Overview
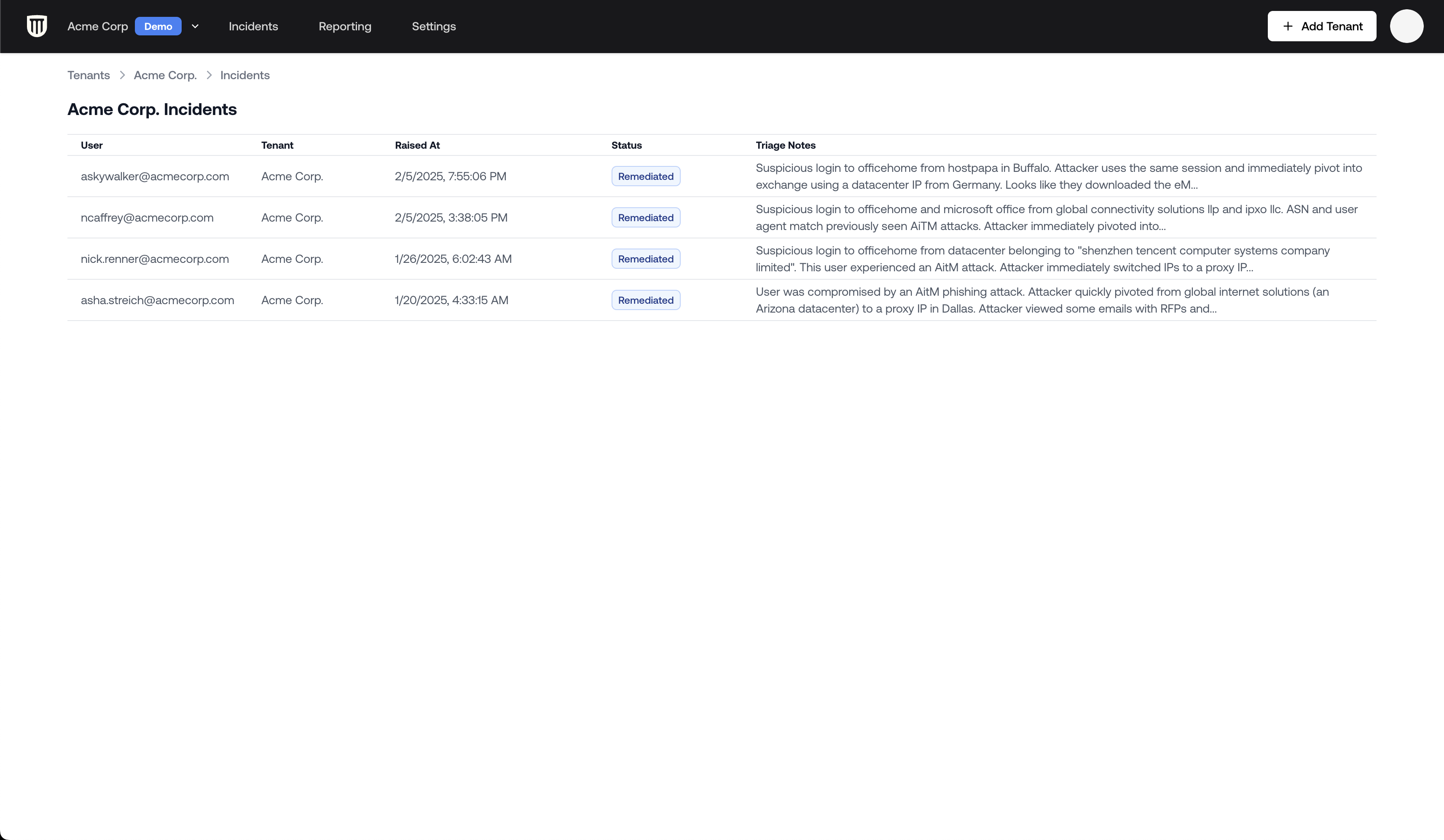
When an account compromise occurs, it’s critical to understand exactly what the attacker did. Petra Security provides comprehensive visibility into attacker actions through the incident page. This guide walks you through how to investigate attacker activities within a compromised account.Finding an Incident Page
