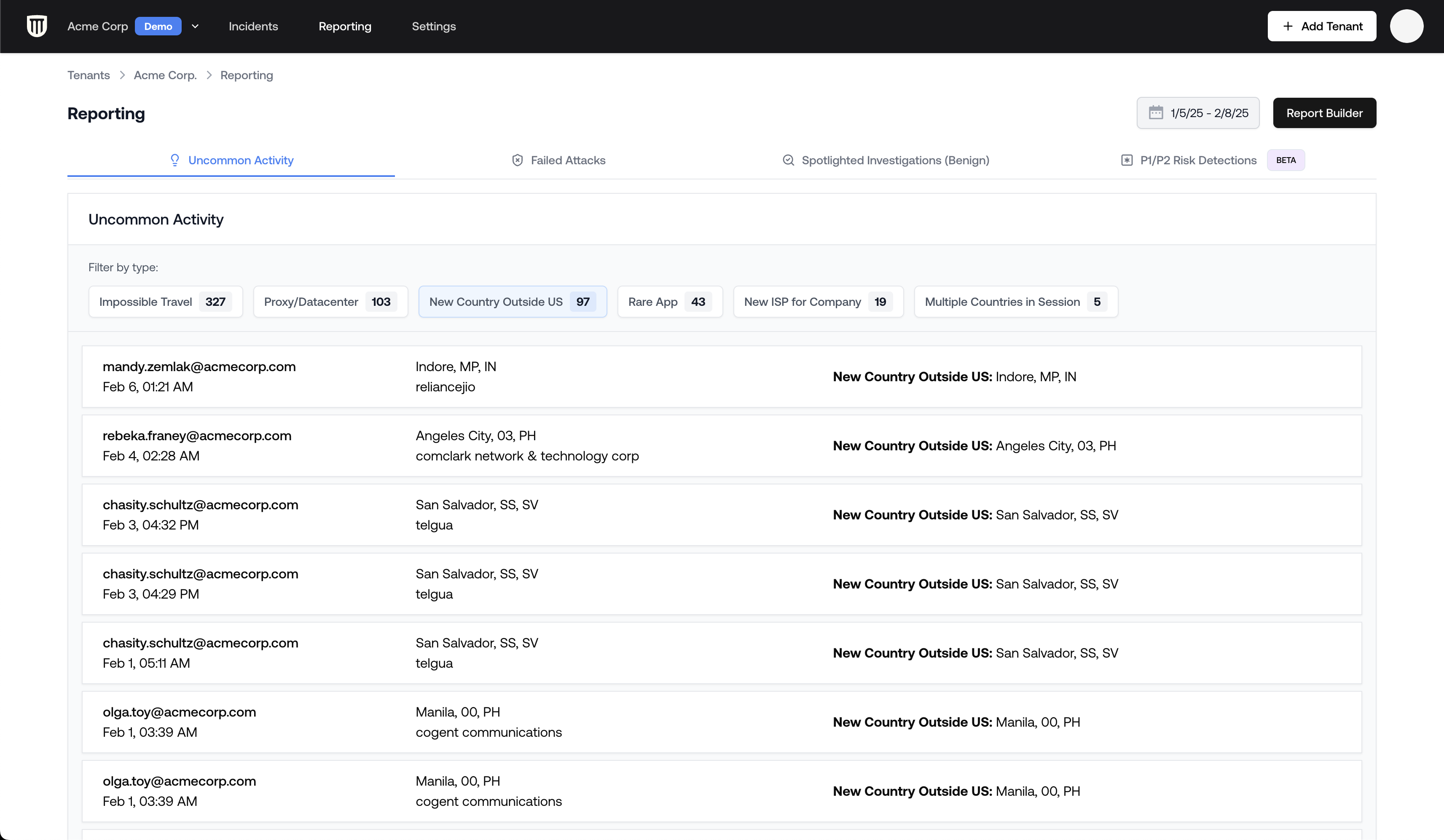
The Reporting tab offers a streamlined view of non-US activity:- Navigate to the Reporting tab in the top navigation bar
- Select the Uncommon Activity tab
- Click on New country outside the US to filter the results
- Each listed user is clickable for deeper investigation
- The complete user profile
- Specific log entries associated with their non-US login
- Detailed information about the activity location
This activity-specific view includes the user information up top, then the specific relevant logs
highlighted in yellow. The logs viewer beneath is fully functional so that you can apply
additional filters and further investigate.
