January 23, 2026
The Autopsy Report
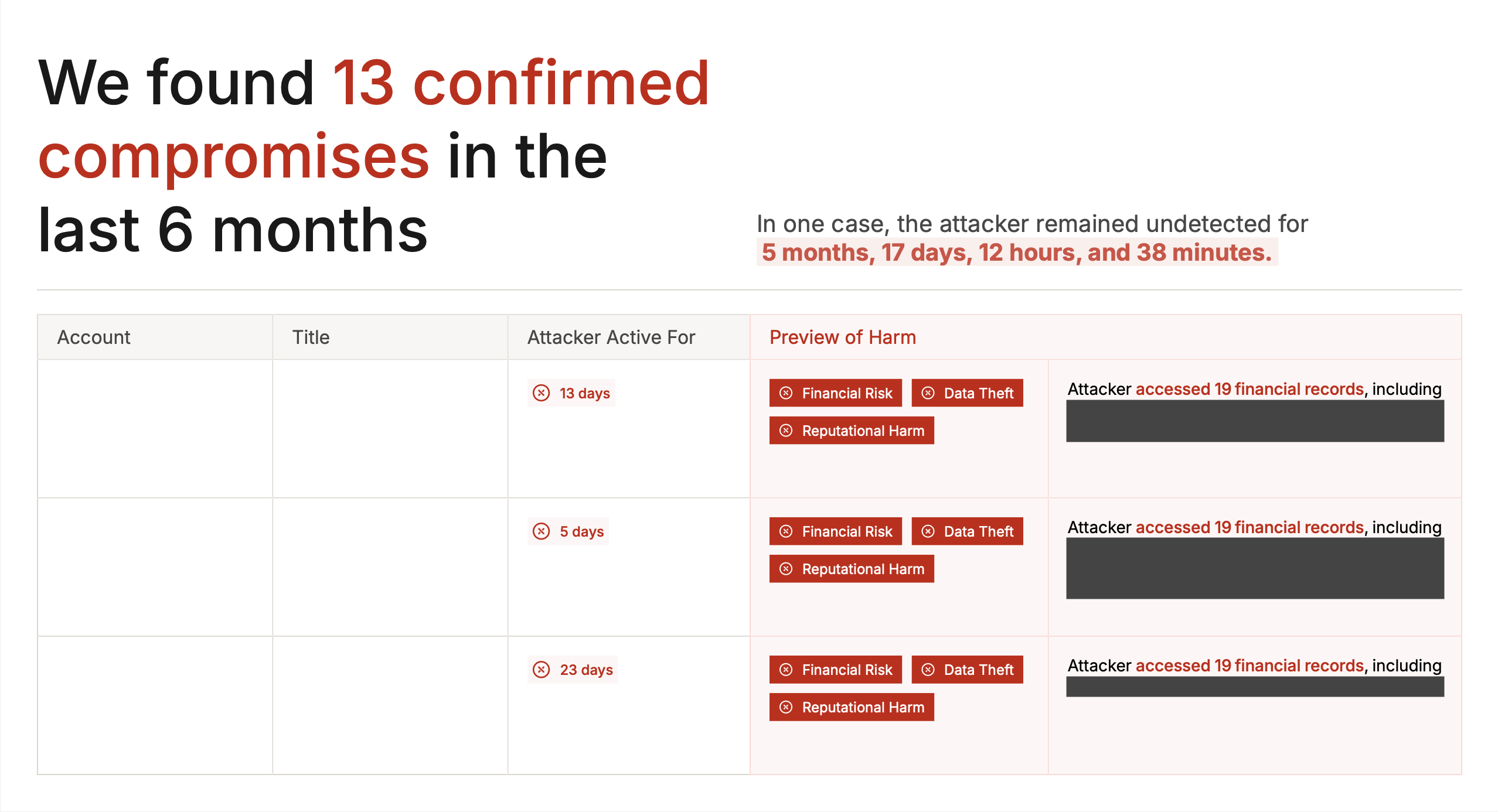
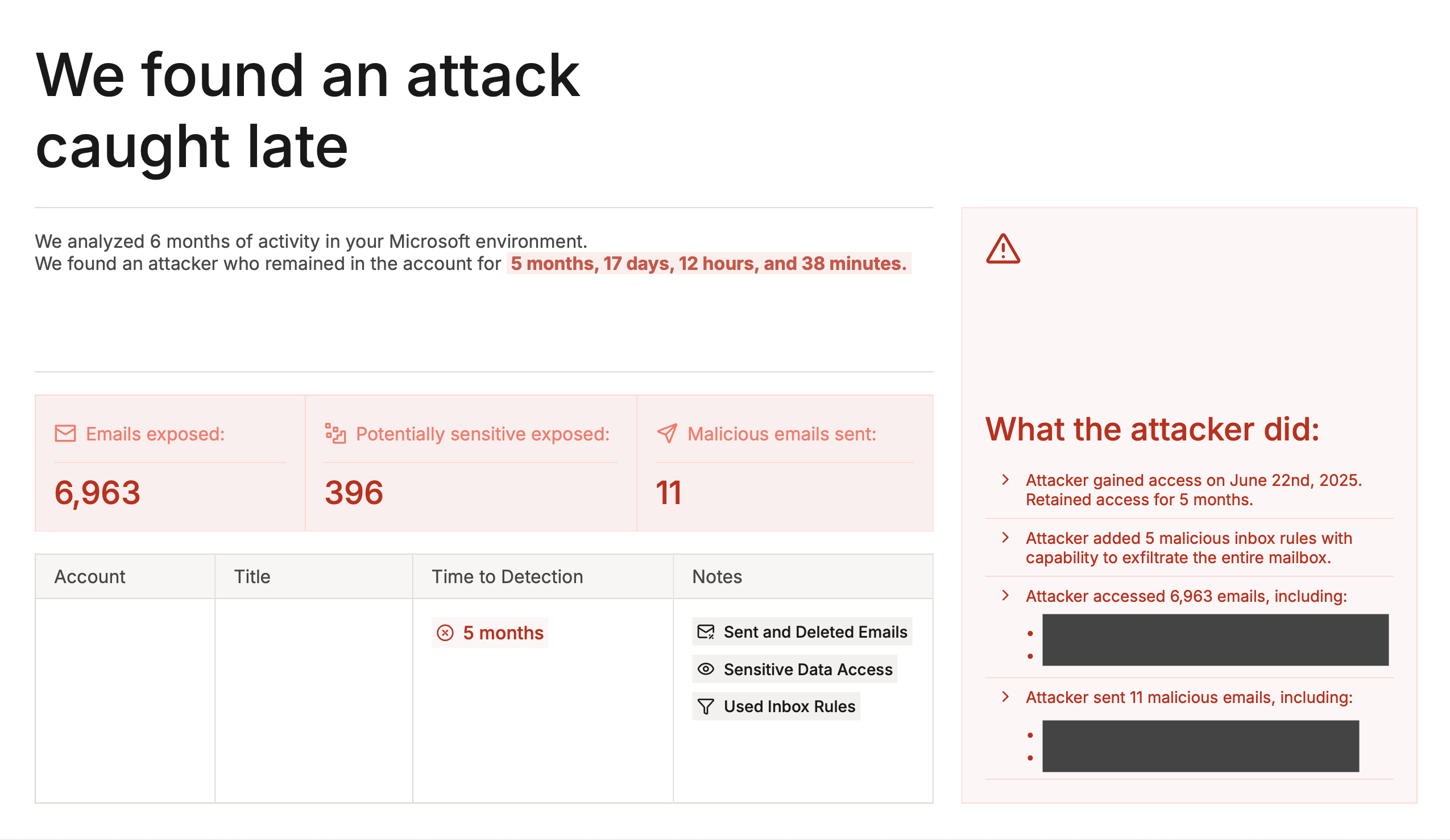
A Petra Autopsy investigates the last 6 months of a tenant’s activity to uncover attacks and compile forensics. Our new white-labeled Autopsy Report transforms 6 months of tenant forensics into a sales-ready document for your client meetings. We hope you use it to demonstrate real security gaps your clients didn’t know existed and make deploying Petra a no-brainer for your client.What it reveals:- Previously remediated compromises with deeper analysis
- Active attackers still in the account
- Gaps in existing ITDR solutions
Note: New MSPs receive a free Autopsy with their Petra trial.
January 16, 2026
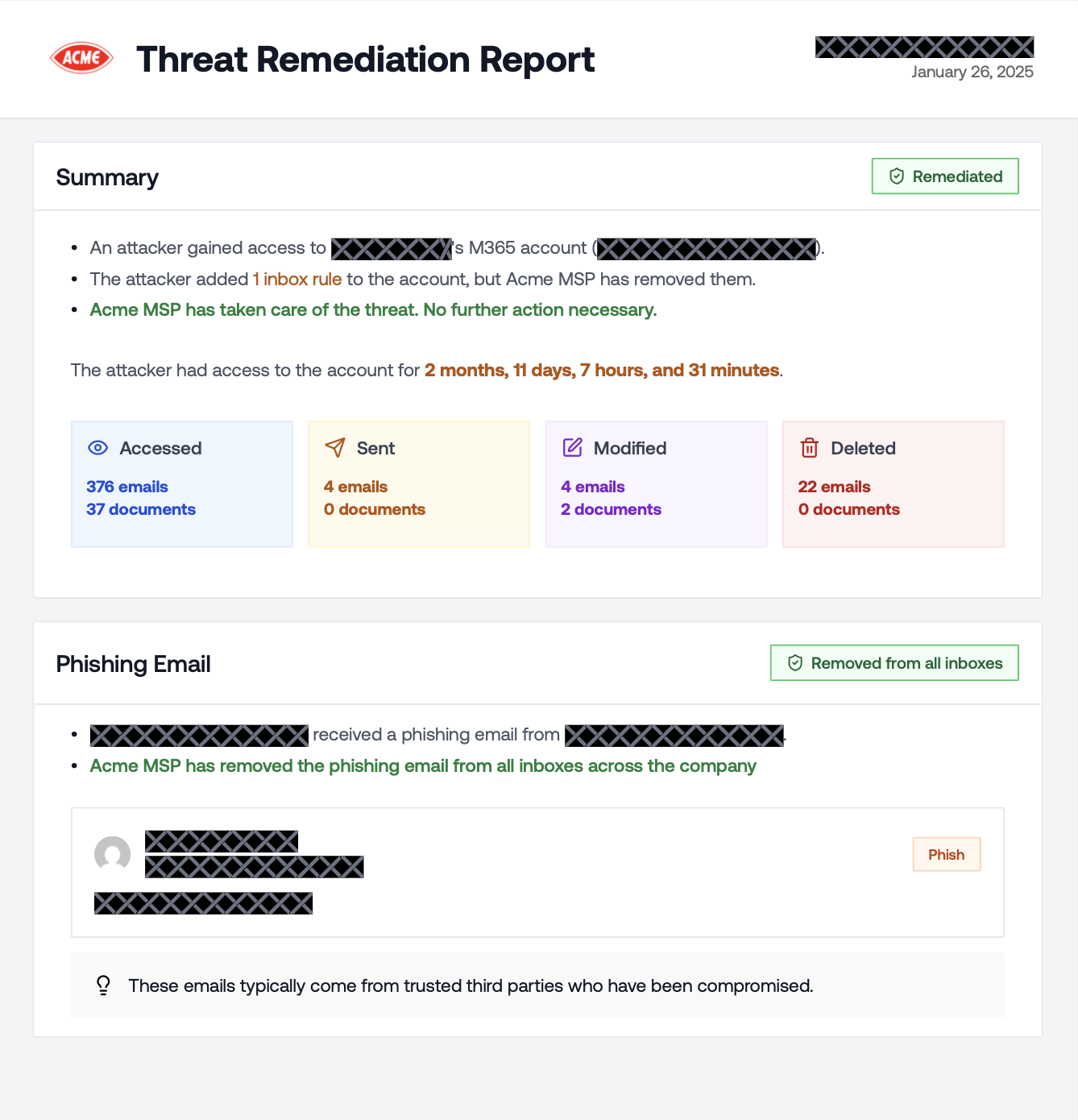
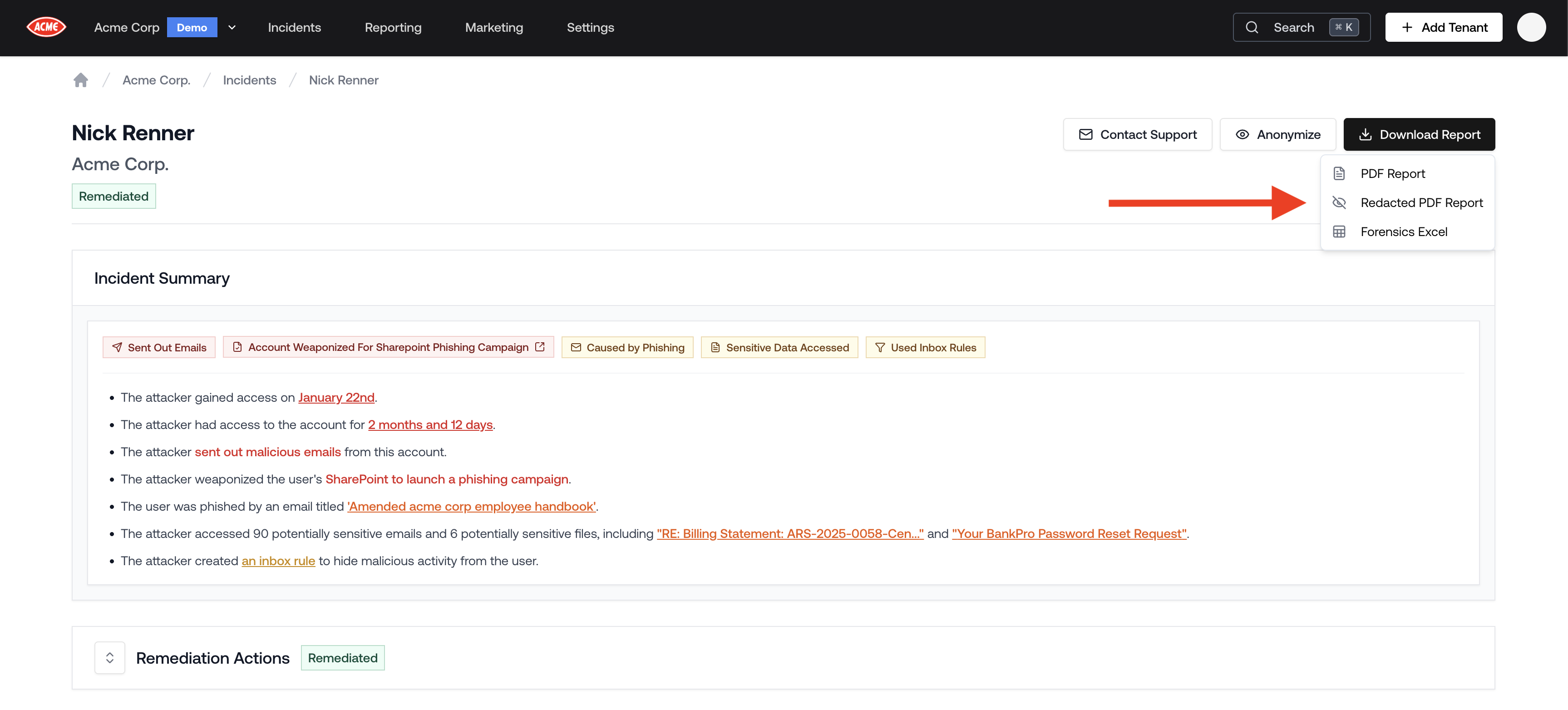
Redacted Incident PDF
Redacted Incident PDFs help you demonstrate real compromises in sales pitches while protecting client data. To download this report, navigate to an incident in the Petra dashboard, click “Download Report”, and select “Redacted PDF Report” in the dropdown.Reminder: When sharing your screen to showcase incidents to other clients, you can redact PII by clicking the Anonymize button on the top right of the Incident page.
Analyst Summary in the Incidents List
The list of previous incidents now includes a detailed Analyst Summary section, making it easier to distinguish between incidents. This helps you select a more compelling and diverse set of previous compromises when engaging prospective clients.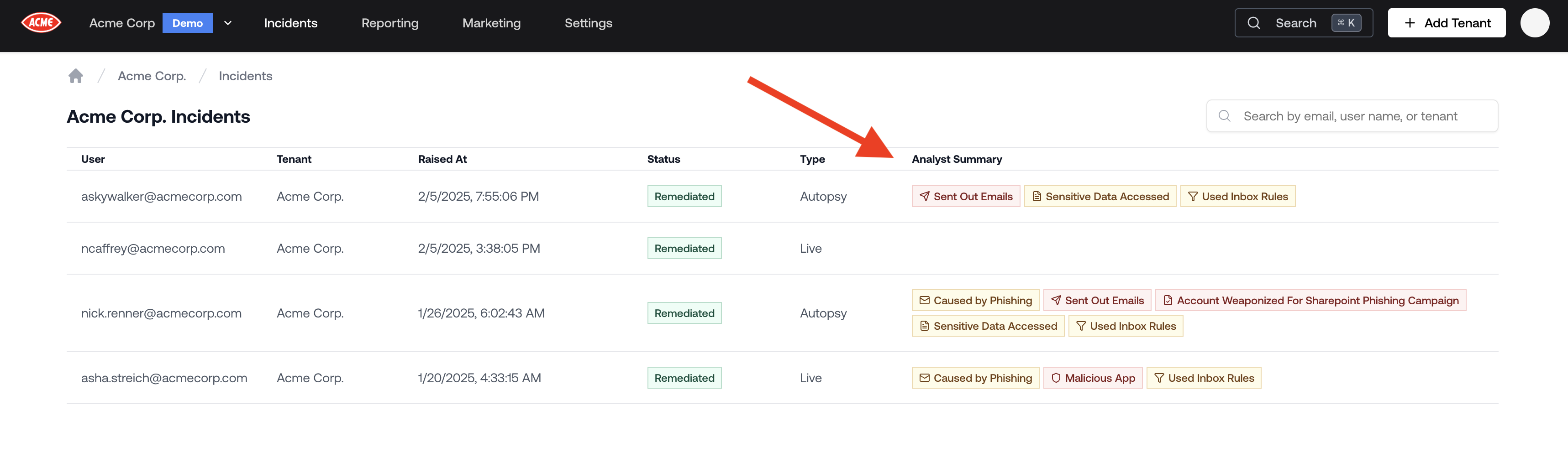
January 9, 2026
Incident Summary
Now the incident page has an “Incident Summary” section which succinctly highlights the most important details of the attack. This enables account managers and salespeople to tell a clear story of the attack, rather than overwhelm the client or prospect with information.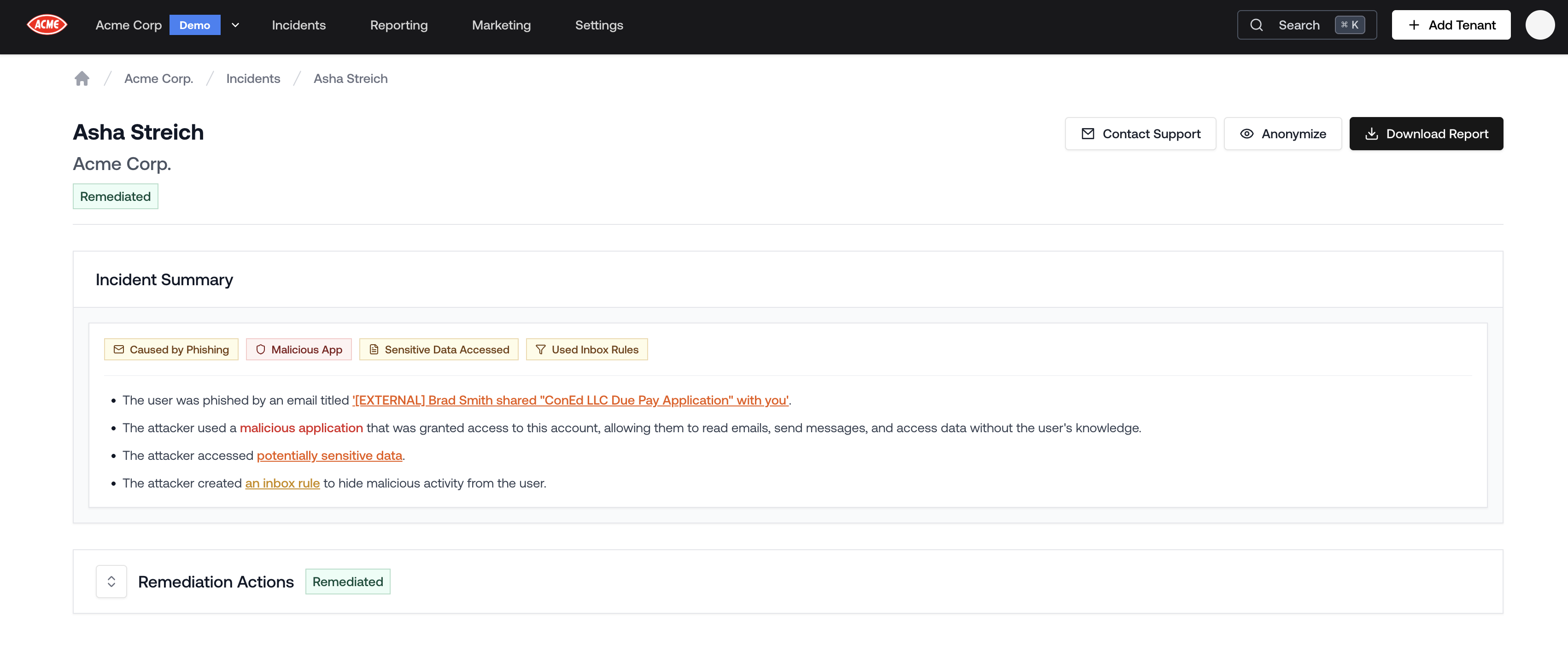
Tenant Onboarding Tracker
When adding new tenants, you’ll now see a streamlined onboarding tracker that displays real-time status updates. This gives you clearer visibility into each tenant’s onboarding progress and lets you anticipate exactly when they’ll be fully set up.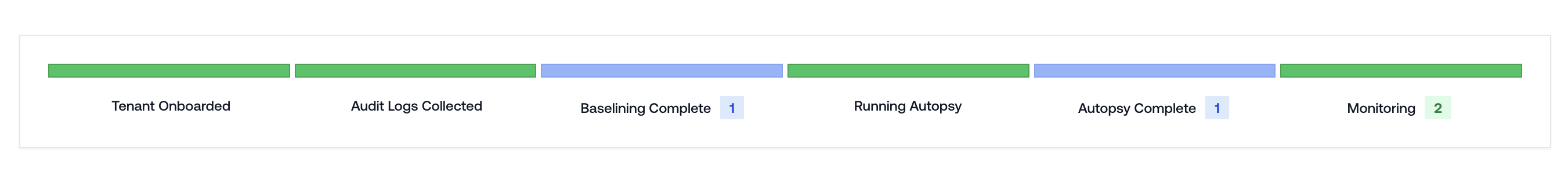
December 19, 2025
Tenant Report Redesign
The Tenant Report has been redesigned! We’ve listened to your feedback and added the most requested features and improvements. Go check out the new Report Generator.Reminder: You can configure automatic sending of Tenant Reports at the end of every month by going to Settings and adding your organization’s emails in the “Automated Monthly Reports (Internal emails only)” section.