- Navigate to the Incidents tab in the top navigation bar
- Click on a specific incident from the incidents list
- You’ll be taken to the detailed incident page for the compromised account
Understanding the Incident Page
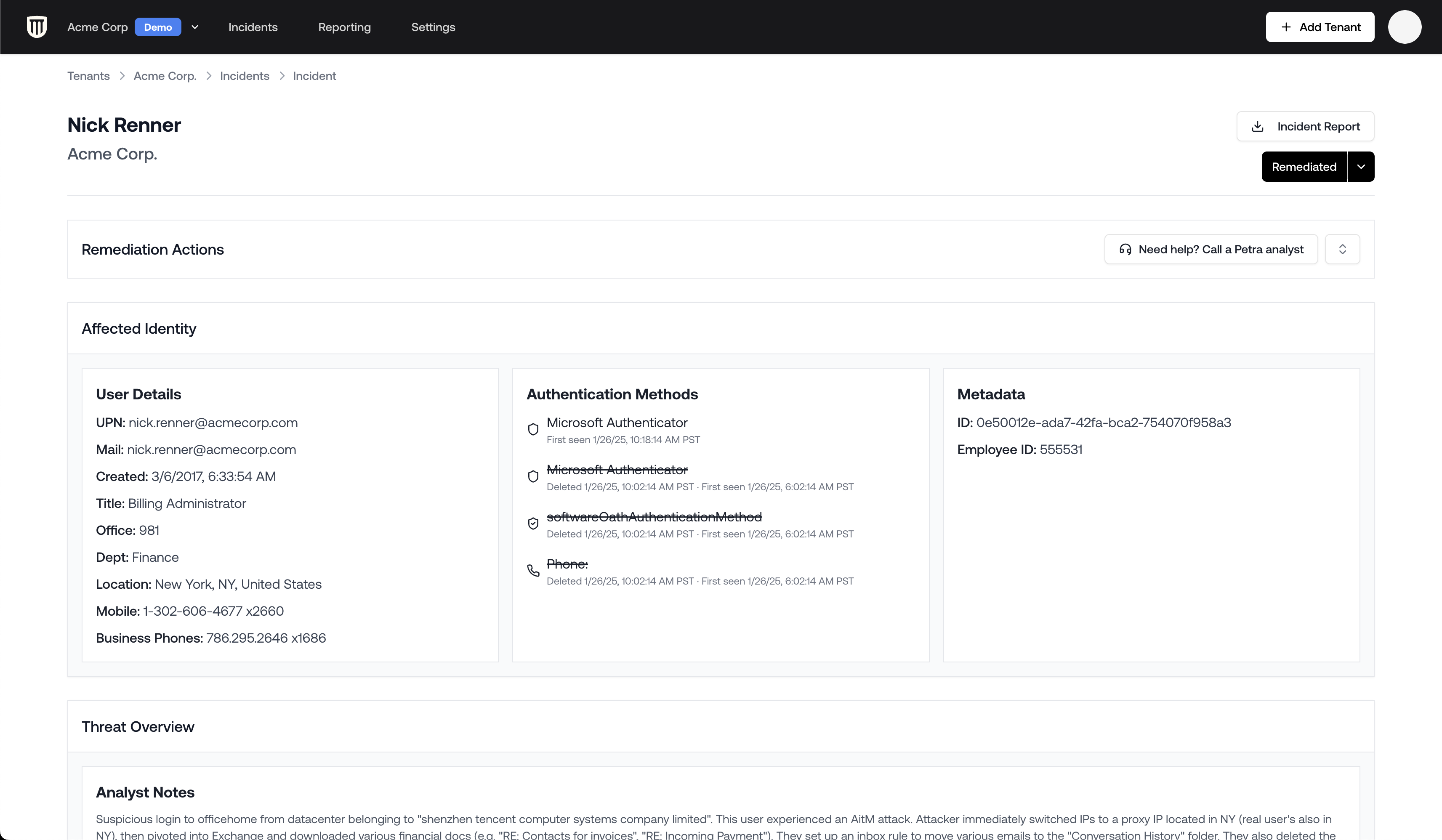
The incident page contains:- Compromised user information (top)
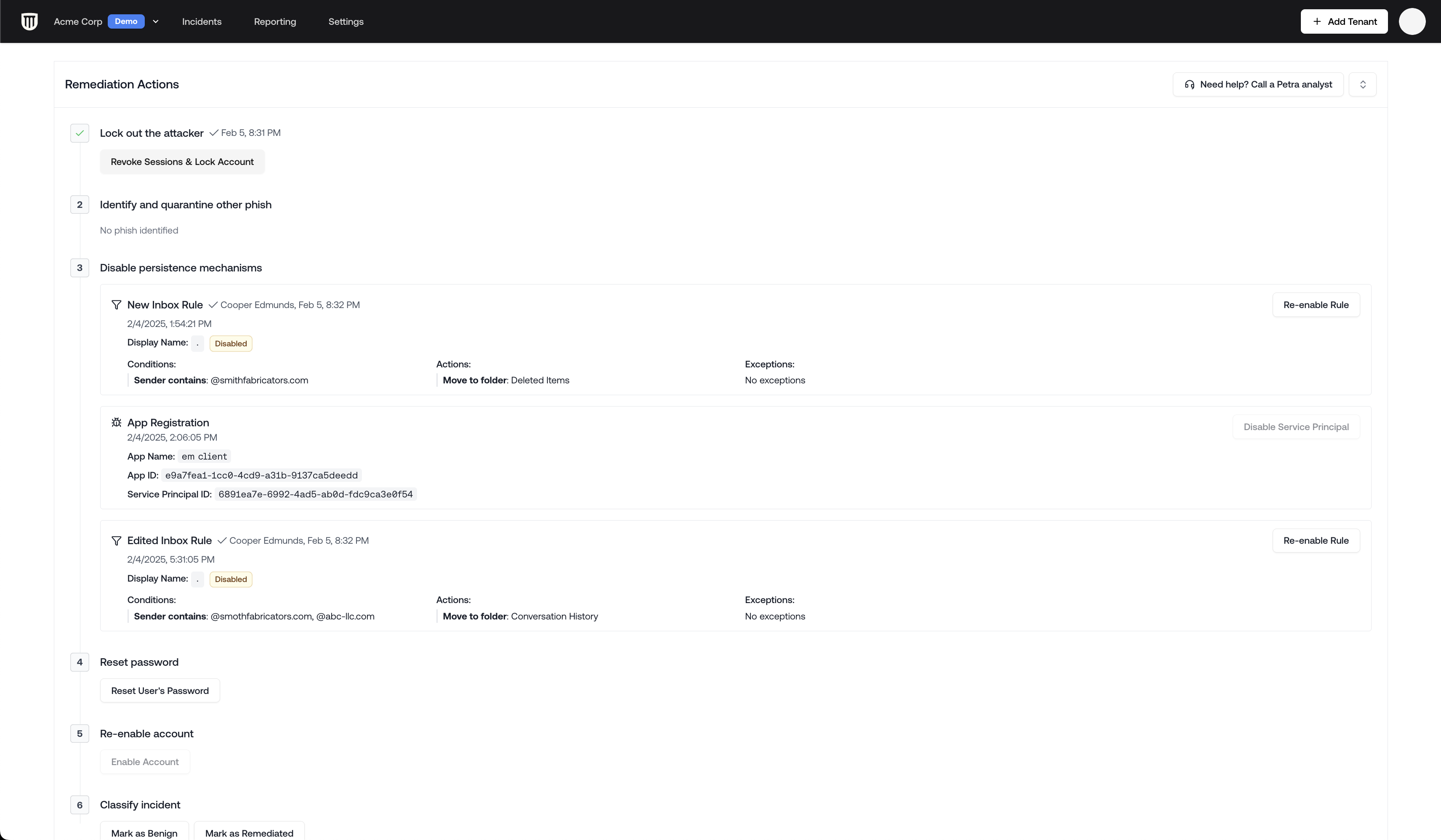
- Remediation actions panel