Method 2: Using the Logs Viewer
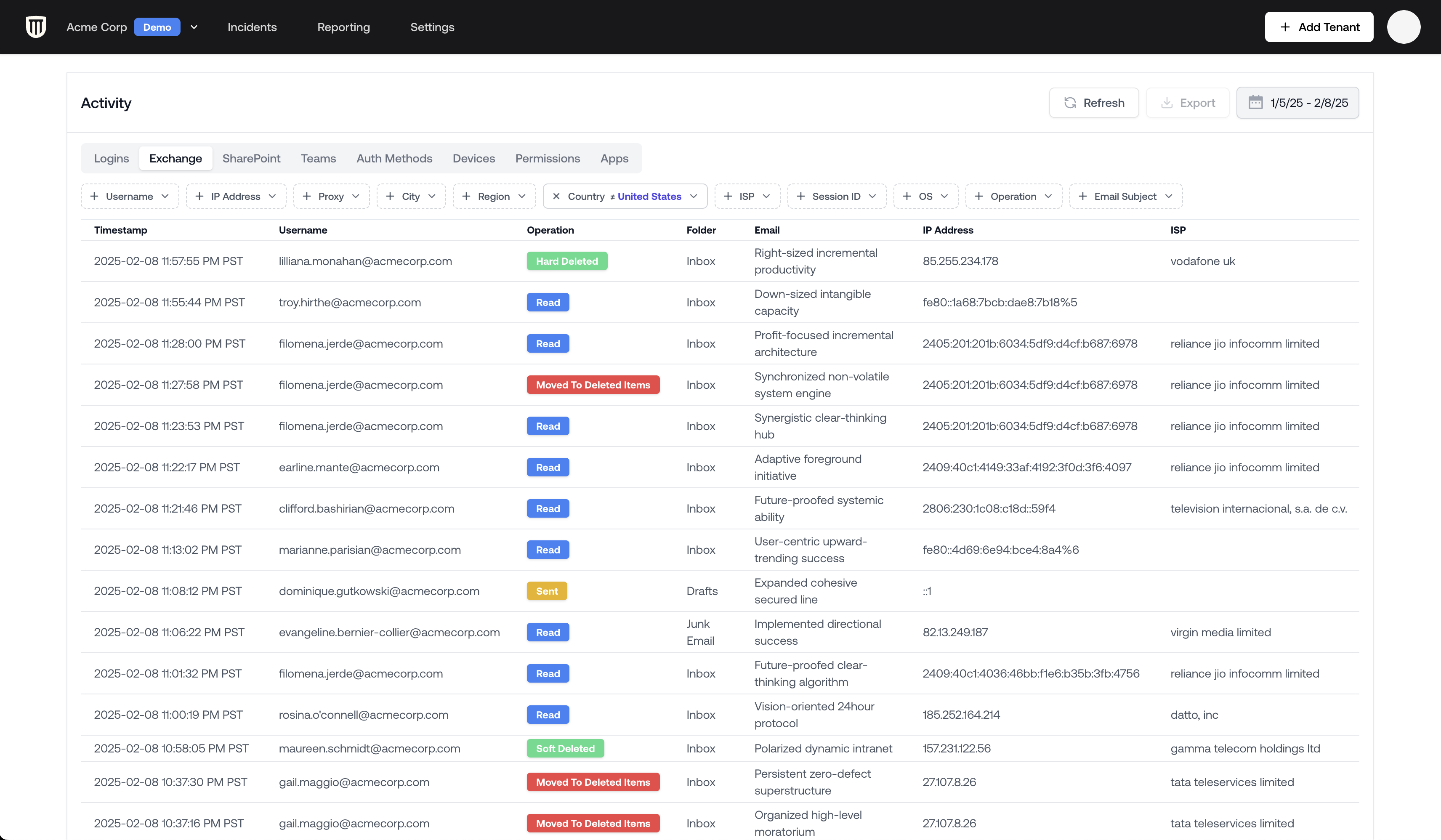
Logs viewers can be found all over Petra. Any one of them will allow you to search for activity coming from outside the United States.- Navigate to the tenant page (via the top left corner navigation)
- Scroll down to the Activity section
- Use the filter option to select not in: United States
Filter Out Failed Attacks/Blocked Activity
To focus on actual user behavior rather than blocked attacks:- Apply an additional filter for successful logins only
- Review the list of legitimate users accessing from non-US locations
- Select a specific user to investigate their pattern of activity
- Filtering for specific applications (Exchange, SharePoint, Teams)
- Examining the timing and frequency of access
- Checking for consistent patterns that may indicate legitimate travel versus suspicious activity
The logs view preserves the username of the user you’re investigating as you add more filters and
switch between Logins, Exchange activity, SharePoint activity, and more.
Navigation Tips
- Tenant Selection: Use the dropdown in the top left corner to switch between tenants
- Home: Click the Petra logo in the top left to return to the home page
- Tenant Activity: Access a specific tenant’s activity panel from the home page by clicking on a tenant in the list