December 12, 2025
Anonymize Incidents
You can now anonymize an incident to help you show any quickly caught incident as a victory lap, and any Autopsy as a cautionary tale. Go to an incident page, click the Anonymize button on the top right, and select which information should be hidden.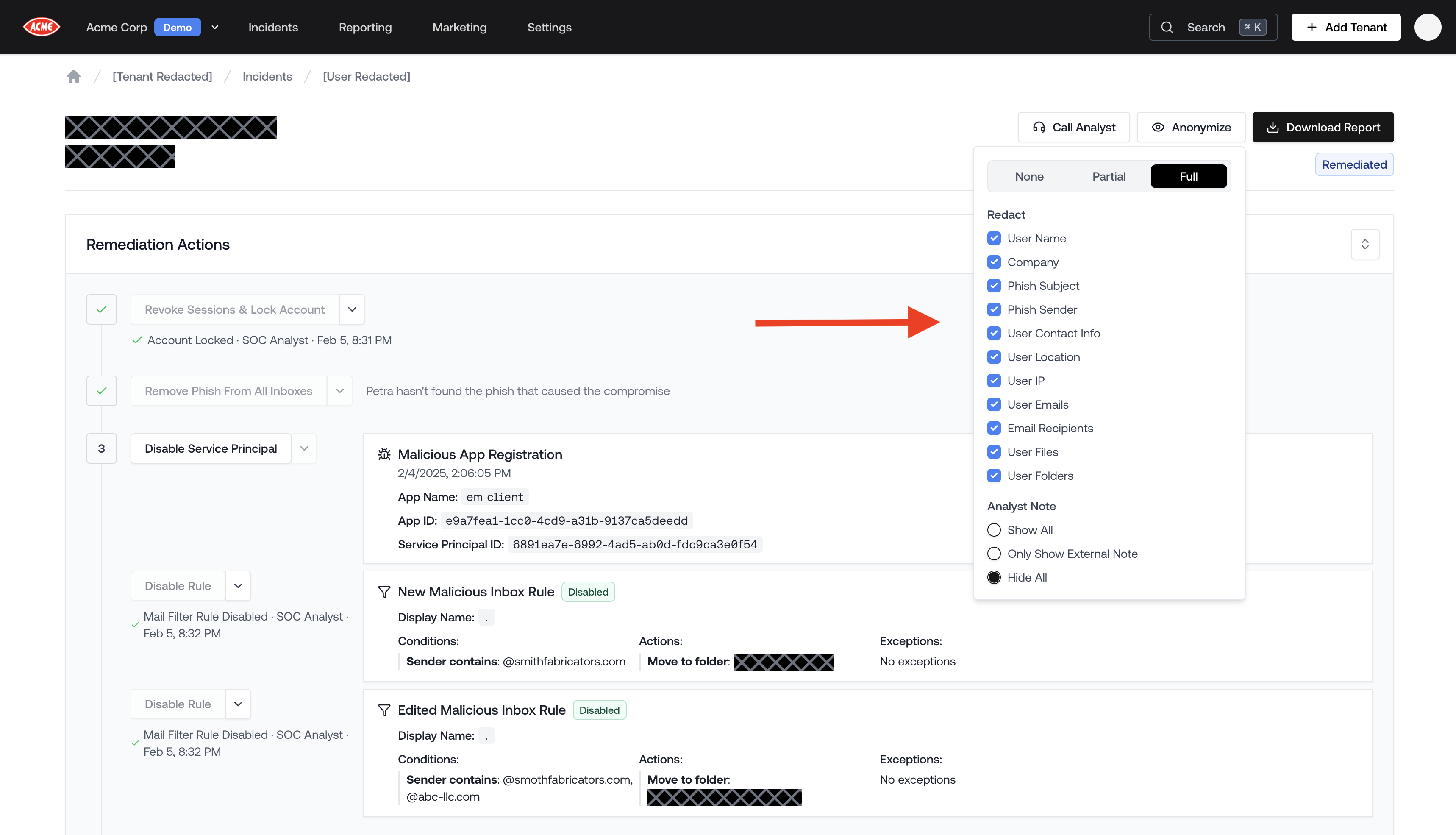
December 5, 2025
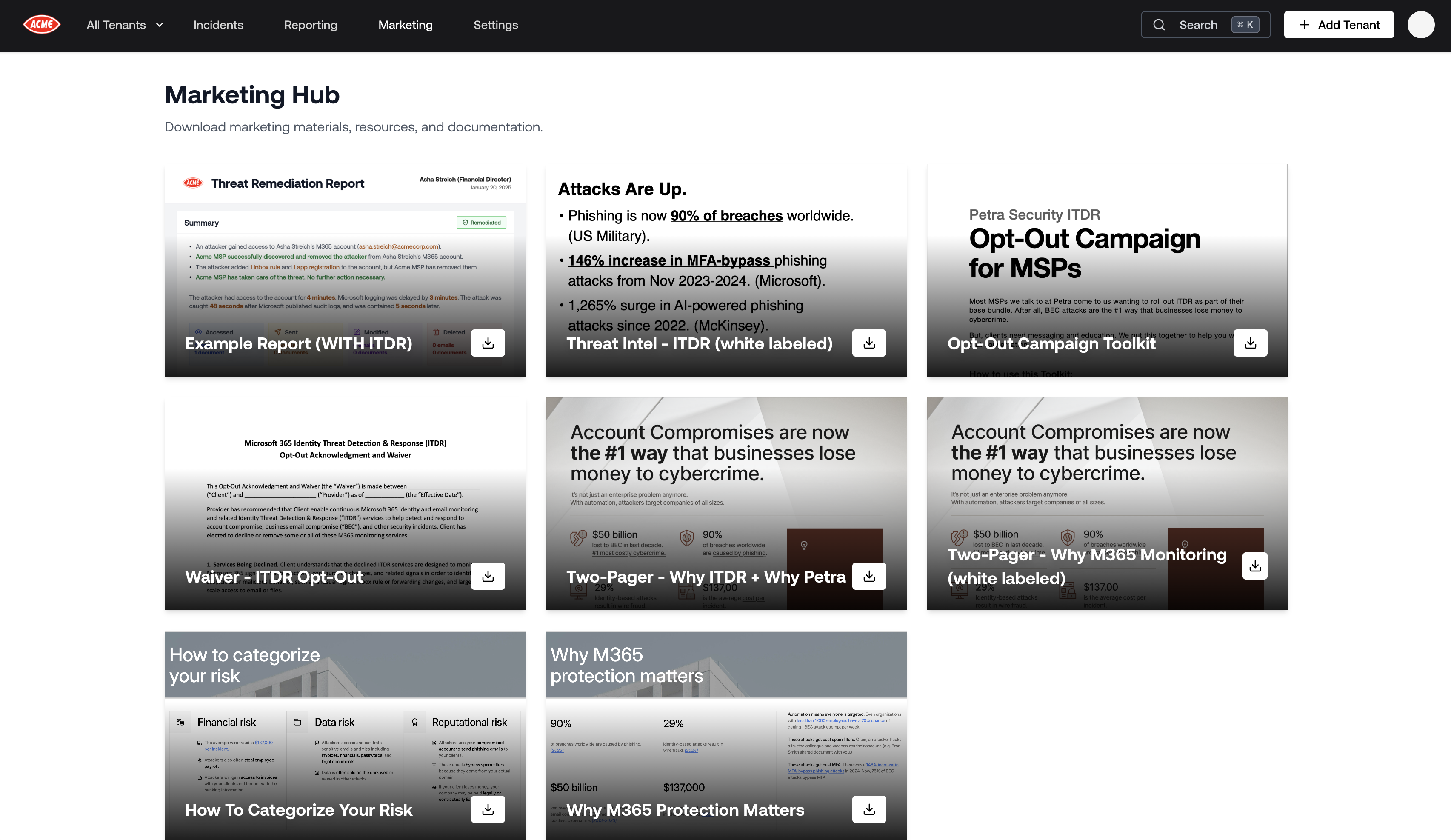
The Marketing Hub
The Marketing Hub offers a collection of documents, slides, and waivers that are meant to help you share the value of Petra ITDR with your clients. Navigate here by clicking the “Marketing” tab in the navbar or by clicking here.Today, the Marking Hub offers the following resources:- Example Report (with ITDR): Sample security report showcasing enhanced detection capabilities with Petra ITDR
- Threat Intel - ITDR (white labeled): White-label ready threat intelligence presentation on ITDR capabilities and insights
- Opt-Out Campaign Toolkit: Documentation and guide for the Petra opt-out campaign toolkit and resources
- Waiver - ITDR Opt-Out: Opt-out waiver document for ITDR services and related terms
- Two-Pager - Why ITDR + Why Petra: Two-page overview document highlighting Petra ITDR capabilities
- Two-Pager - Why M365 Monitoring (white labeled): Two-page overview document highlighting general M365 ITDR capabilities
- How To Categorize Your Risk: Presentation slide providing guidance on categorizing and assessing security risks
- Why M365 Protection Matters: Presentation slide explaining the importance of Microsoft 365 security protection
November 28, 2025
View Tenant-Wide MFA Enforcement
You can now see whether MFA is enforced for every user in a tenant directly from the tenant homepage. Both legacy MFA methods and enforcement through Conditional Access Policies are shown.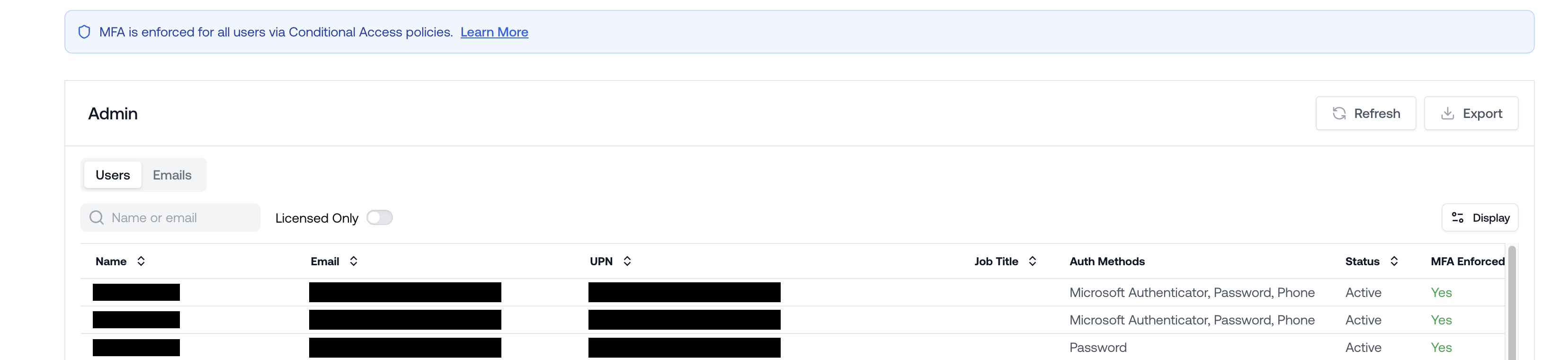
November 21, 2025
SOC Incident Highlighting
Our SOC highlights especially relevant or noteworthy incidents for your clients with a star. This helps you quickly spot the most important incidents to showcase, even when Petra detects many incidents.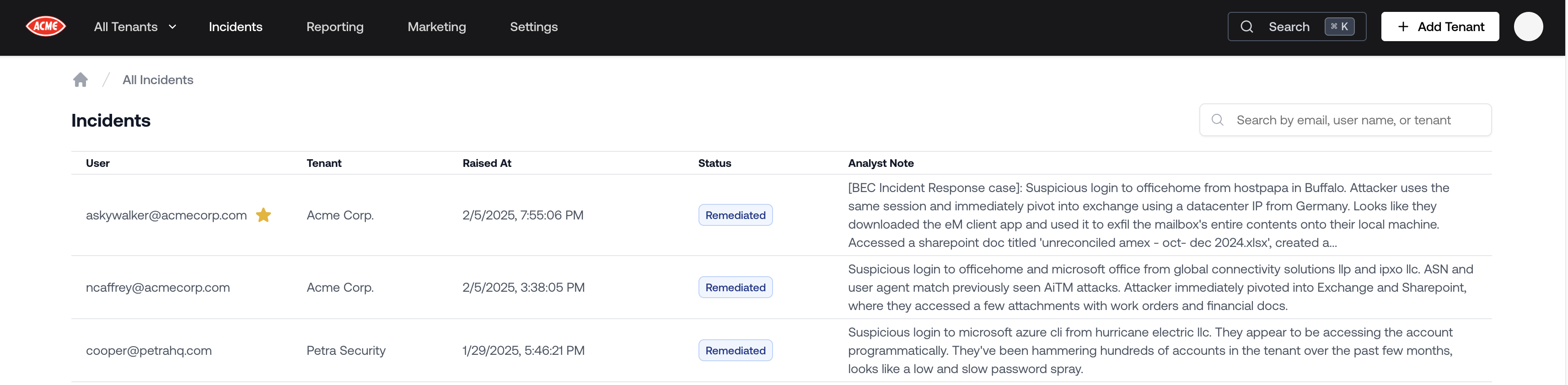
November 14, 2025
Read-Only Members