- Information about the affected identity
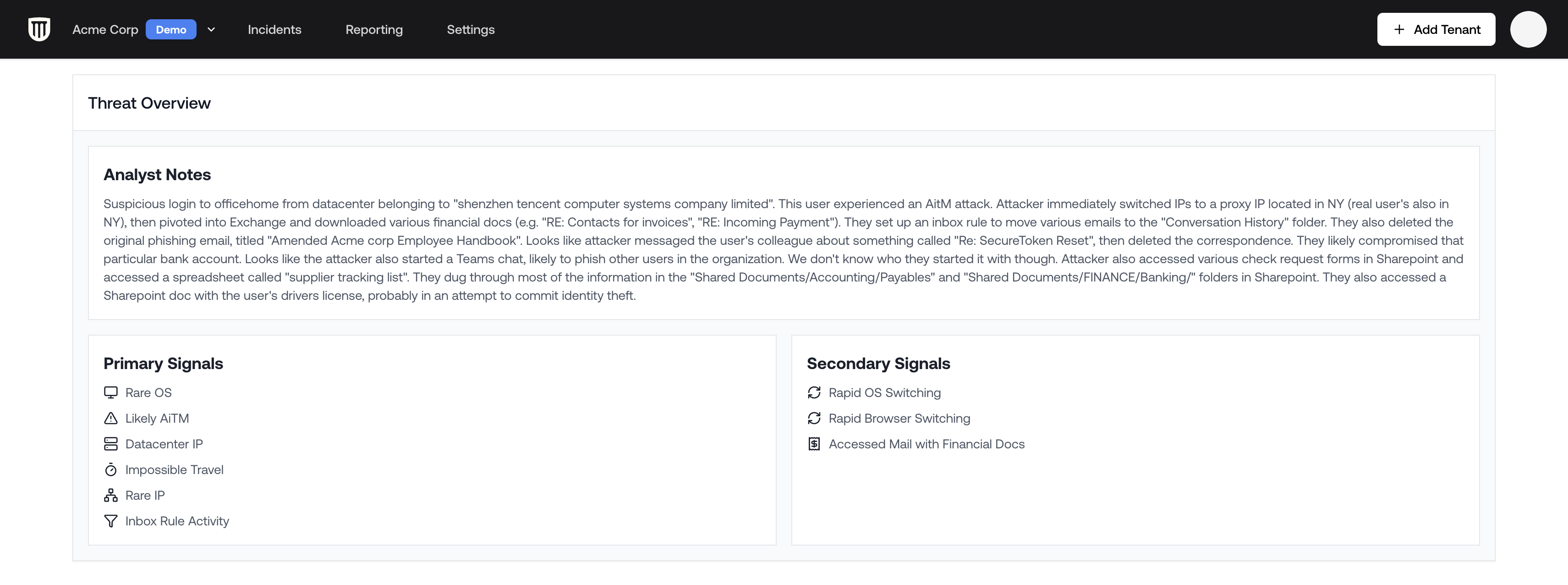
- Threat overview (how the compromise was detected)
- Attack timeline
- Activity logs viewer

Viewing Attacker Actions
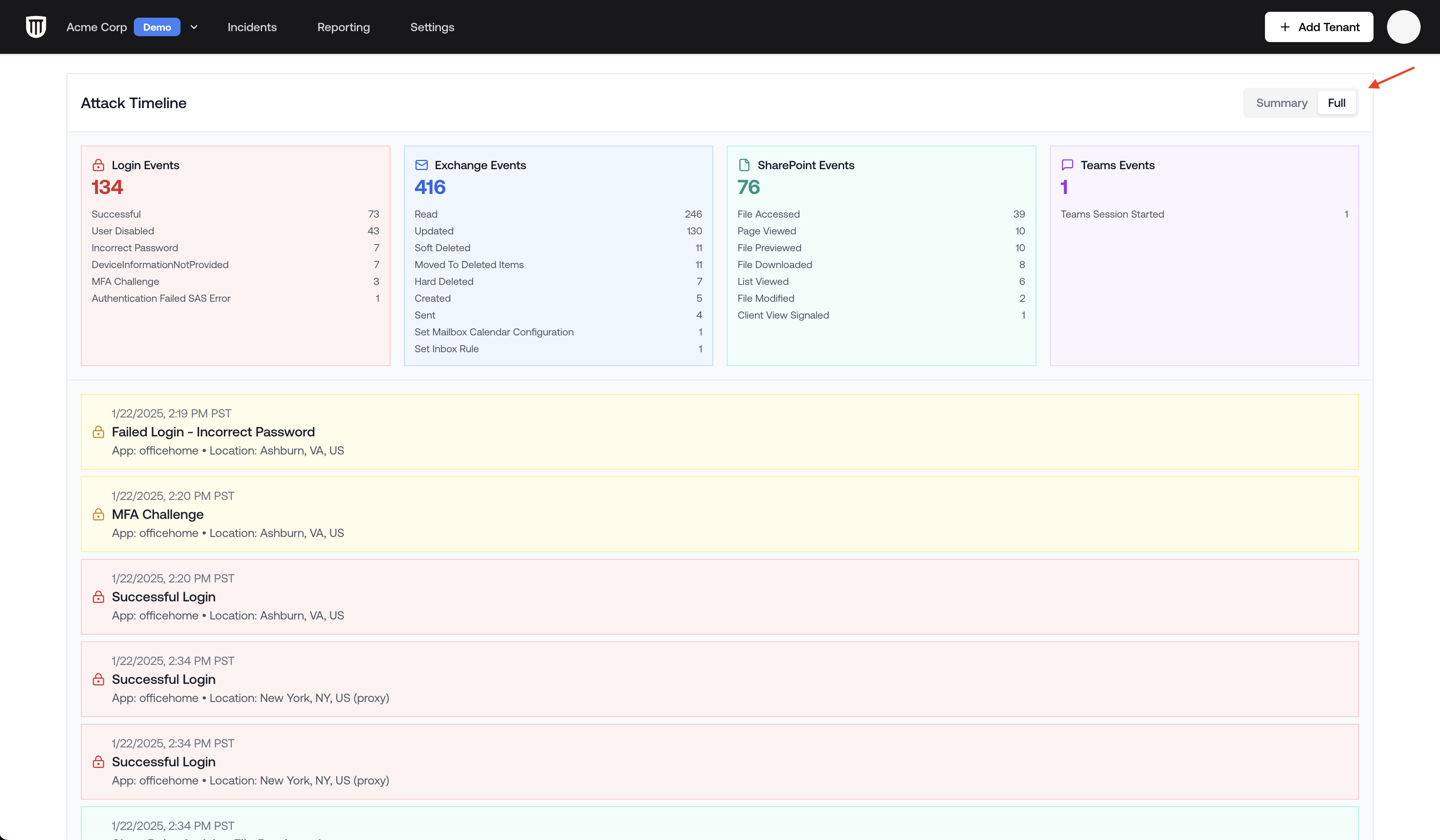
There are two primary ways to see what an attacker did when inside a compromised account:1. Attack Timeline
The Attack Timeline provides a chronological view of attacker activities:- Summary View: Shows general types of actions the attacker performed, categorized by service (login events, Exchange events, SharePoint events, Teams events)
- Full View: Displays detailed step-by-step, timestamp-by-timestamp actions, including specific files accessed
Toggle between Summary and Full views using the selector in the Attack Timeline section.