You can now assign read-only status to members within your organization. Read-only members are restricted to viewing content and cannot perform any actions in the app. By default, all existing users are not set to read-only, and this setting is also not set for new members unless specified. You can designate a member as read-only either when inviting them or by updating their permissions at any time in the Settings -> Access page.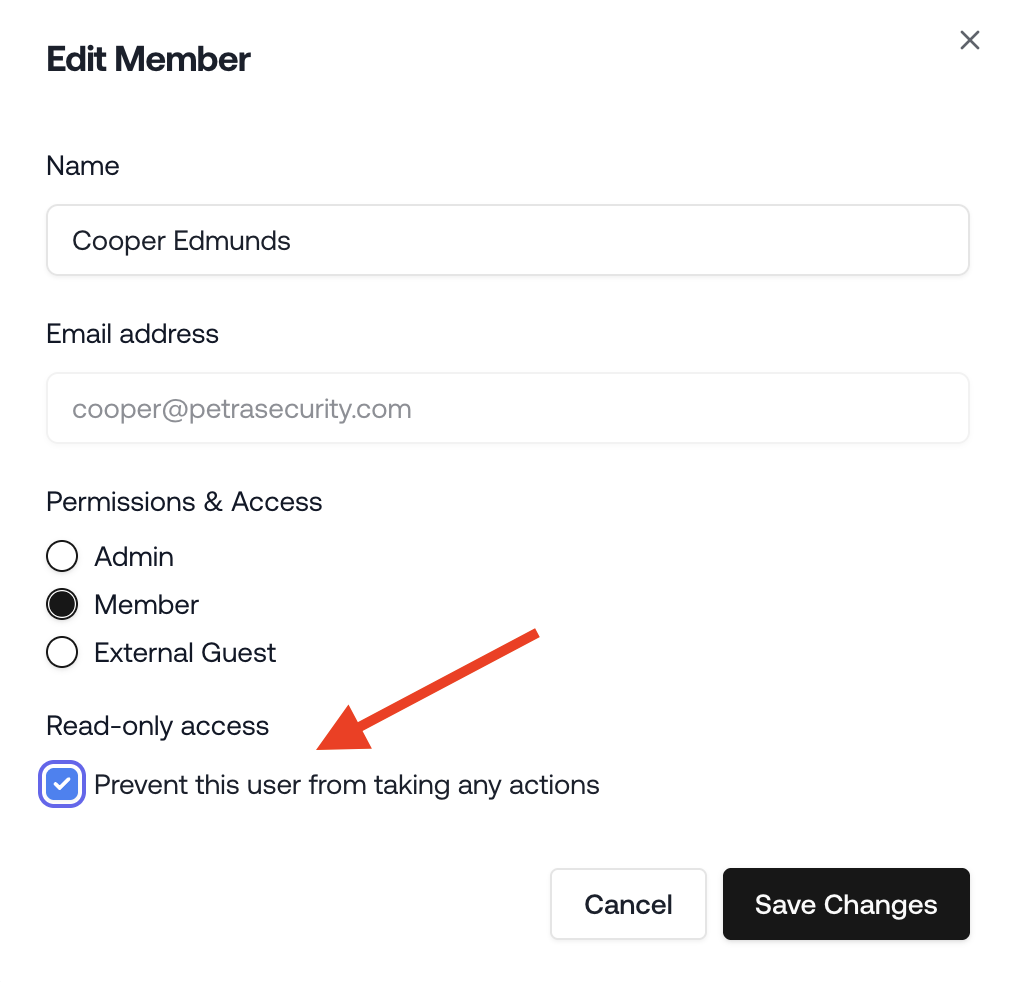
November 7, 2025
Delete Malicious Inbox Rules
You can now delete inbox rules from the Threat Remediation Actions panel.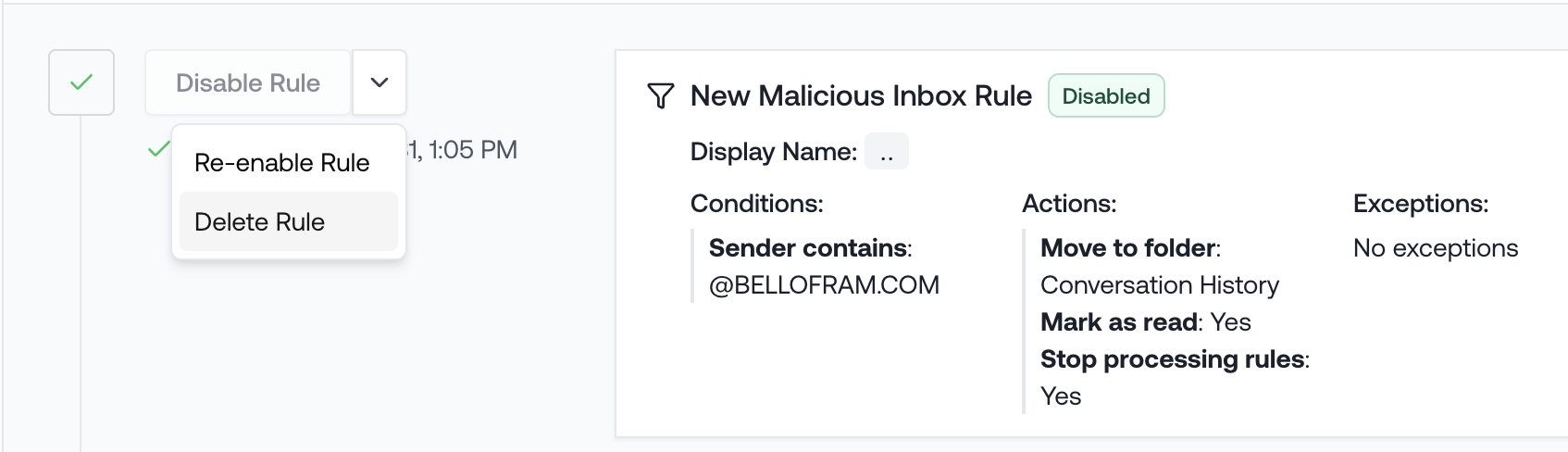
October 31, 2025
New Remediation Actions Panel
The Threat Remediation Actions panel has been updated with a clearer layout, making it easier to find and perform the actions you need.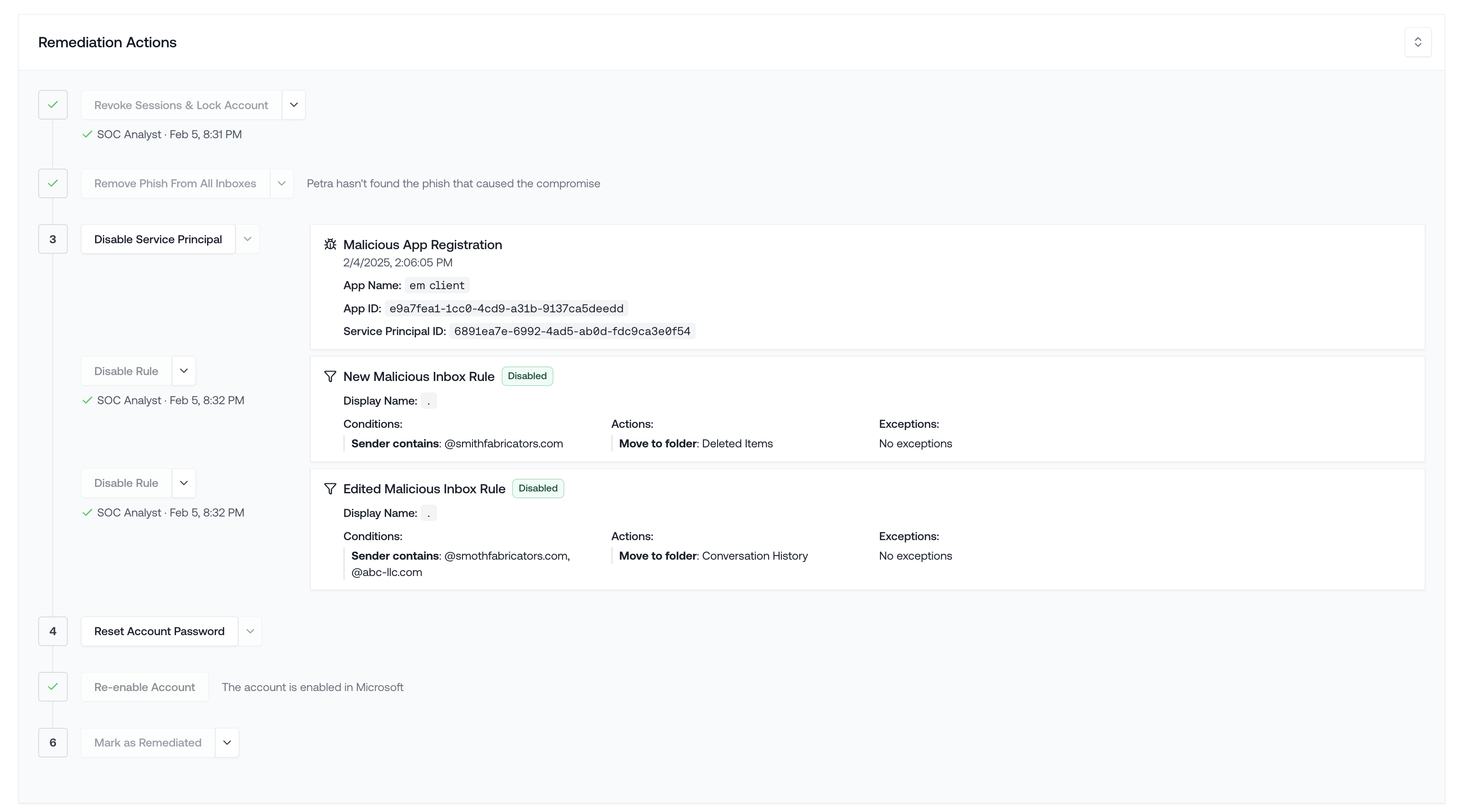
October 24, 2025
International Text Alerts
International text alerts are now supported. When an incident occurs, we can send SMS notifications to members of your organization in any country. To use this feature, go to “Settings” > “Notifications” > “Texts” and choose the appropriate country code for each recipient.
October 17, 2025
Threat Remediation Report Includes Phish
Improved the Threat Remediation Report to include the phish that led to the compromise.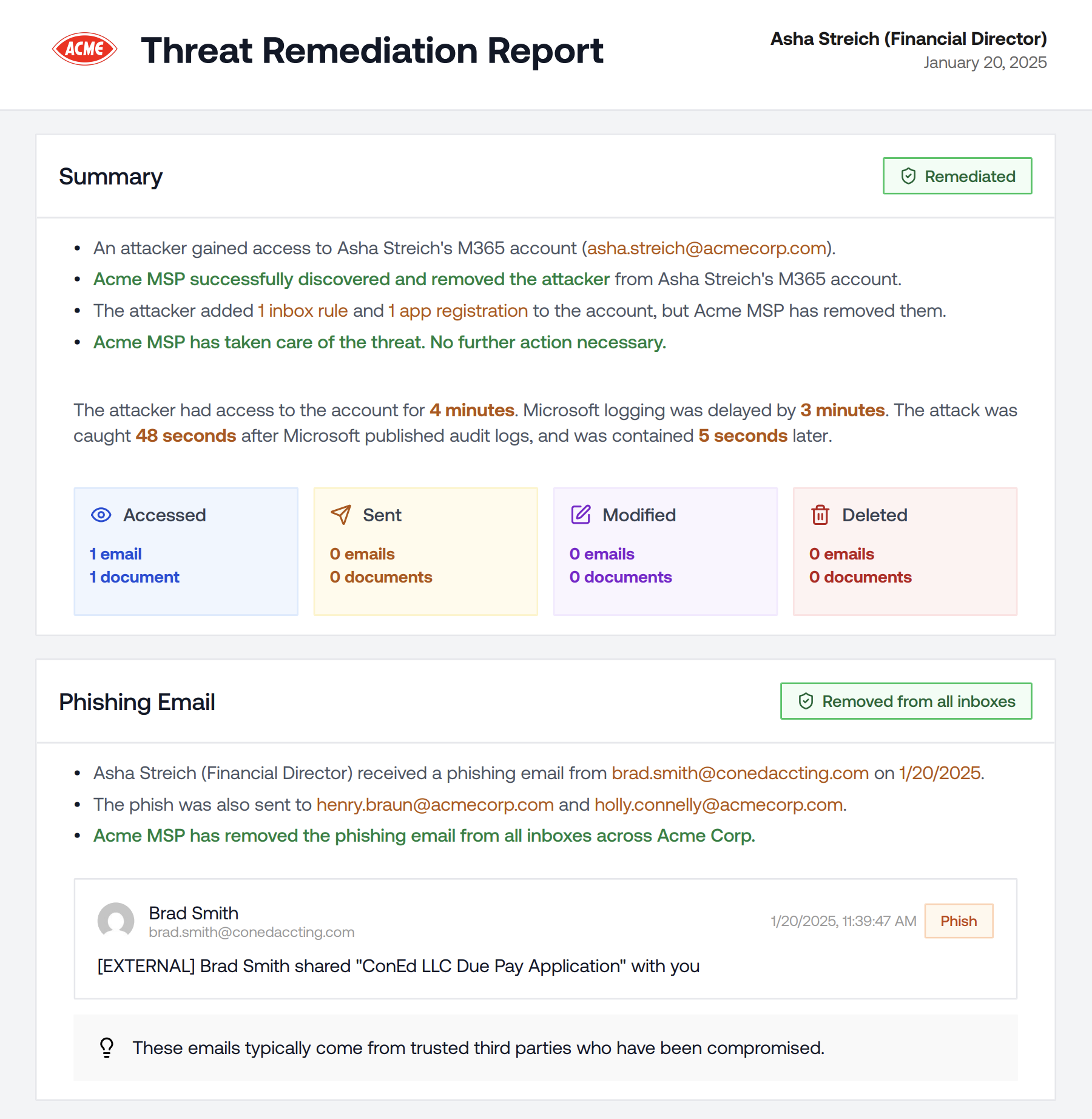
October 10, 2025
Rogue Apps & Remnant Inbox Rule Incident Redesign
We redesigned the Rogue Apps and Remnant Inbox Rule incidents to show all available context and remediation options.September 26, 2025
Full Incidents in Tenant Report Appendix
When a Tenant Report includes an Incident, the complete Incident Report will now be added to the Appendix.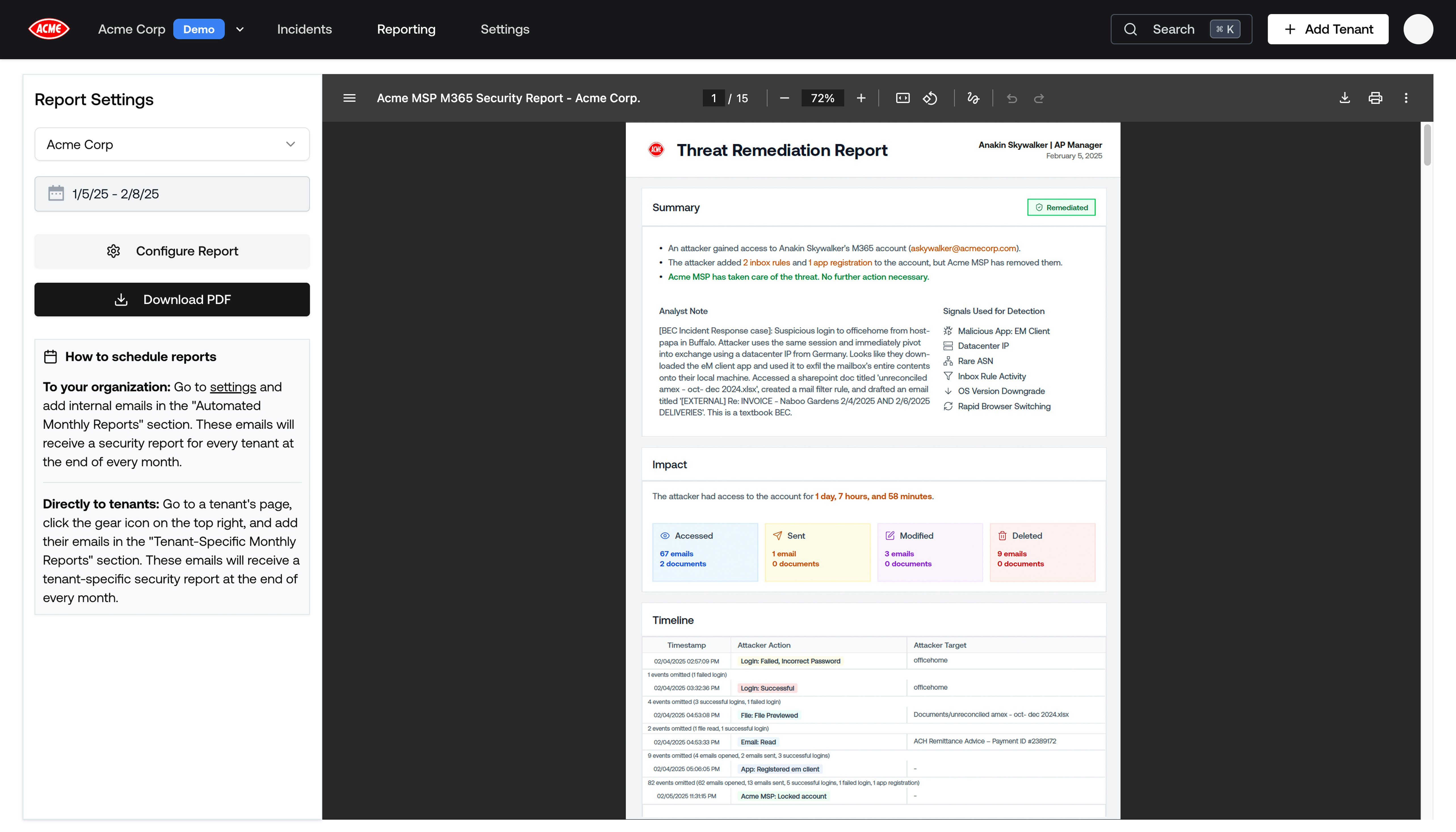
Tenant Report Bug Fixes
Thanks to some helpful feedback from customers, we’ve fixed a few bugs in the Tenant Report.- Improved readability of the Executive Summary page
- Fixed bug for particularly long usernames in the failed attacks section
September 19, 2025
Tenant Report Redesign
The Tenant Report has been redesigned! Go check out the new Report Generator.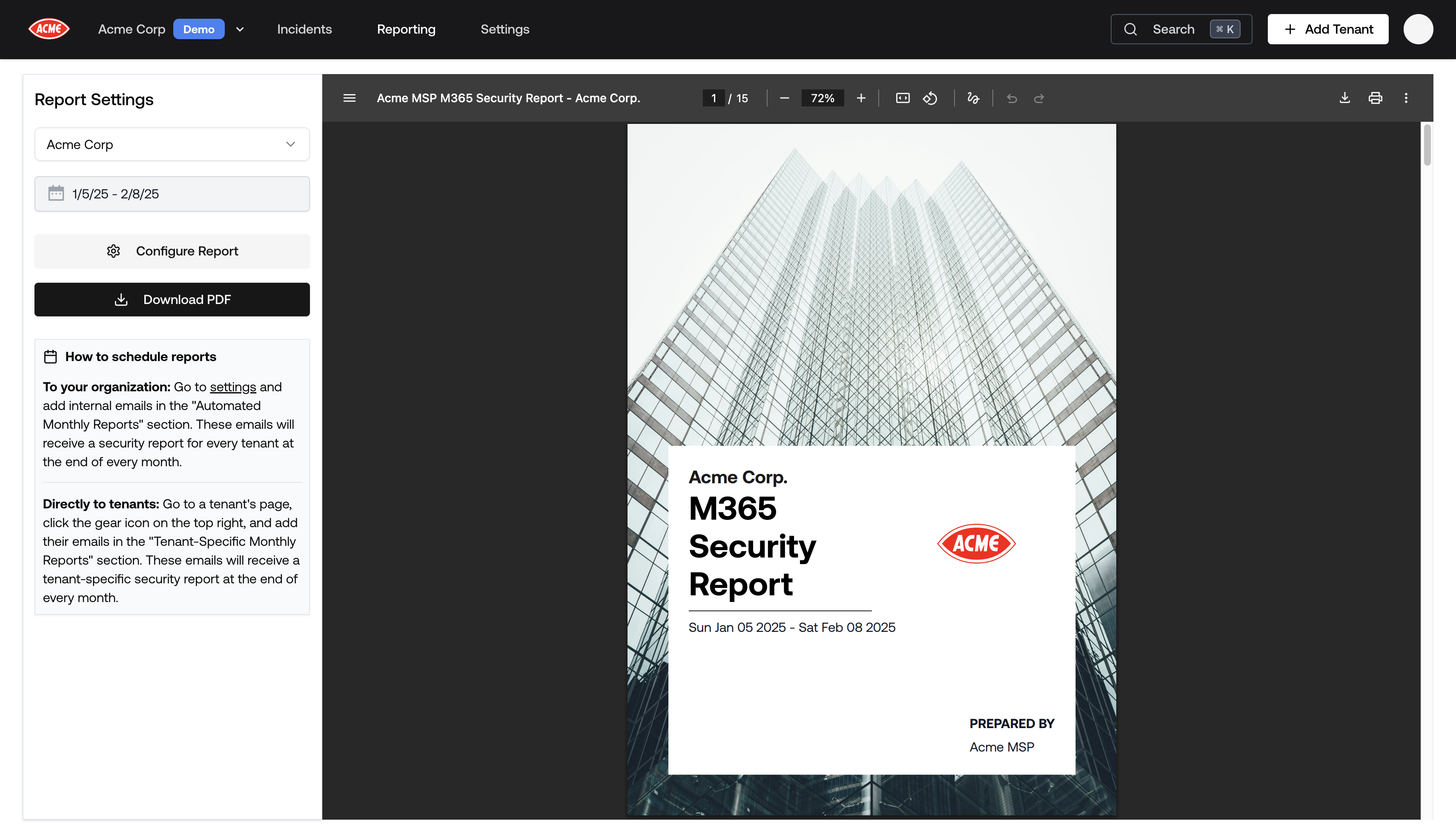
Tenant Report Configuration
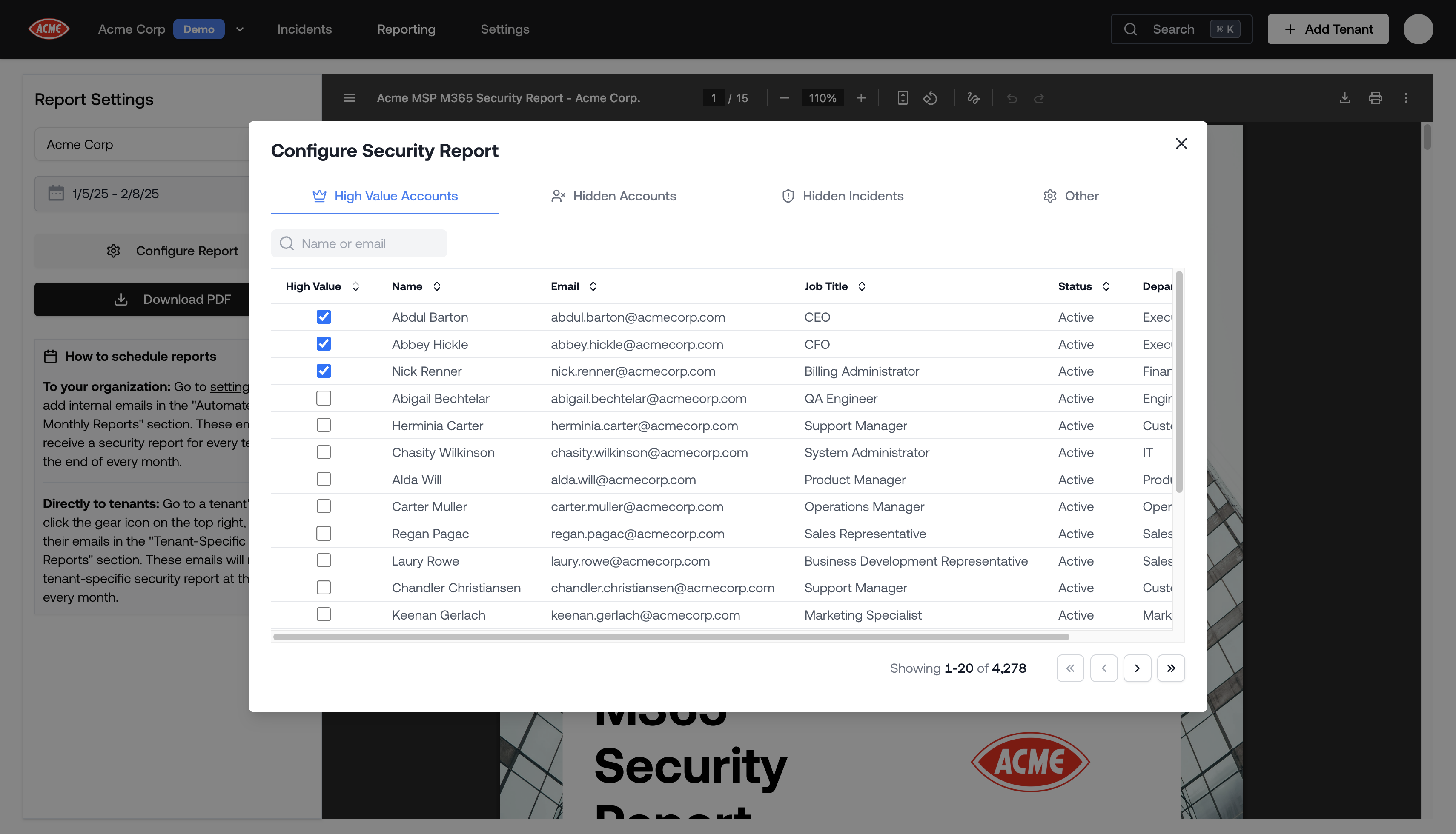
- High Value Accounts: tag accounts like CEO, CFO, billing manager to see greater detail on who is targeting them.
- Hidden Accounts: hide accounts that you want to be excluded from the report, like your own admin account or testing accounts.
- Hidden Incidents: hide incidents that you want to be excluded from the report, like those that you’ve already surfaced to the client.
- Other Options: customize which sections are included in the report.
September 12, 2025
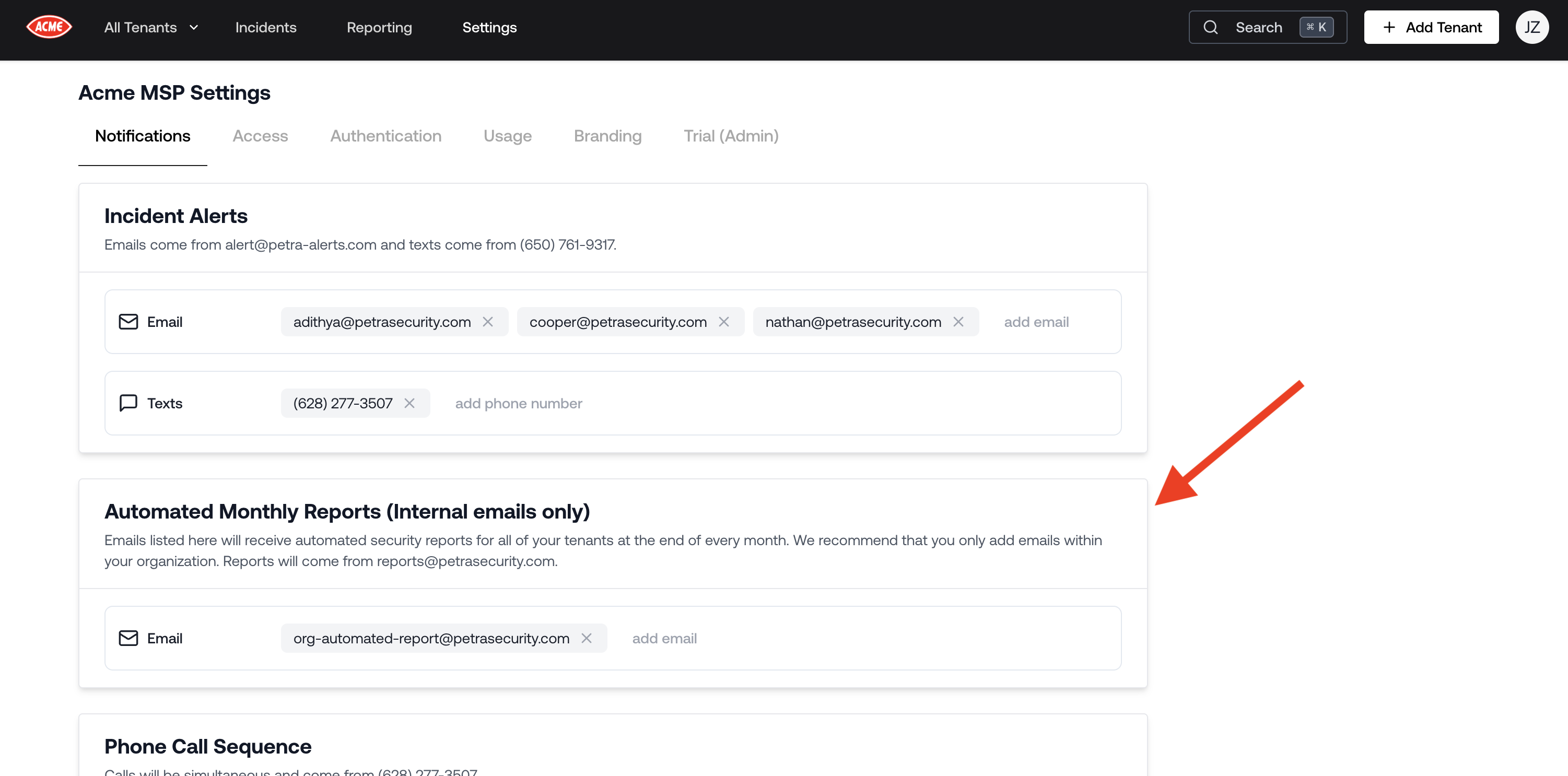
Automate Sending Monthly Tenant Reports
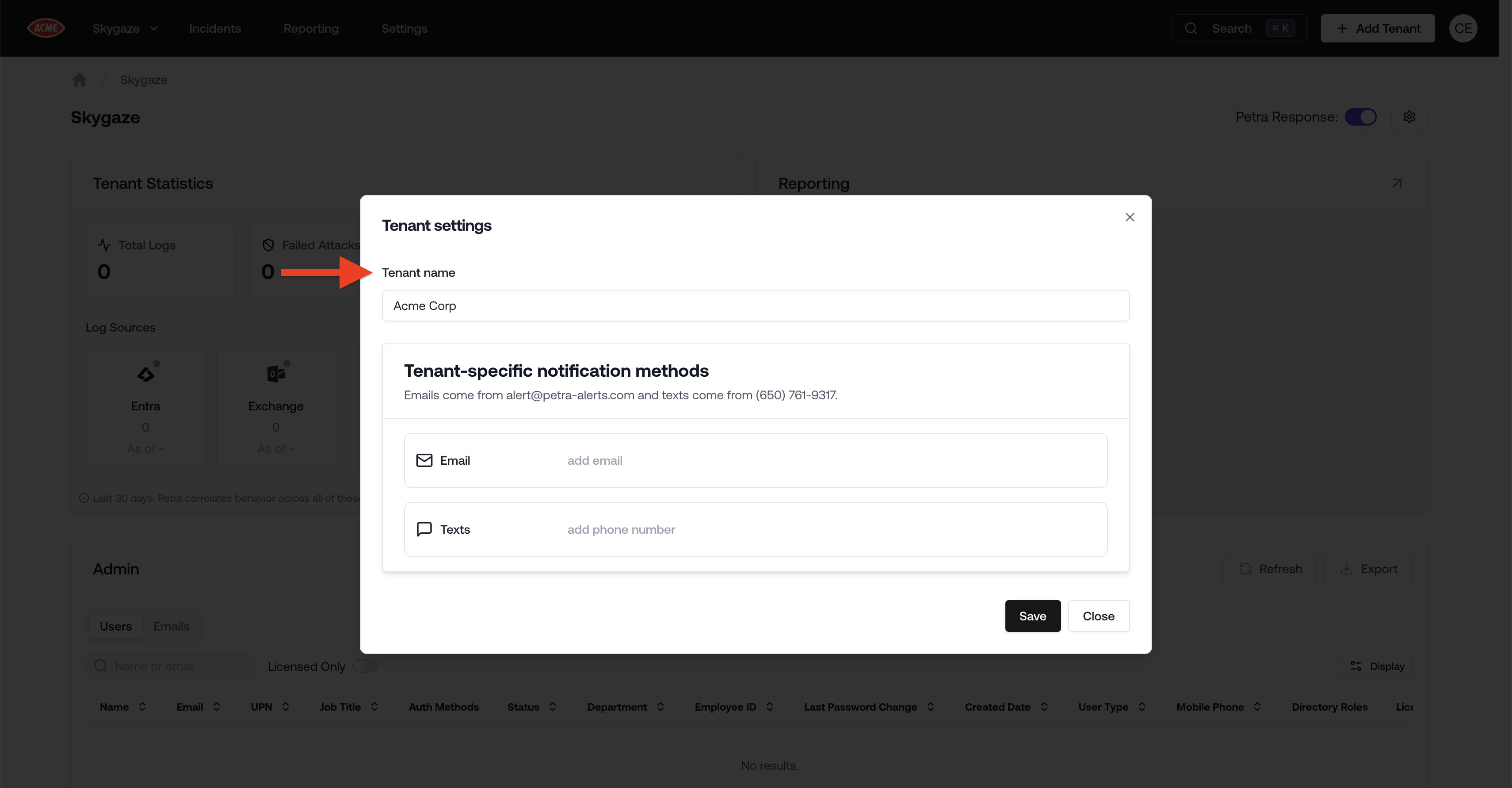
Now you can schedule sending security reports to your tenants and your organization at the end of every month.Directly to tenants: Go to a tenant’s page, click the gear icon on the top right, and add their emails in the “Tenant-Specific Monthly Reports” section. These emails will receive a tenant-specific security report at the end of every month.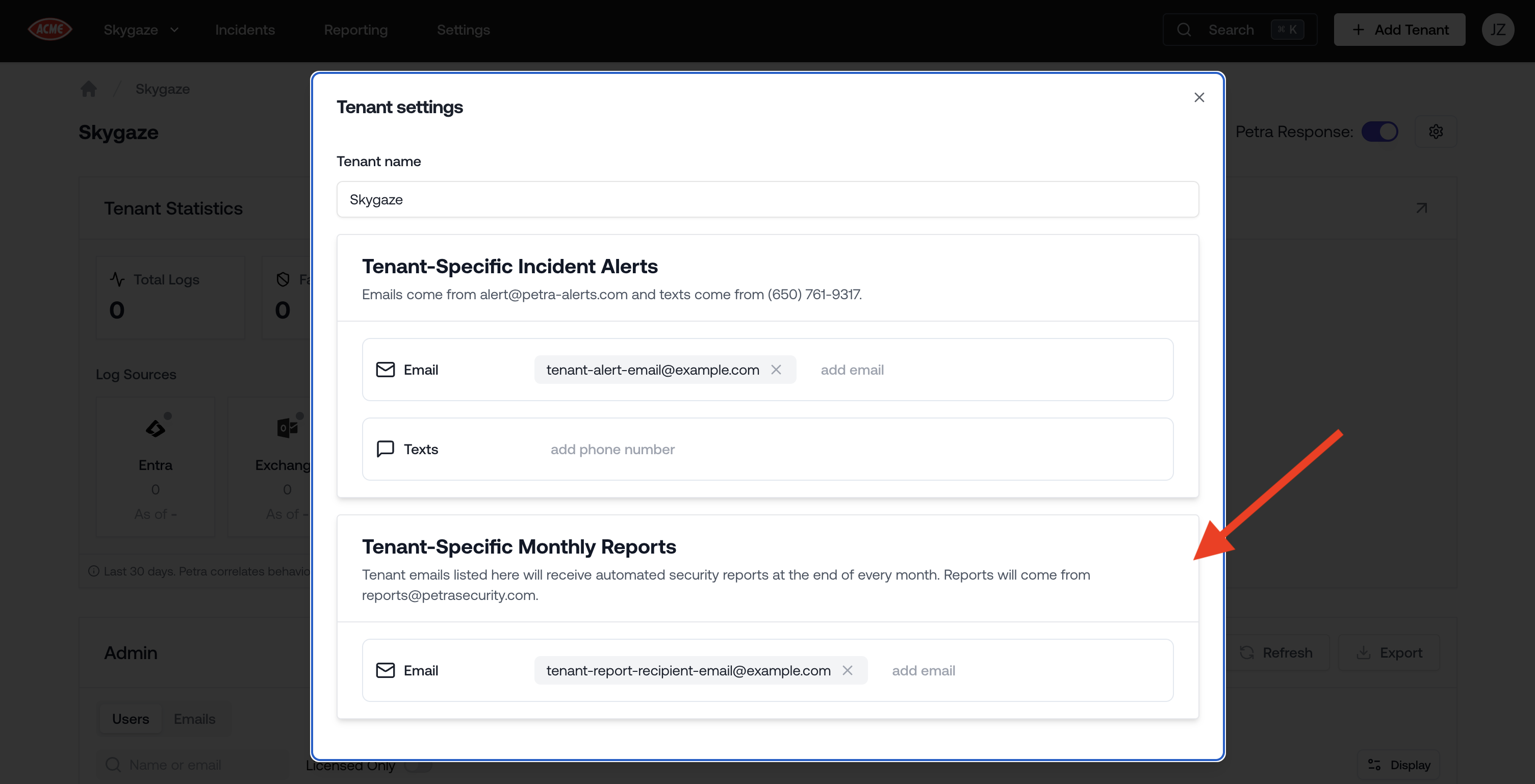
September 5, 2025
August 29, 2025
Petra Automatically Enables Audit Logs
Now when you onboard a tenant, Petra automatically enables audit logs if they were not already enabled.We all know the pain of trying to enable audit logs in Purview—it lags by hours and often takes several attempts. Now onboarding in Petra is the last step in setting up monitoring.Like everything else in Petra, this is available regardless of Microsoft license level.Improved Threat Remediation Report Timeline
We updated the summary timeline at the bottom of the Threat Remediation Report to focus on the most important events in the incident—especially how you stopped it.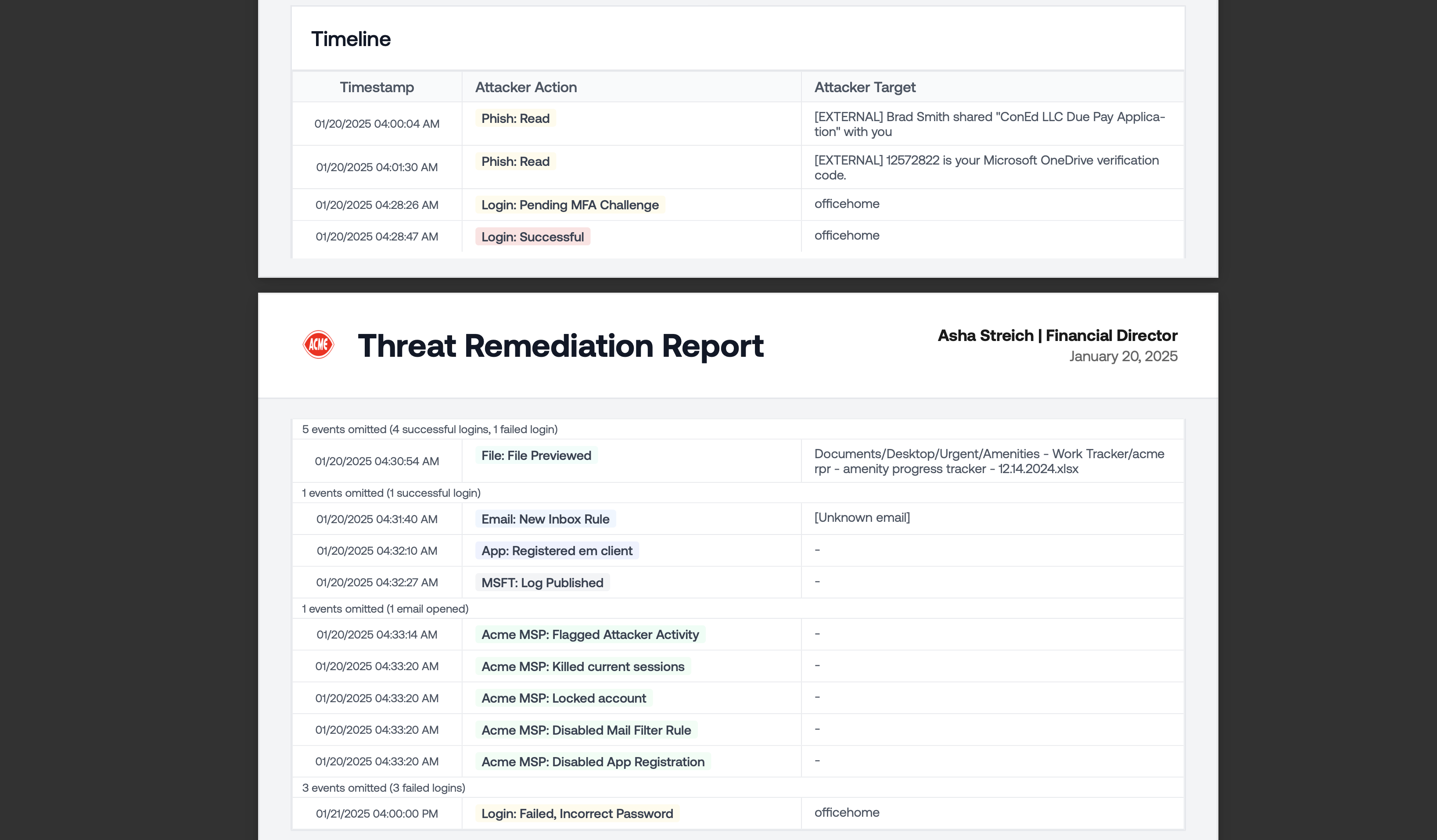