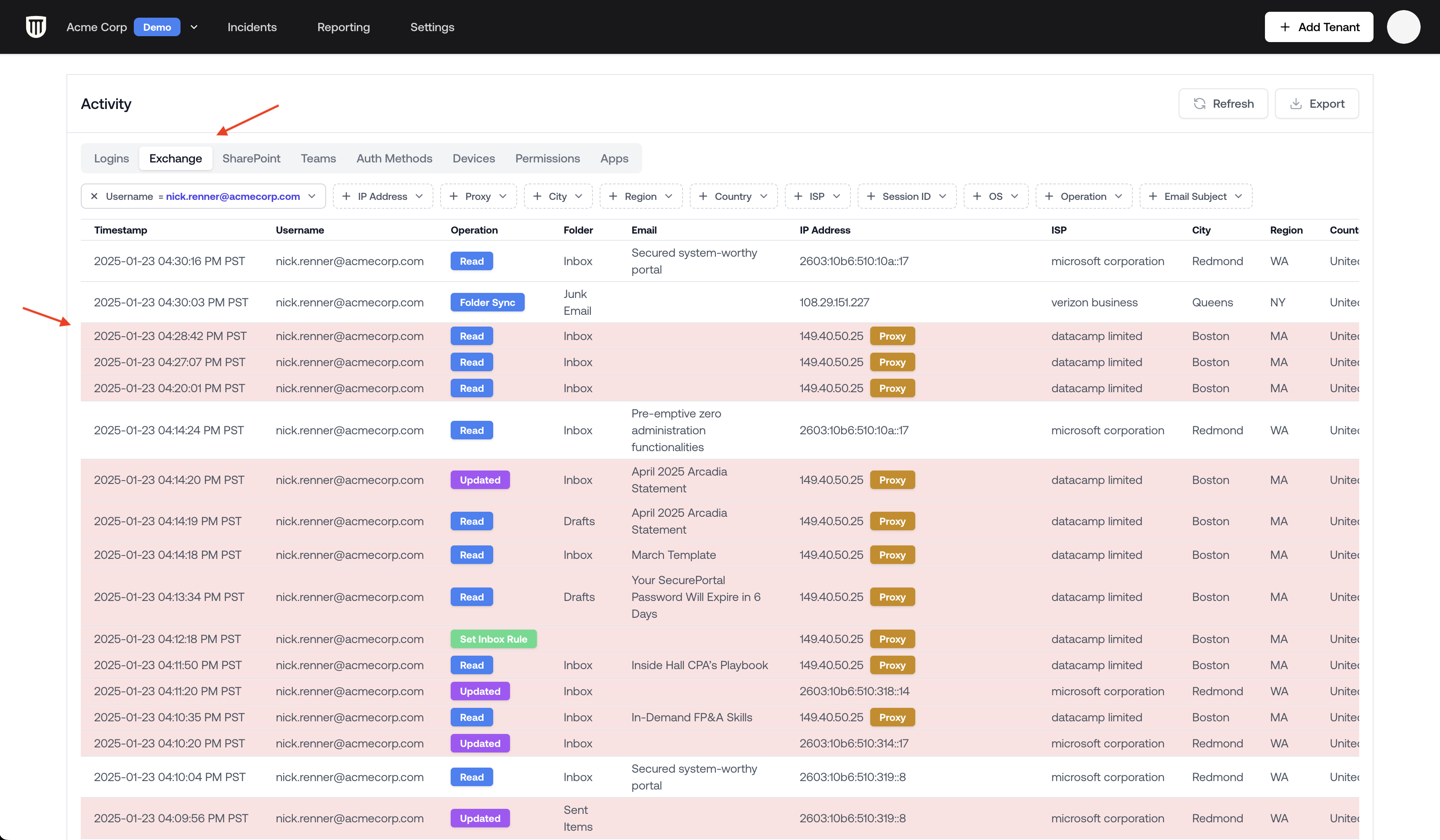
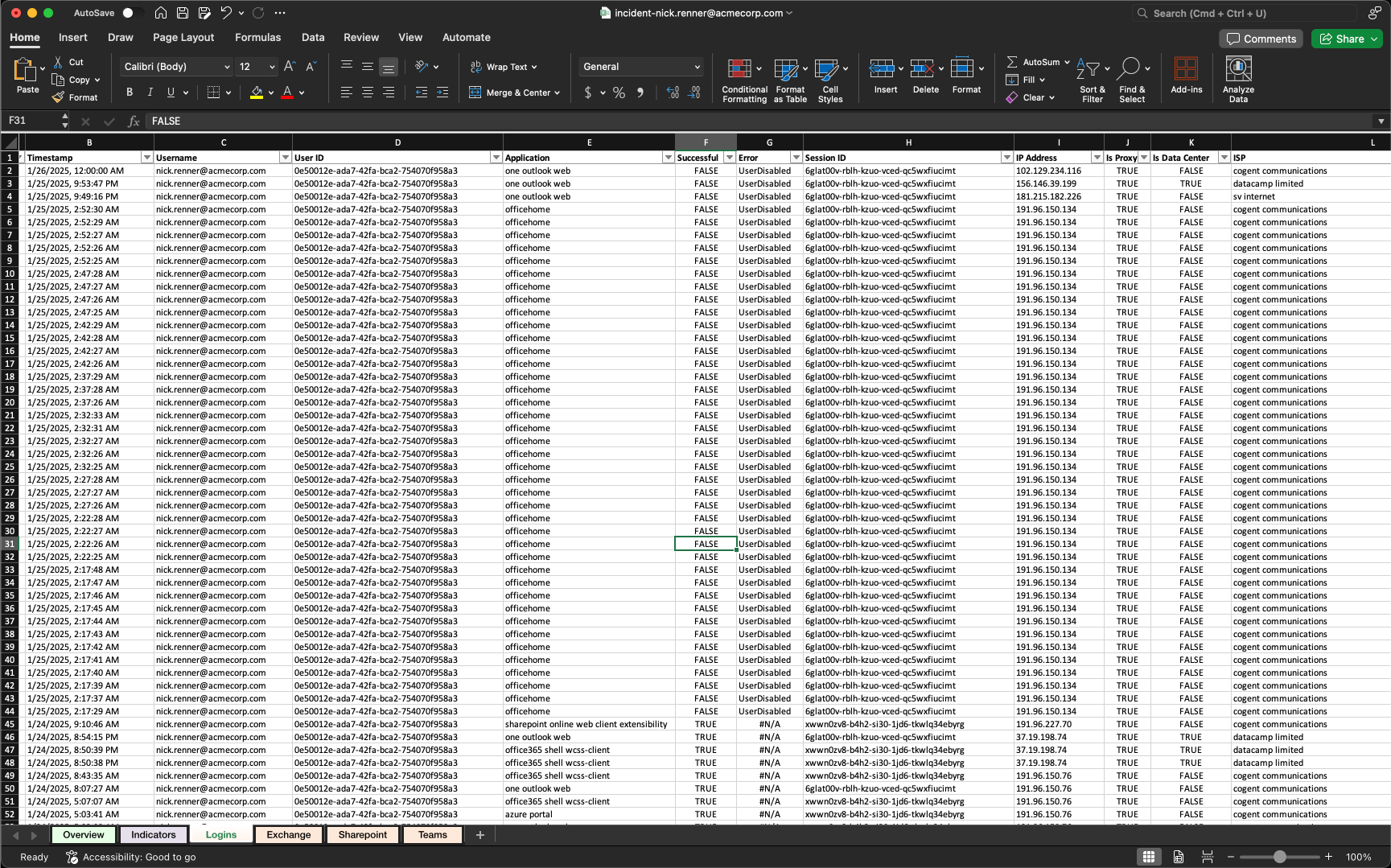
2. Logs Viewer
The Logs Viewer provides deeper insights into specific activities across different services:- Available Tabs:
- Logins
- Exchange
- SharePoint
- Teams
- Auth Methods
- Device Registrations
- App Permissions

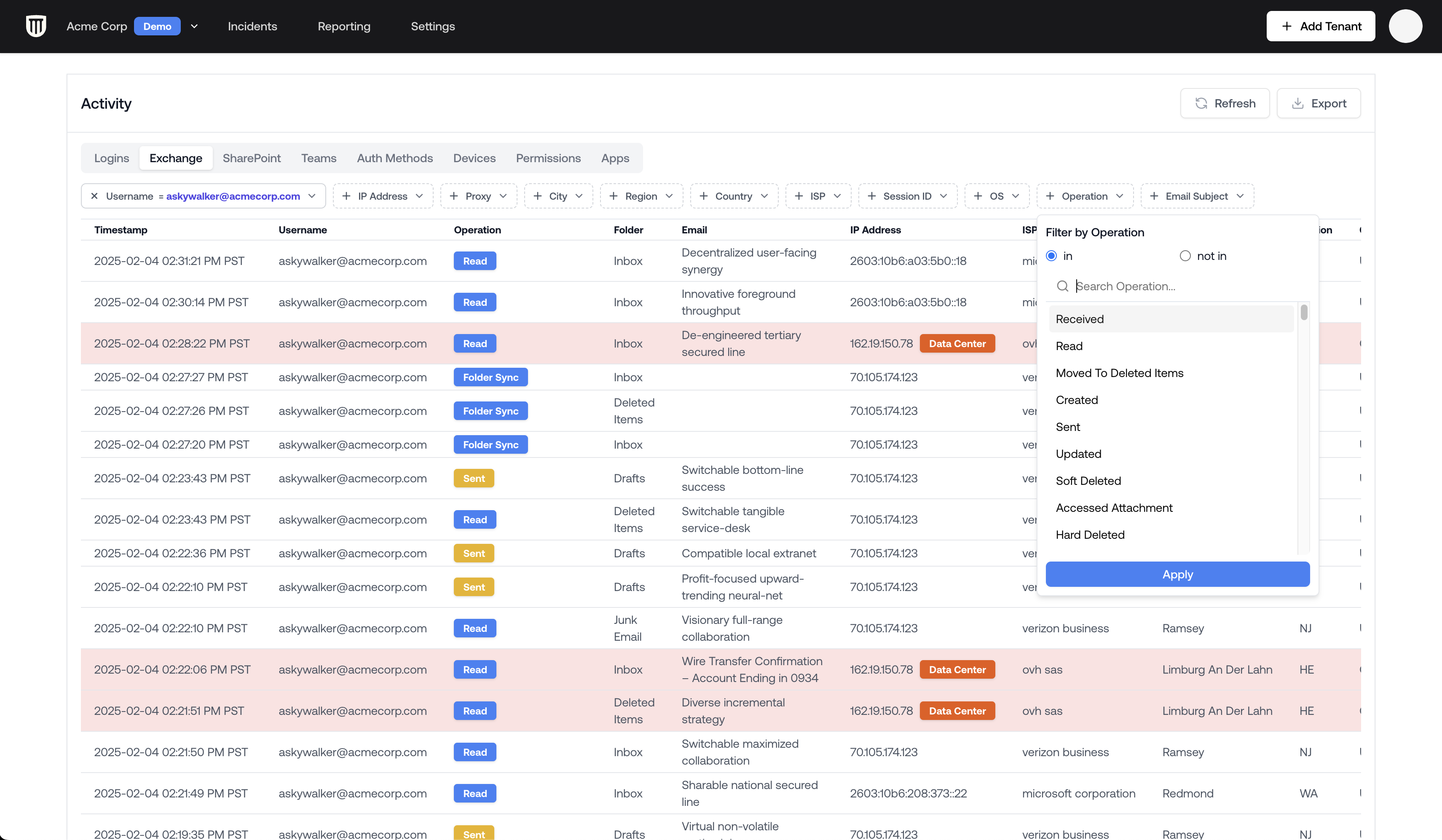
Filtering Exchange Activities
To focus on meaningful attacker actions in Exchange:- Navigate to the Exchange tab in the Logs Viewer
- Click on the Operation filter
- Select not in for “Read” and “Updated” events
- Apply the filter
- Deleted emails (soft deletes and moves to deleted items)
- Hard deleted items
- Sent items - particularly important as these represent external communications from the attacker
Pay special attention to “Sent” and “Created” items as these often require additional remediation
actions. You can also click on an email to see all interactions with it by users across the
environment (e.g. who read/replied/forwarded/sent/received it).