August 22, 2025
SharePoint Malicious File Removal
Attackers often upload new files to SharePoint to use as a phishing lure.Petra commonly uncovers these files in baselining when latent attackers are discovered. Now you can remove them from SharePoint from within Petra without opening Microsoft.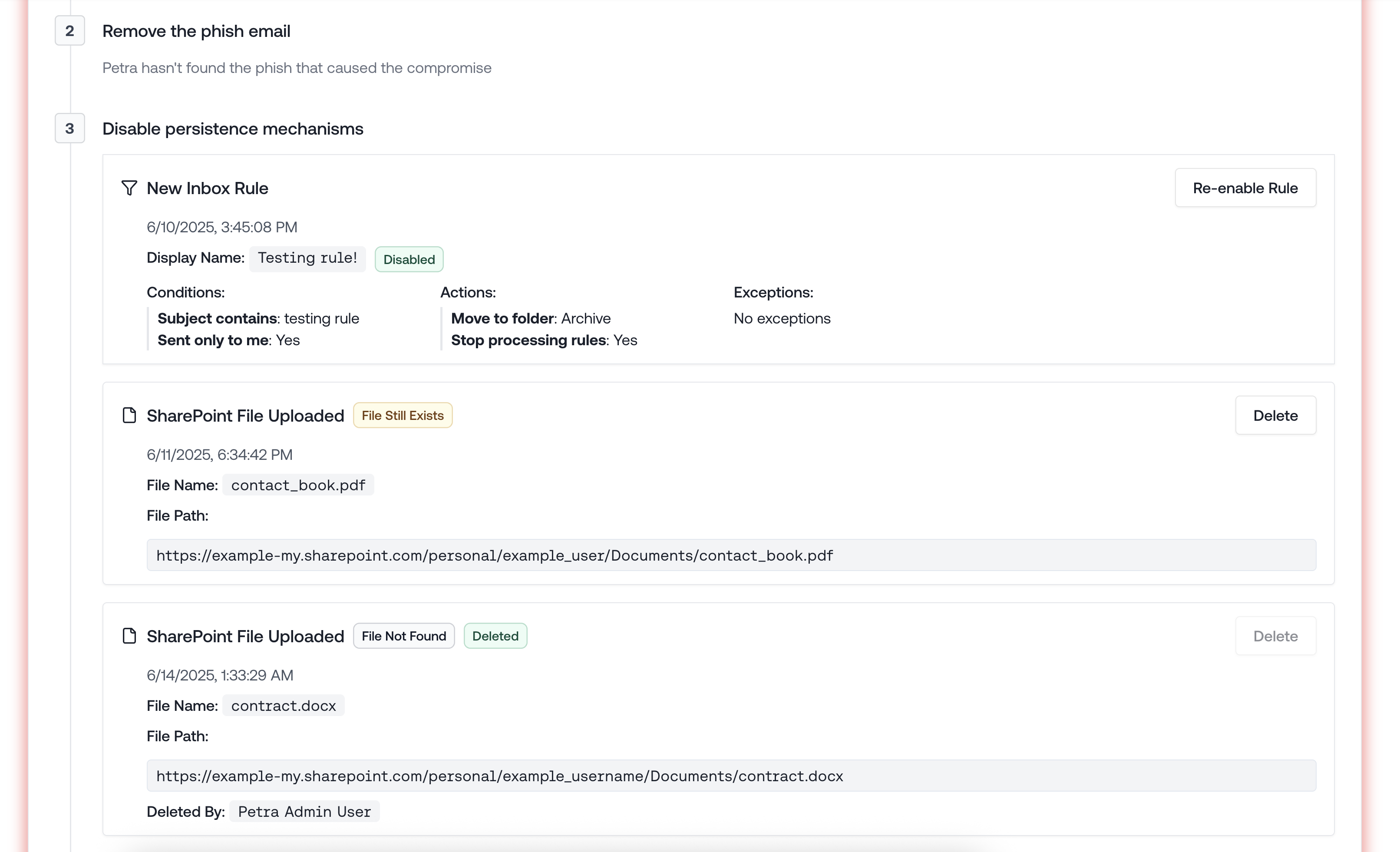
August 15, 2025
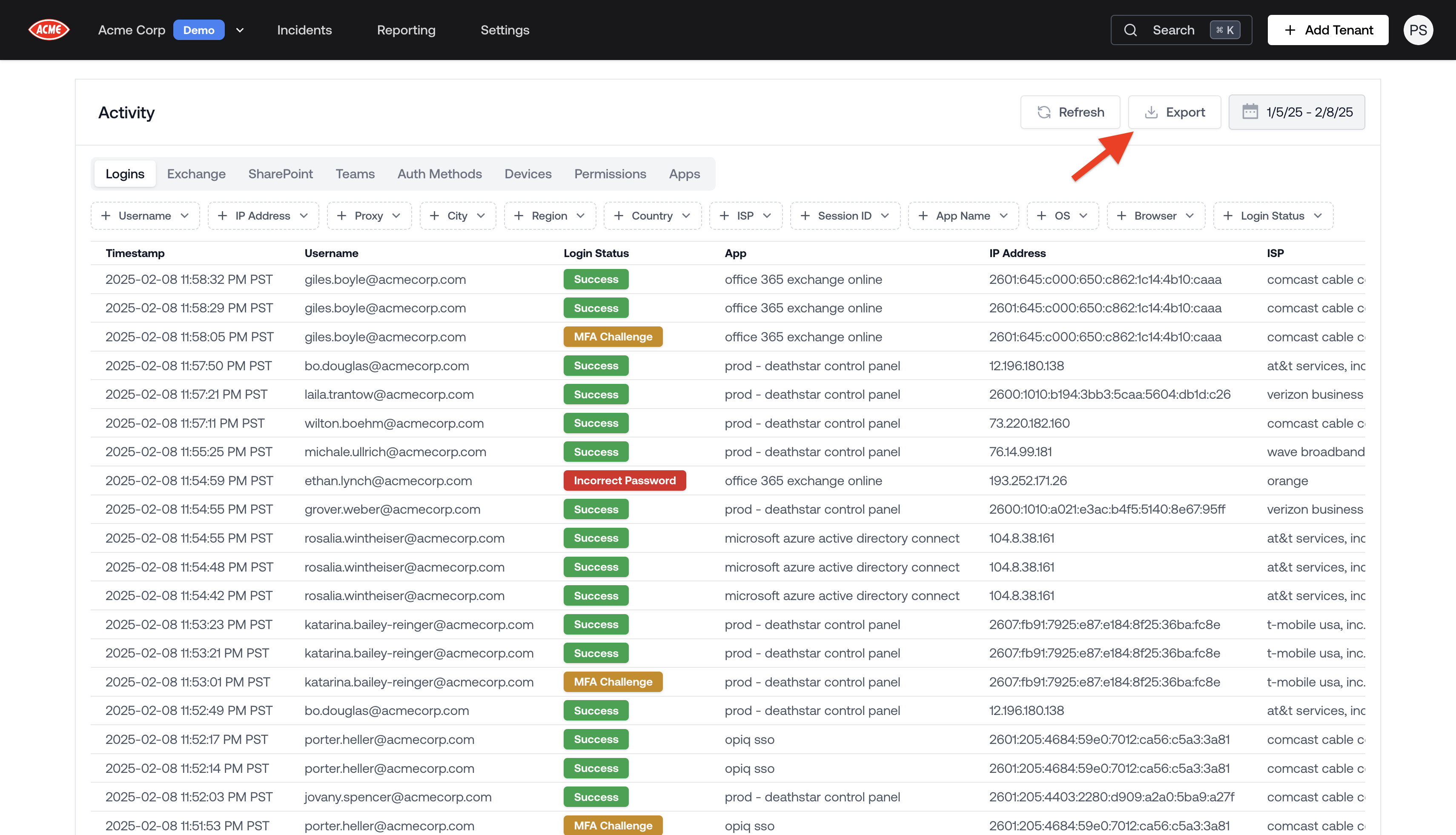
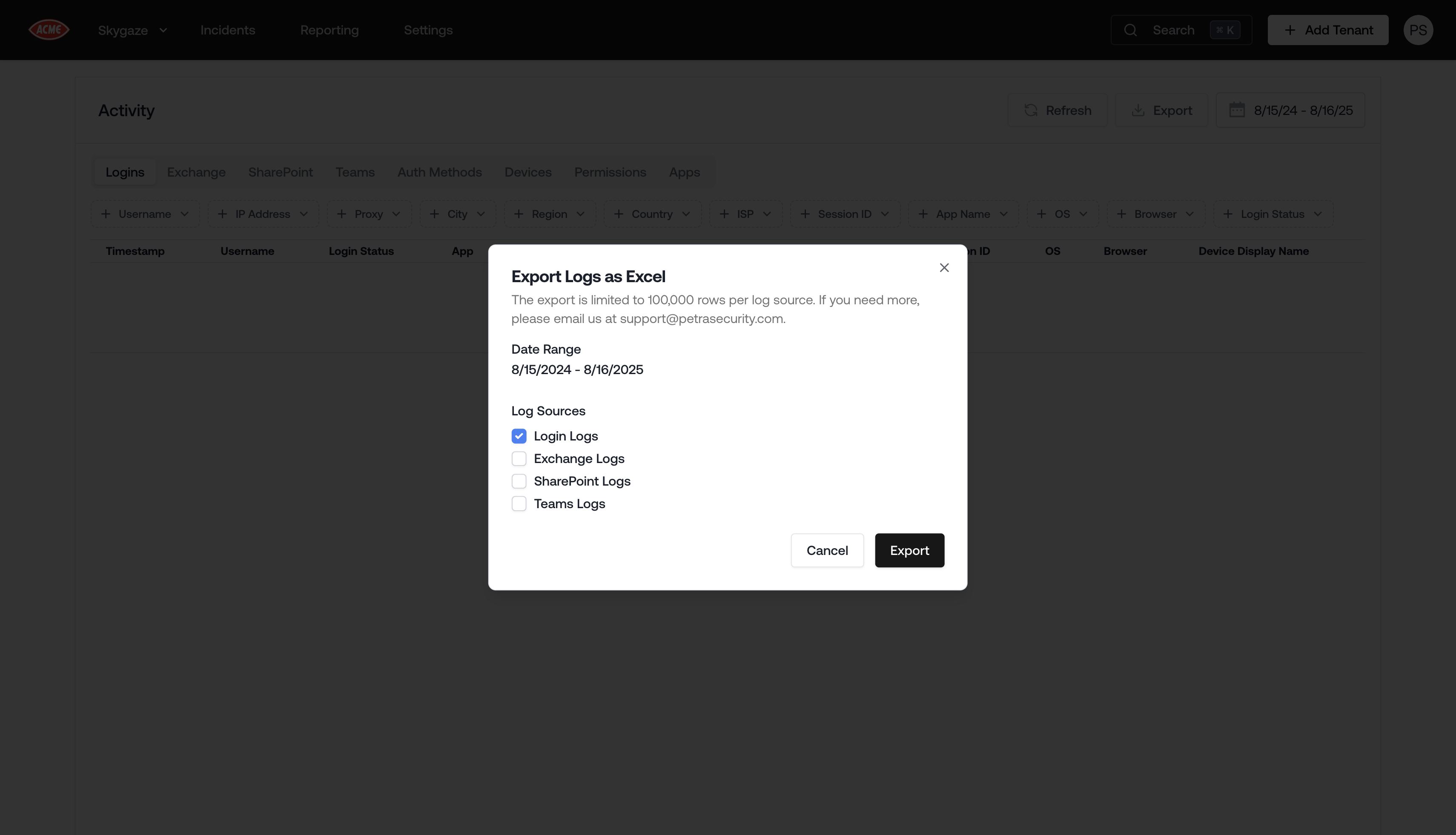
Tenant Logs Excel Export
You can now export tenant logs to Excel. The export includes fully enriched metadata for Exchange, including email subjects, sender, recipients, and more.The export respects any filters you have applied in the viewer, so you can get, for example:- A specific user’s activity across logins, Exchange, SharePoint, Teams, etc.
- All activity across a tenant for a specific time period.
- All sent emails across a tenant for a specific time period.
August 8, 2025
Halo PSA Integration
You can now link your Halo PSA account to Petra. Go to Settings > Integrations to link your Halo PSA account.Follow this guide to integrate with Halo PSA: Halo PSA Integration.August 1, 2025
Phish Search & Retraction
Phish search and retraction now catches replies and forwards. It’s surprisingly common for the recipient of a phish to forward it to coworkers. Now Petra finds all of those replies and forwards so we can retract those too.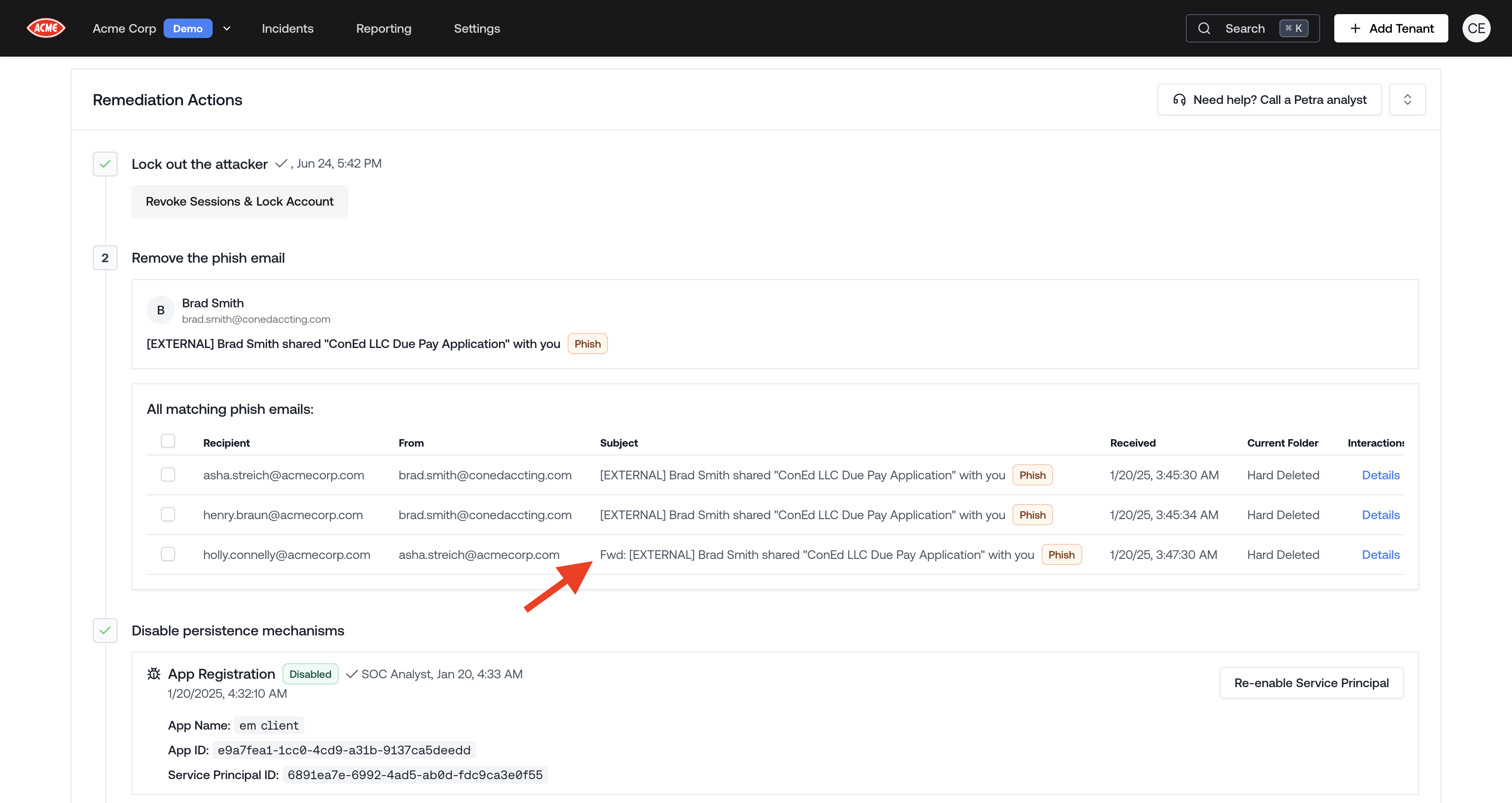
Excel Export for Usage by Tenant
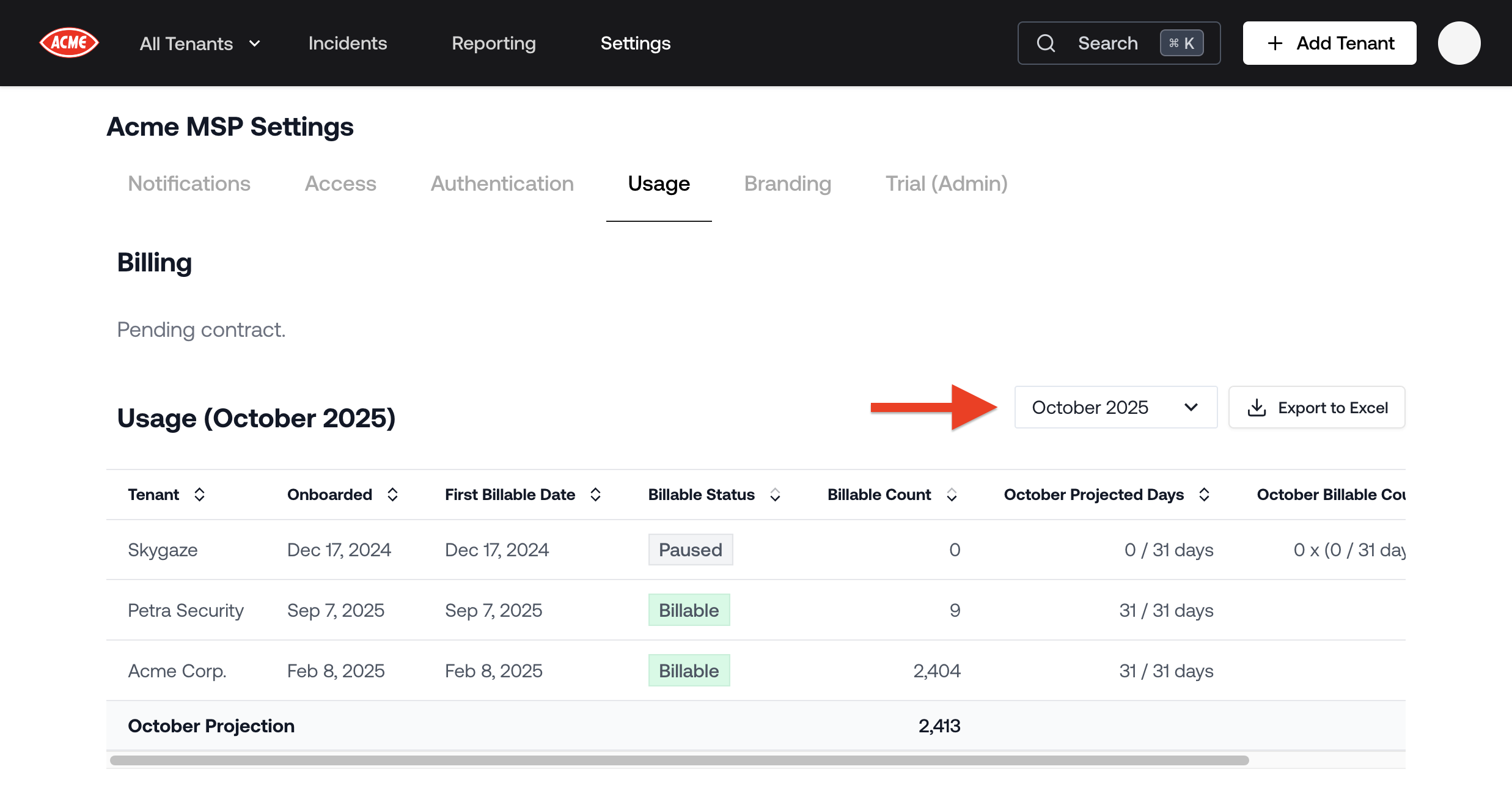
The usage page in settings now includes an option to export usage data by tenant to Excel.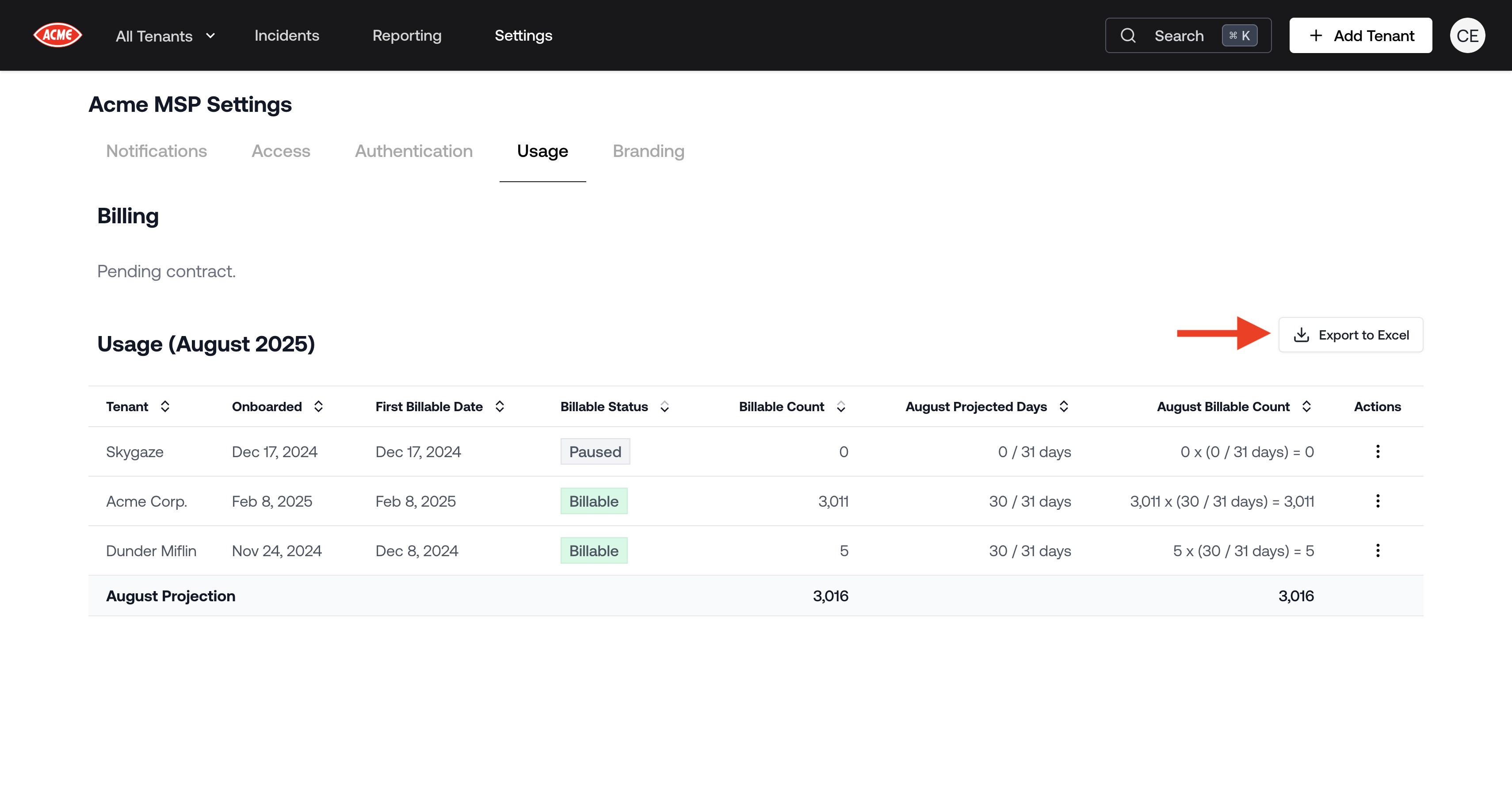
Beta of API Endpoint for Tenant Usage
We launched a beta of an API endpoint for tenant usage. Contact us if you want to try it. Read more about it in the API documentation.July 25, 2025
Email Search and Removal
The admin panel now includes the ability to search for emails by subject, sender, and recipient, as well as the option to remove emails.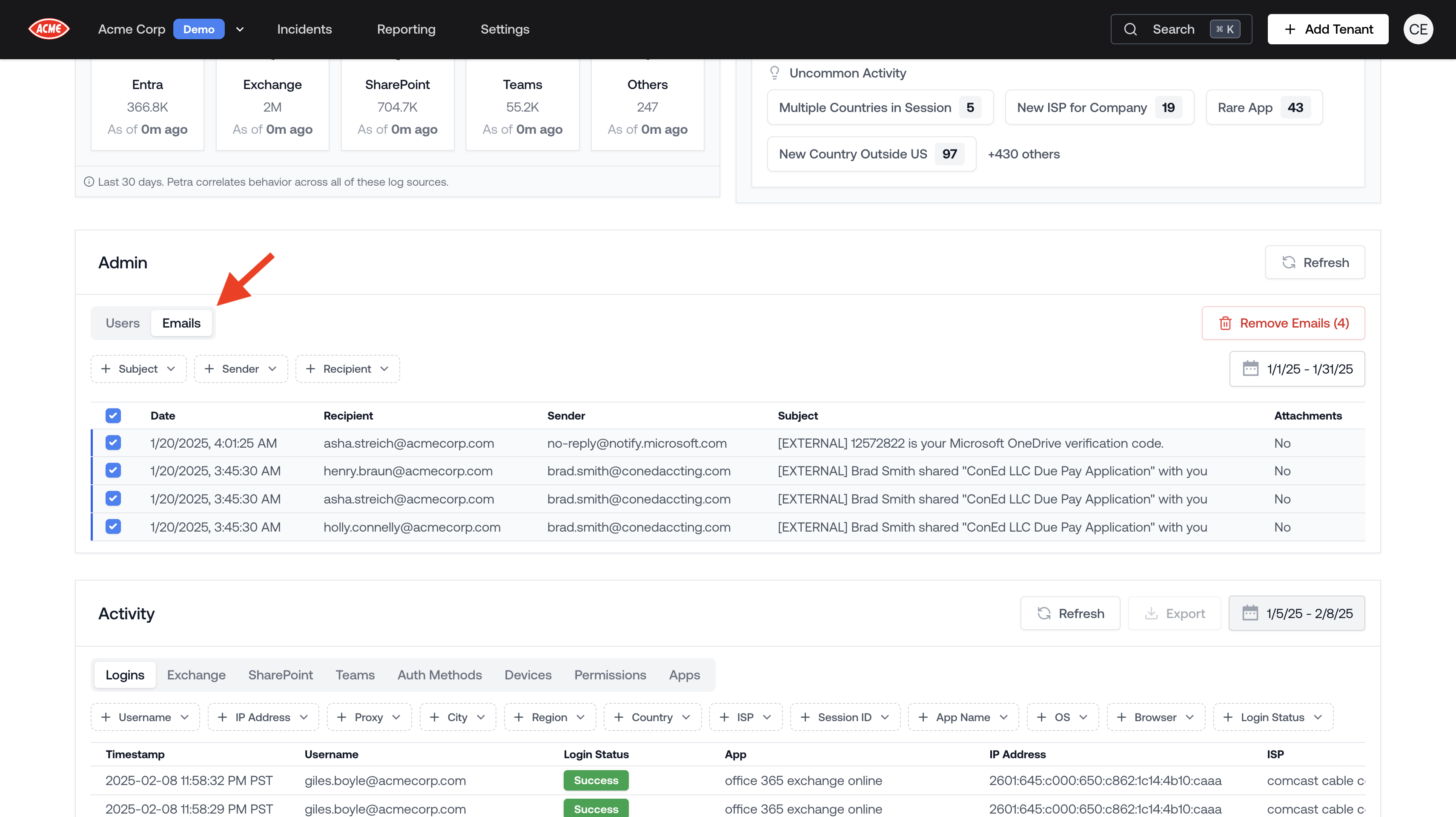
Sensitive Tenants
Sensitive Tenants are tenants that only admins have access to within Petra. This is useful for safeguarding access to certain tenants, such as the MSP’s own tenant.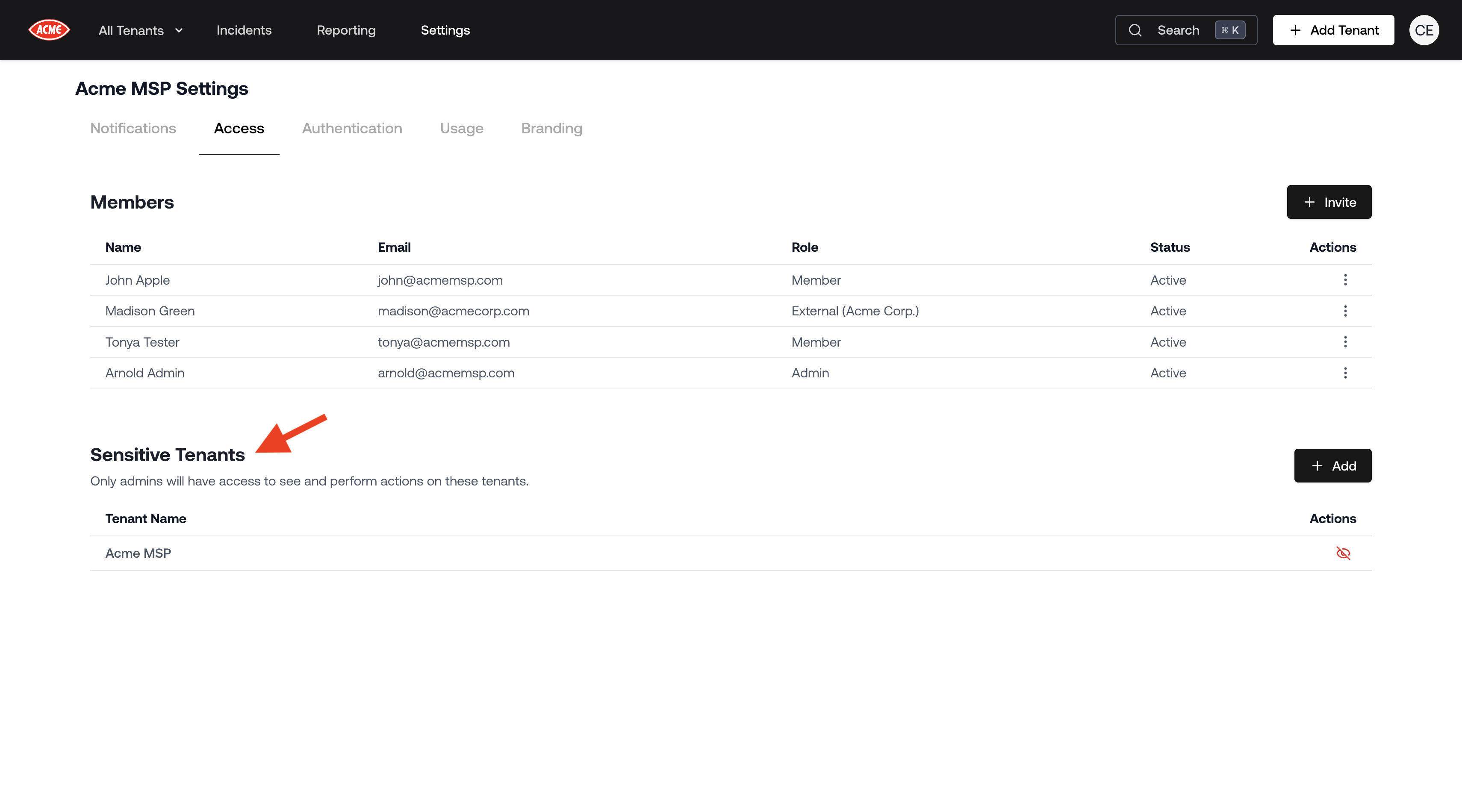
July 18, 2025
Better Phish Deletion
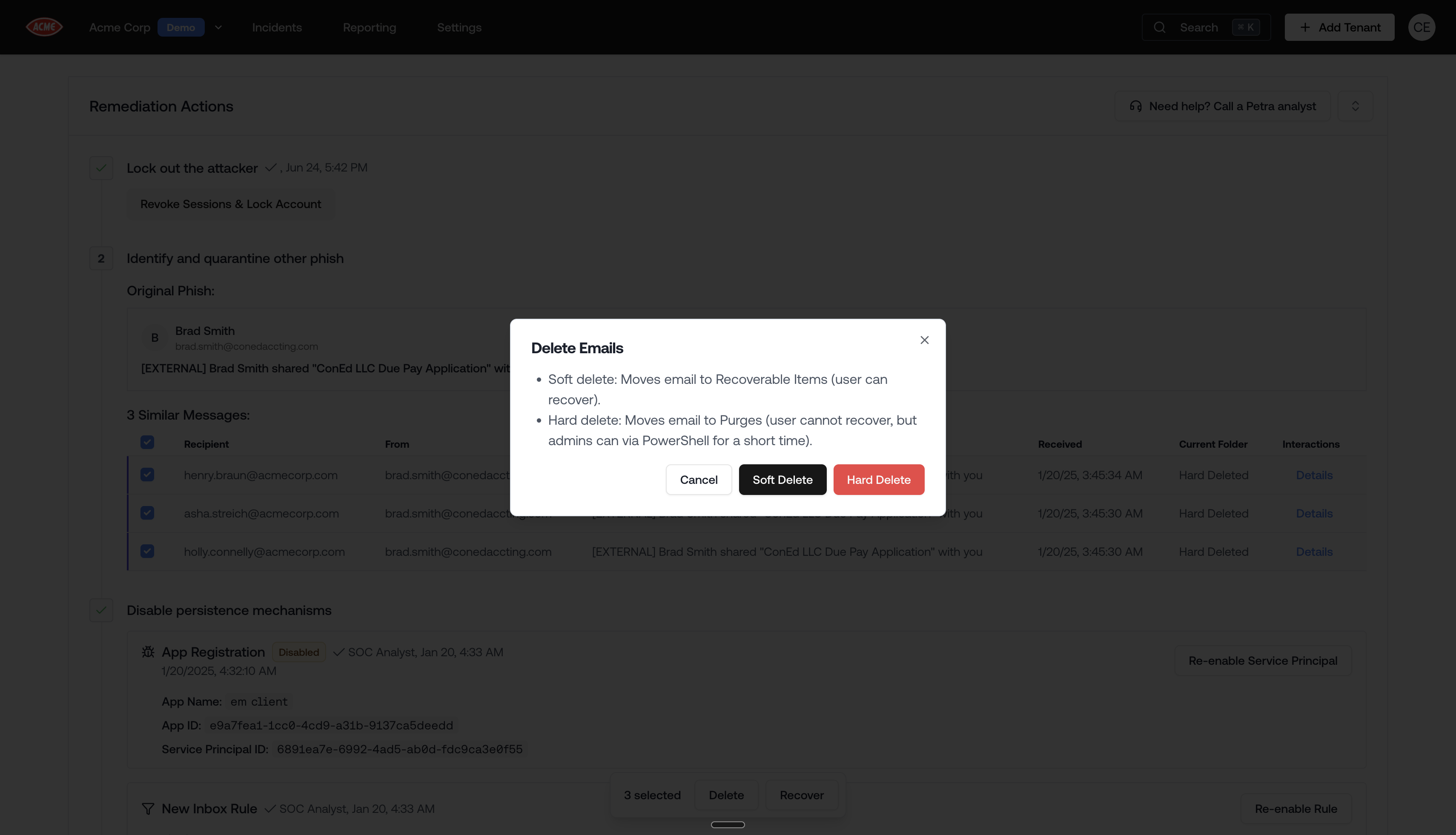
- Soft delete moves the email to the recoverable folder within deleted items (which users are much less likely to find than just the deleted folder).
- Hard delete deletes the email from the mailbox.
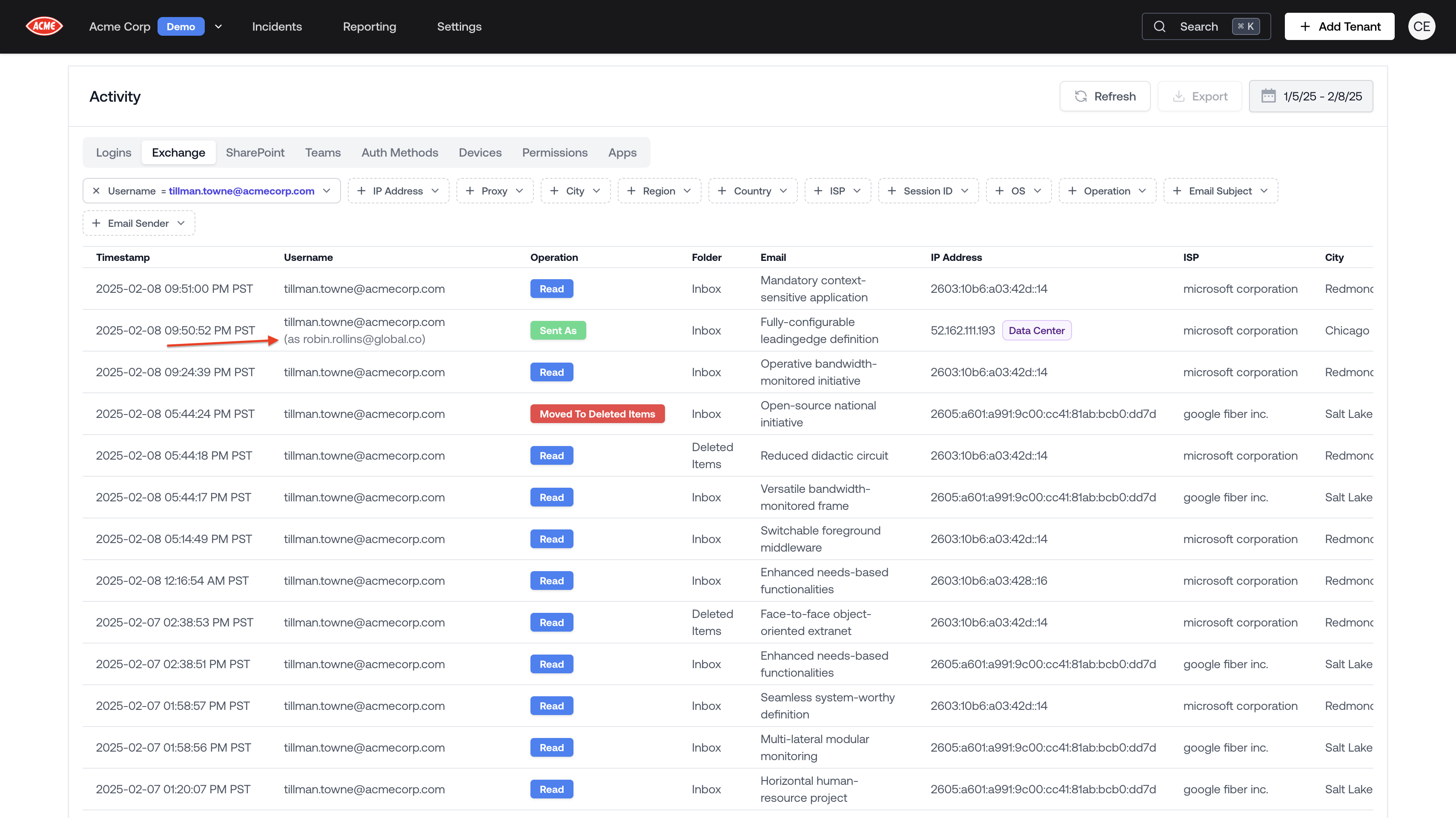
Delegated Activity in the Activity Viewer
July 11, 2025
Deep Links & Streamlined Sign In
- Deep Links: Now if you open a link to a specific page (e.g. an incident link in a ticket), you’ll be taken to that same page after you sign in.
- Streamlined Sign In: We removed the organization selection step during sign in, reducing sign-in flow by 1 click in 99% of cases.