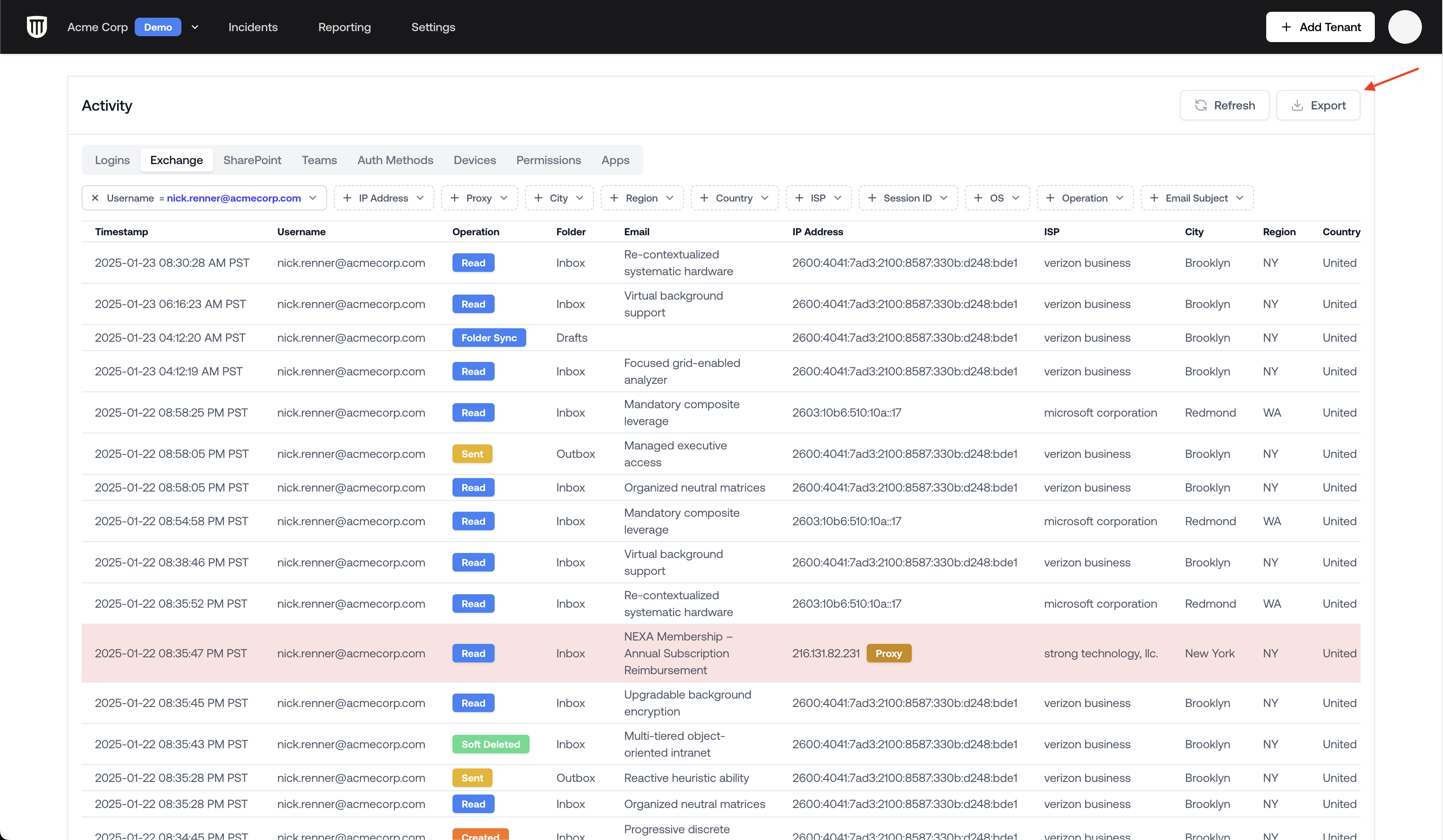
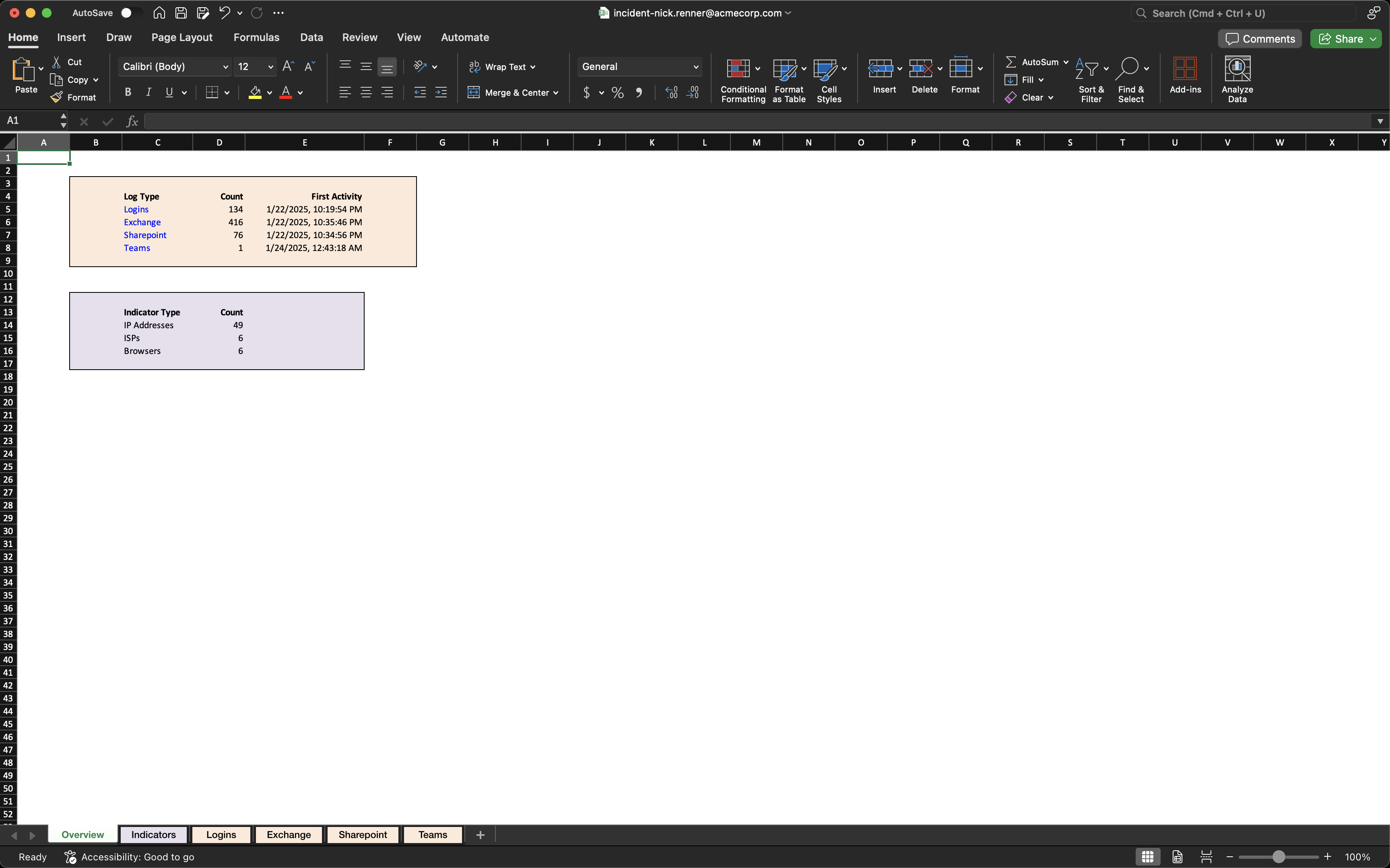
Exporting Activity Logs
For even deeper analysis or reporting:- Click the Export button at the top of the Logs Viewer
- Open the exported Excel document
- Navigate to the relevant tab (Exchange, SharePoint, etc.)
- Use Excel’s filtering capabilities for more granular analysis
Making the Most of Your Investigation
A few tips for your investigations:- Focus on Sent and Created events in Exchange. These often indicate external comms performed by the attacker that you likely want to remediate. They may also indicate data exfiltration. Most often, these are signs of trusted third party phishing and can be disastrous for both organizations involved if not remediated.
- Look for Hard Deleted and Soft Deleted events that might indicate an attacker’s attempts to cover their tracks. Attackers often try to delete their own phishing email or further phishing emails that they send. Note that Petra captures and preserves these deleted items.
- Pay close attention to external sharing or permission changes in SharePoint.
- Look for new malicious app installations and mail filter rules. These are also auto-highlighted in the Remediation Actions Panel.
Your clients will likely want to know if sensitive data was accessed or if any external
communications were sent from the compromised account. You can do that here.