Incident Forensics Countdown
Microsoft logs are often delayed by a few minutes, which could cause the forensics in the Threat Remediation Report to change in the minutes after the incident.You can now see an estimated time for all of the forensics to be published by Microsoft and included in the Threat Remediation Report.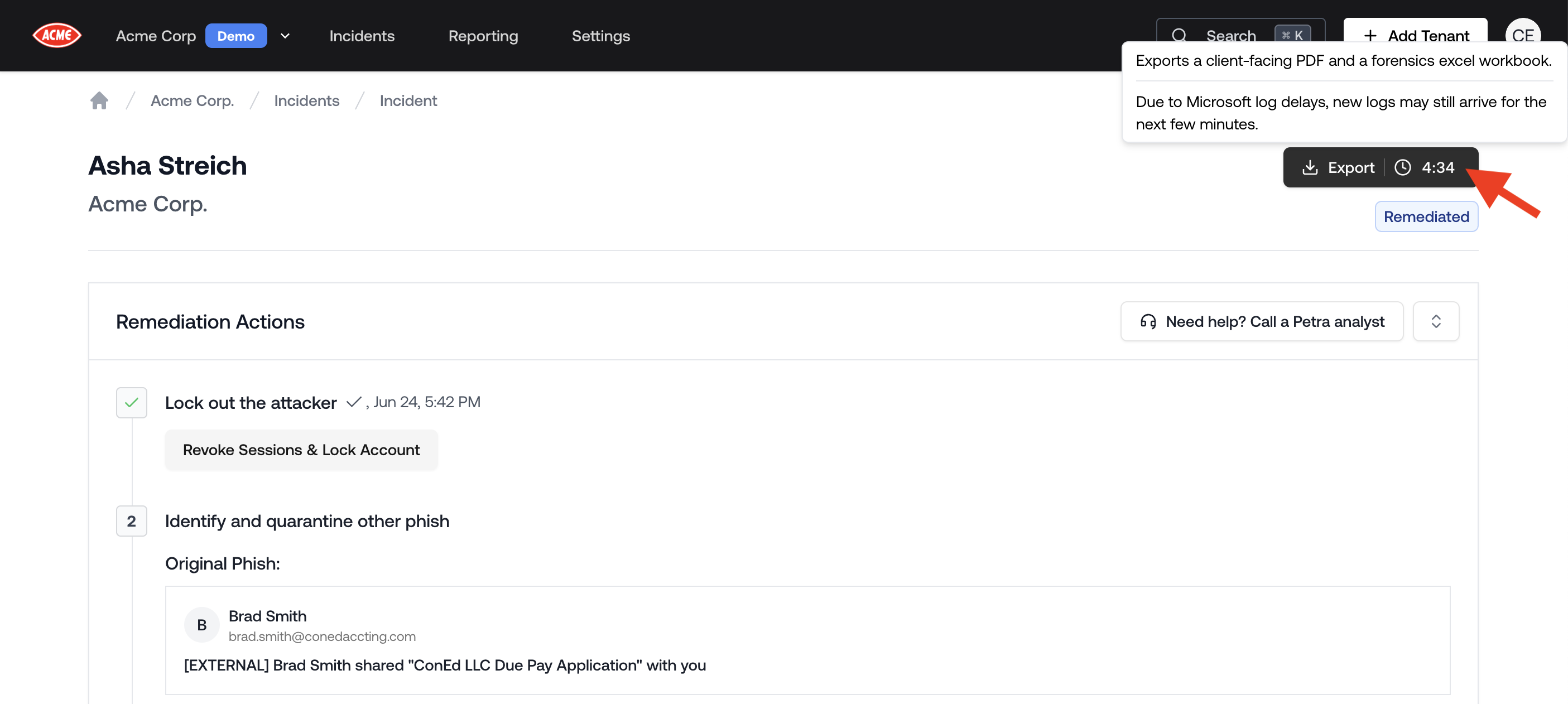
July 4, 2025
Improvements to Self-serve Tenant Management
June 27, 2025
Similar Phish Retraction
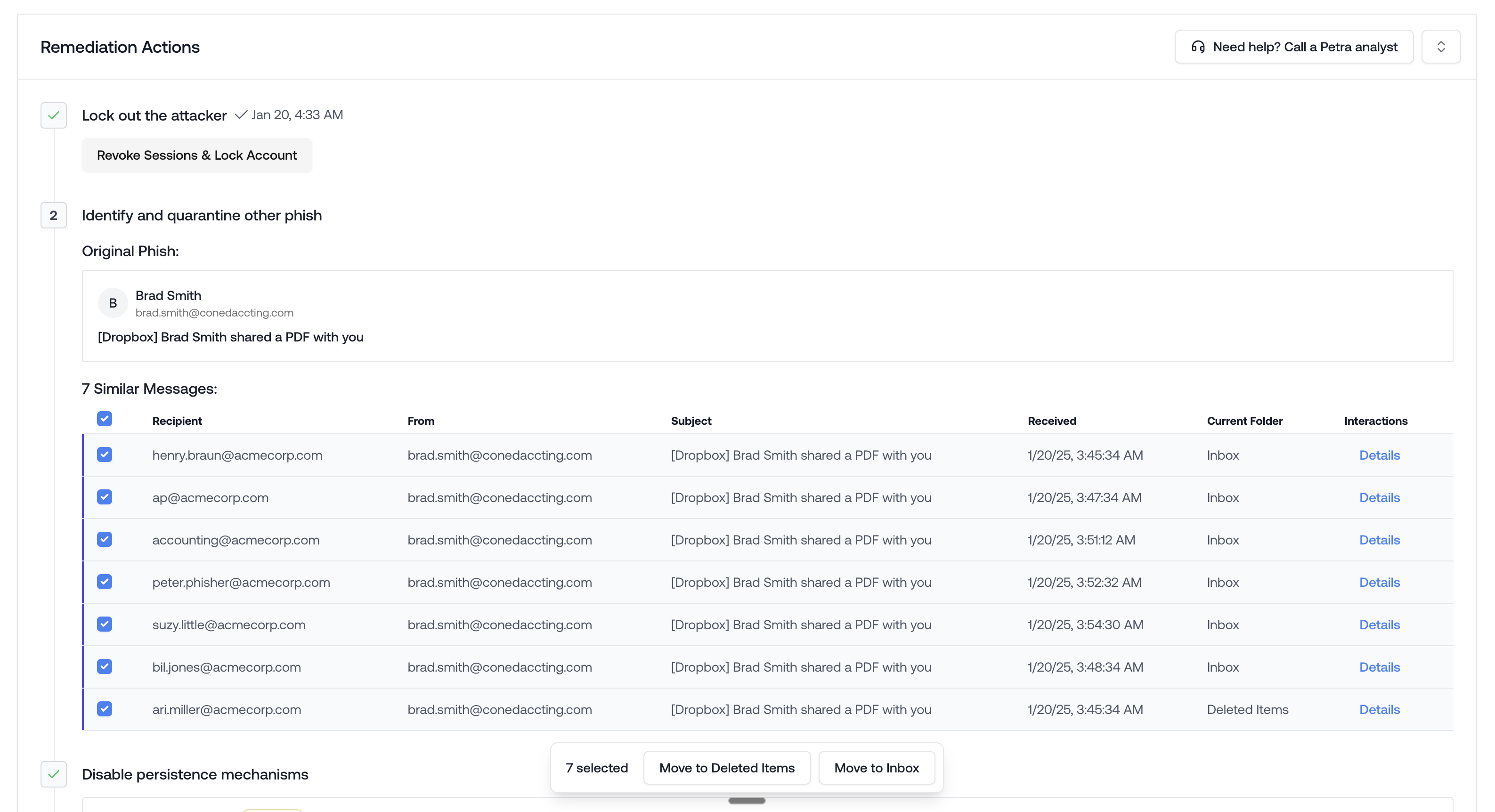
- The ‘Current Folder’ column updates in realtime as you or the employee moves the email.
- The ‘Interactions’ column opens the Email Interactions Panel which displays all read/moved/deleted/etc. interactions with the email.
June 20, 2025
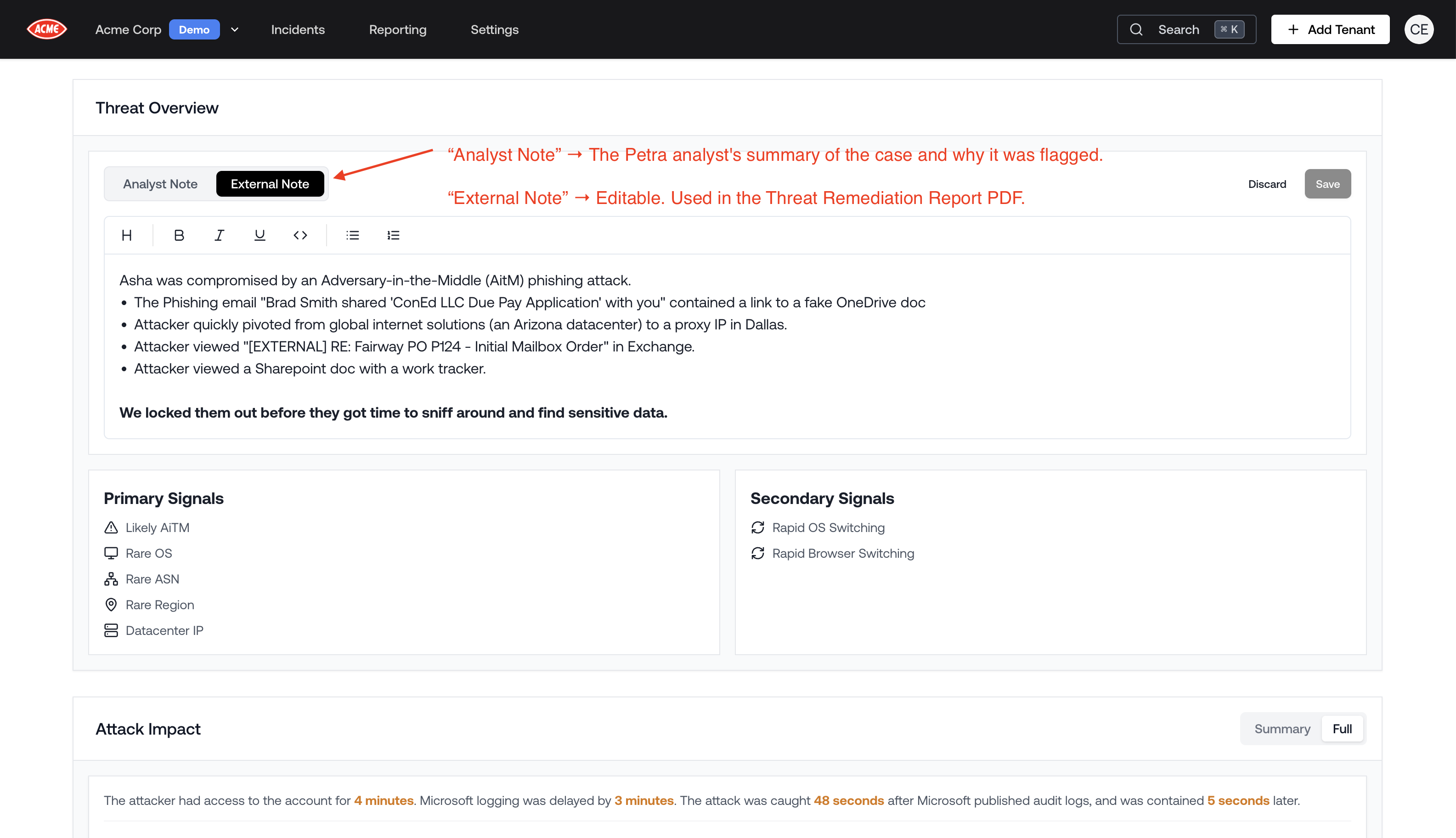
Edit Analyst Note for Reports
June 13, 2025
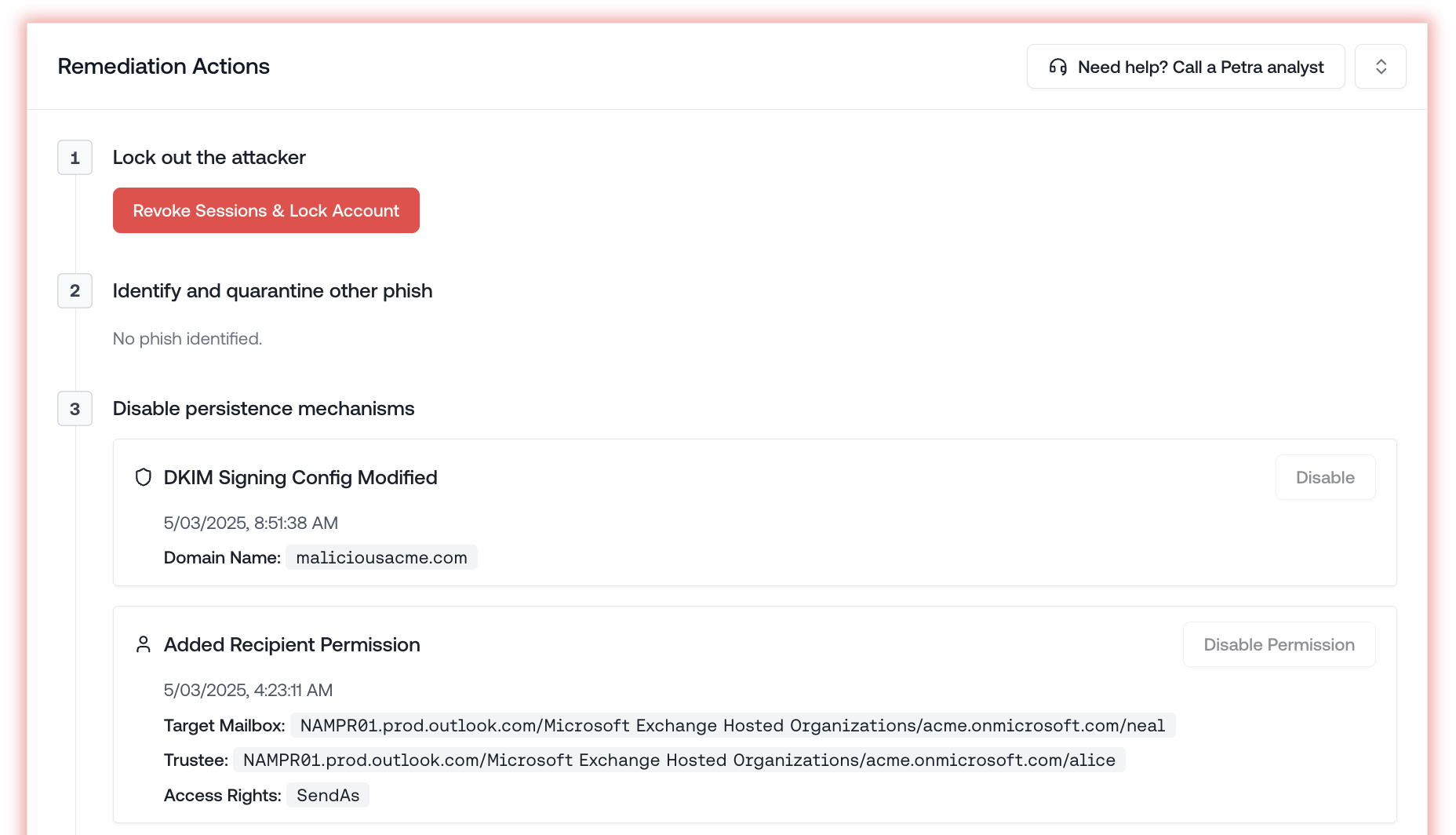
Added DKIM & Mailbox Permissions to Remediation Actions Panel
June 6, 2025
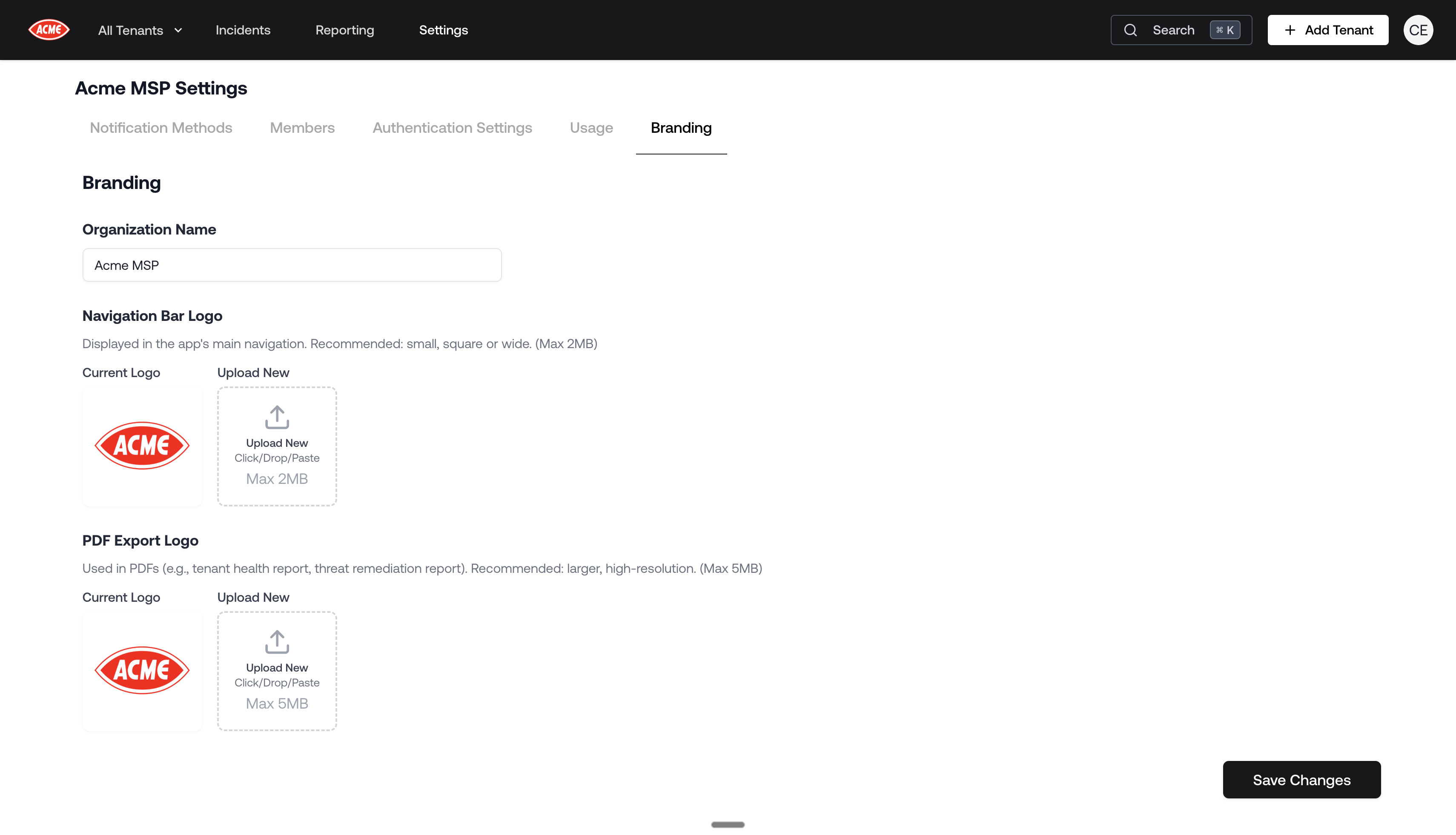
White-label Portal & PDF Reports
May 30, 2025
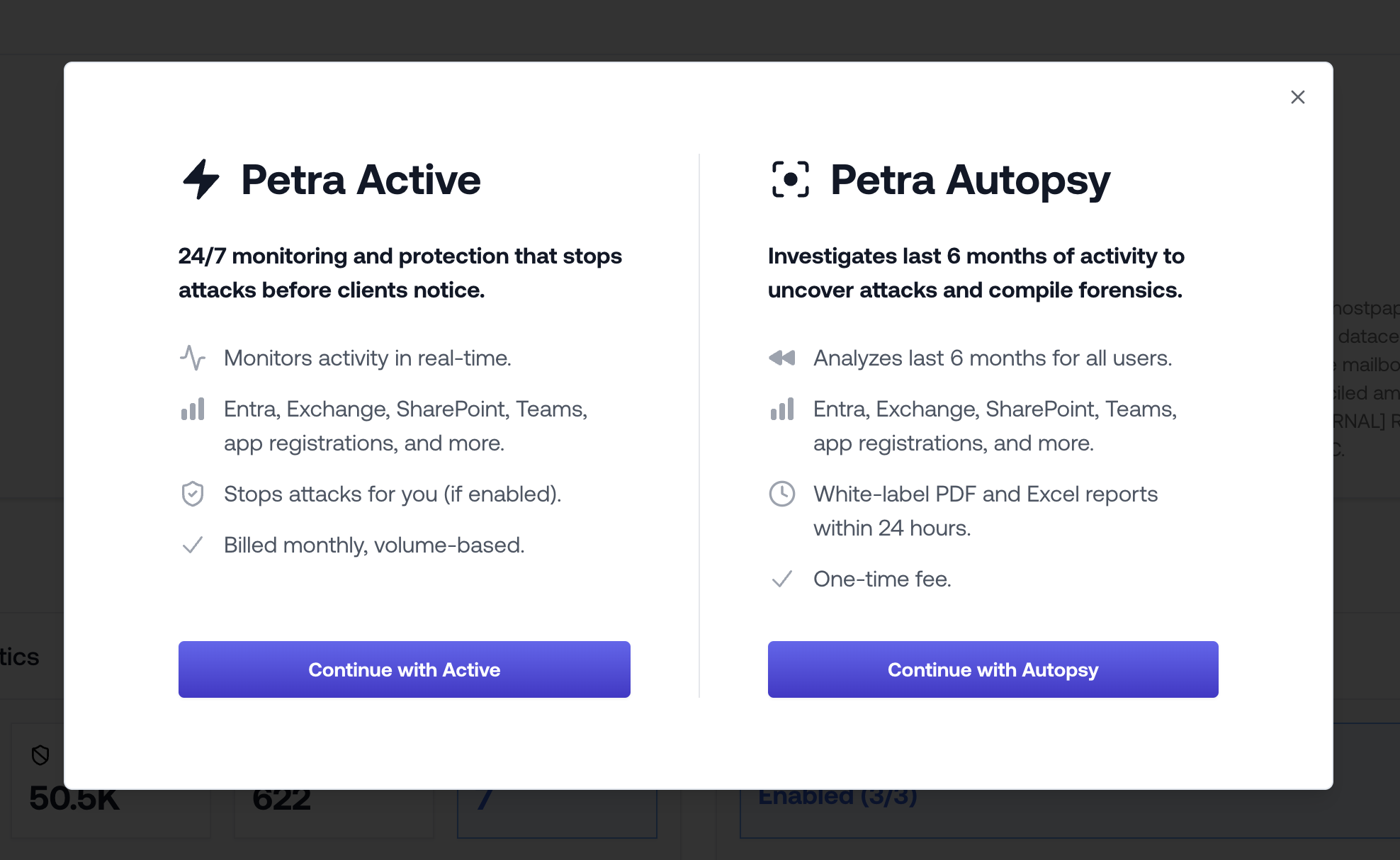
Petra Autopsy: Incident Response for BECs
May 23, 2025
Improved White-label Threat Remediation Report
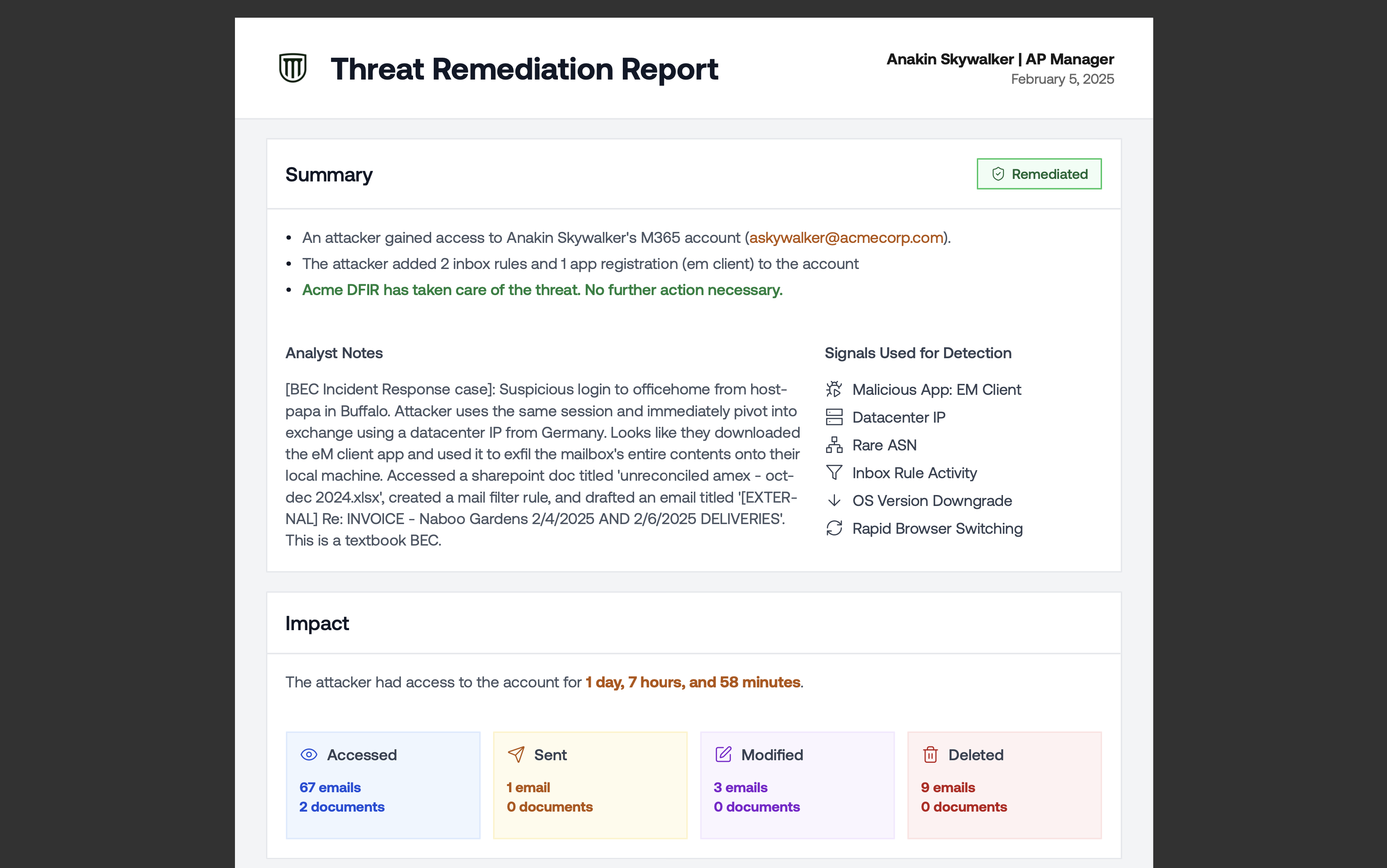
- New executive summary for quick read-through.
- Attack duration and impact (crowd favorites in the portal) are now in the PDF.
- More compact timeline of events table on the second page.
May 16, 2025
Tenant-specific Access
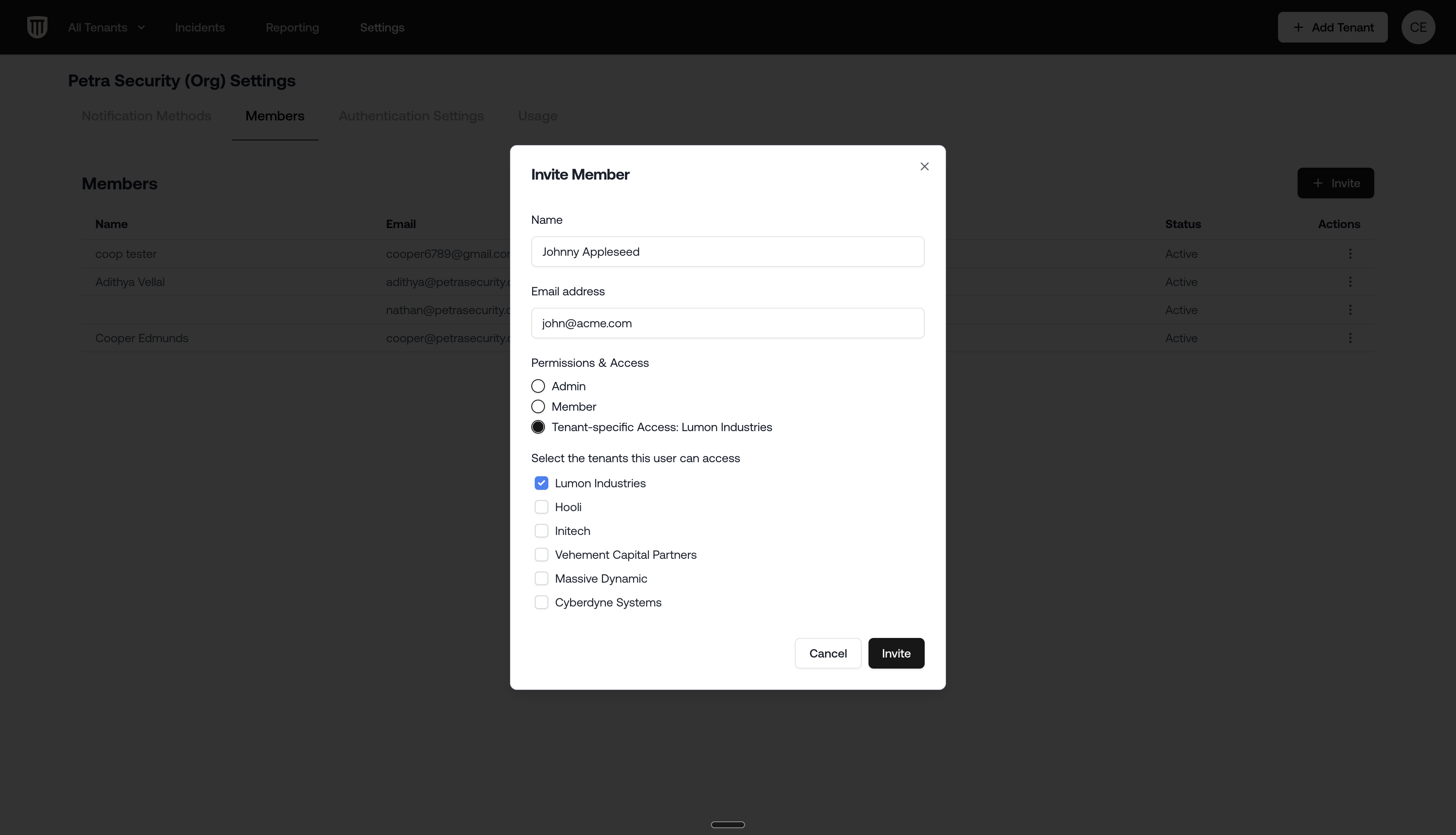
- Giving access to a client who needs to see the portal themselves.
- Least-privilege access to a subset of tenants for an AE or technical team member.
May 12, 2025
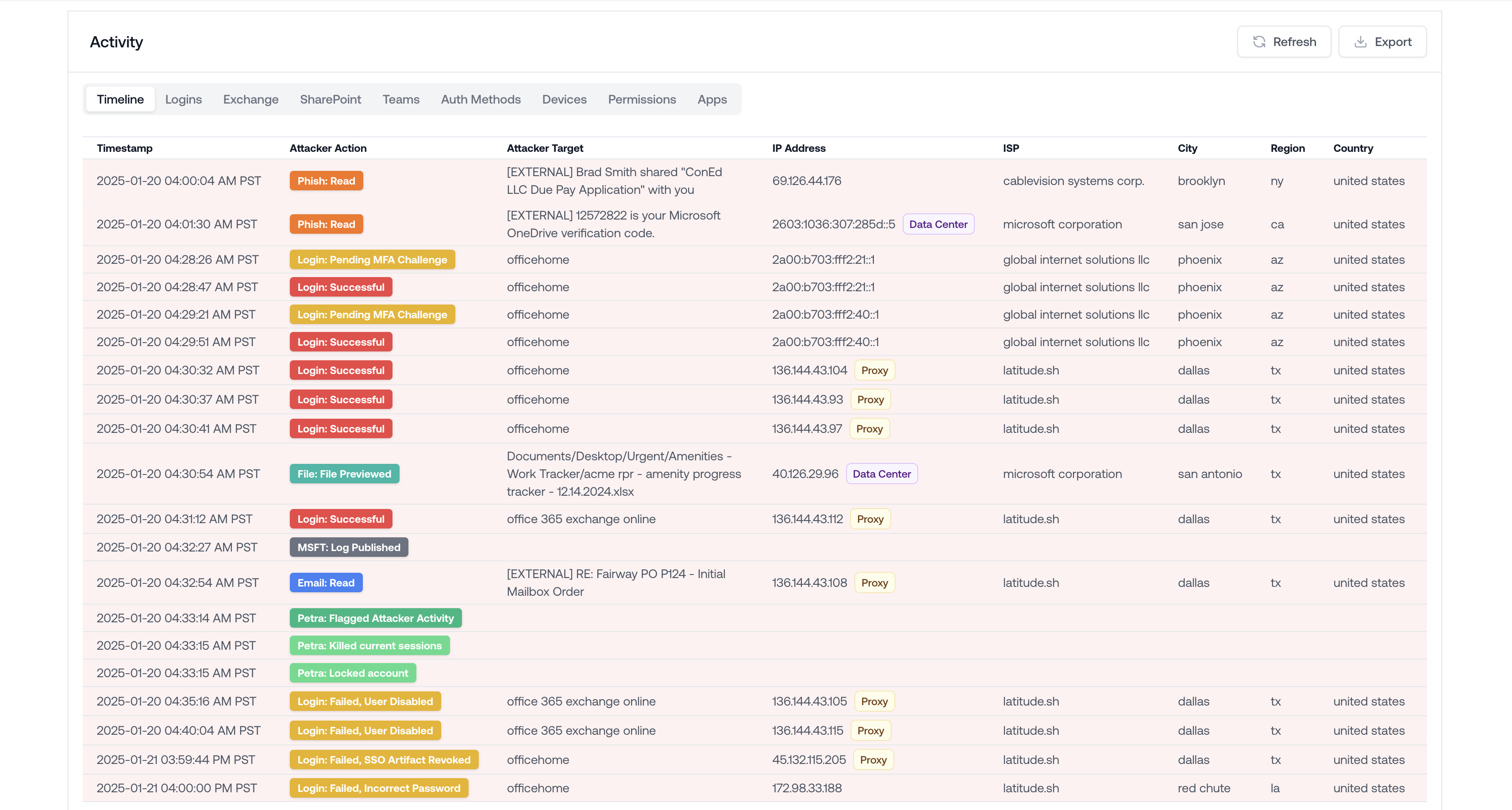
Revamped Attack Timeline
May 9, 2025
Attack Impact
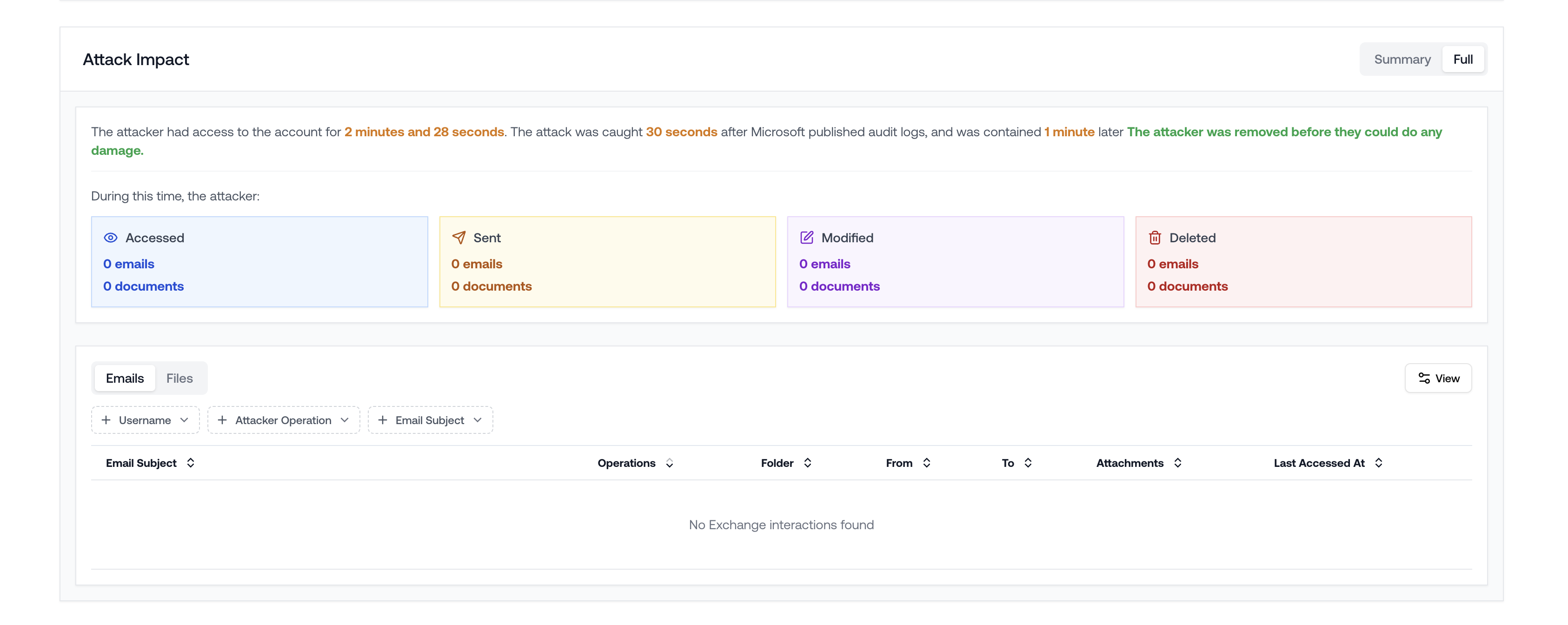
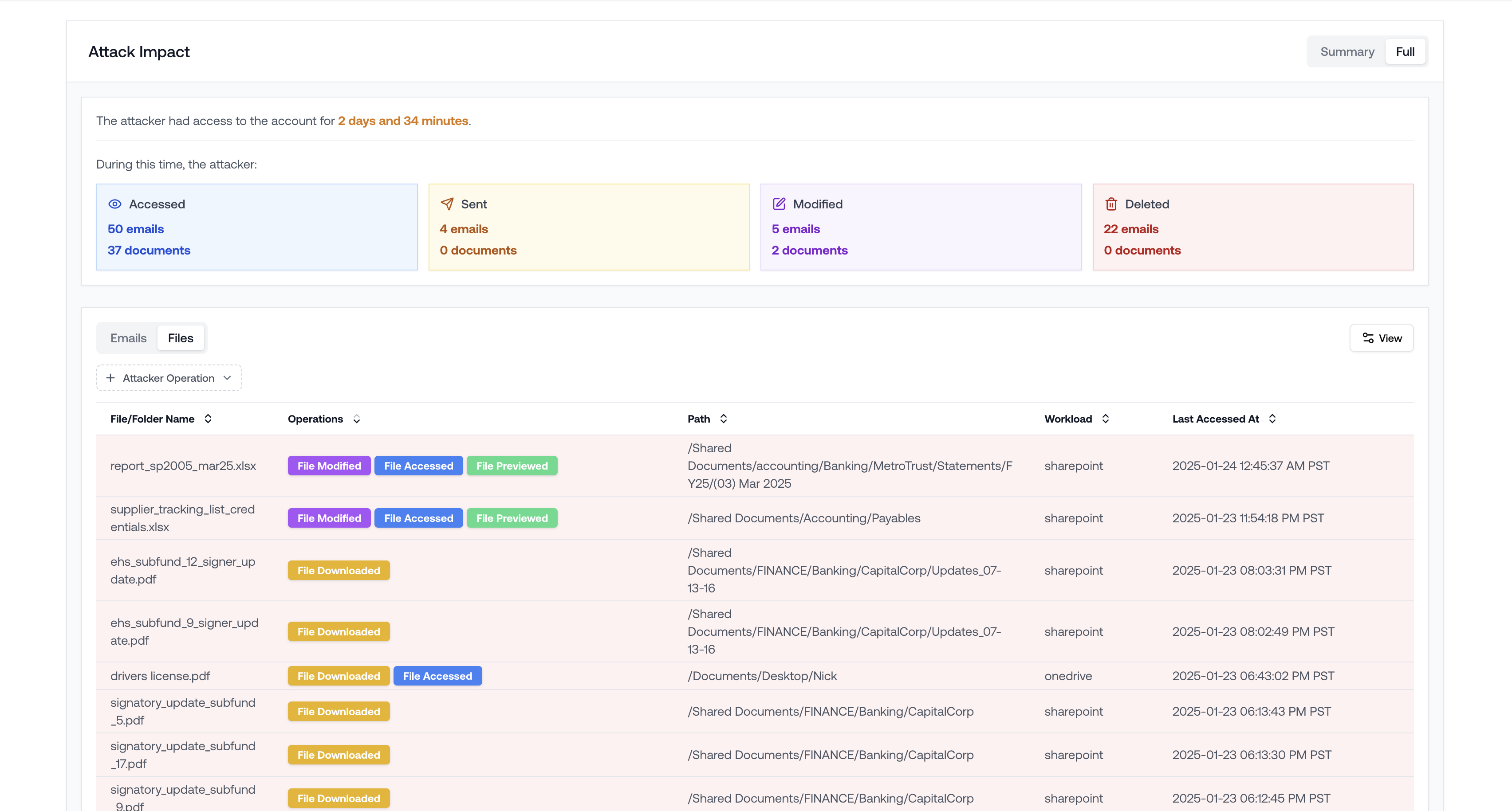
- What emails did the attacker send? To whom? (Likely to laterally phish).
- What files did the attacker modify?
- What did the attacker delete?
May 2, 2025
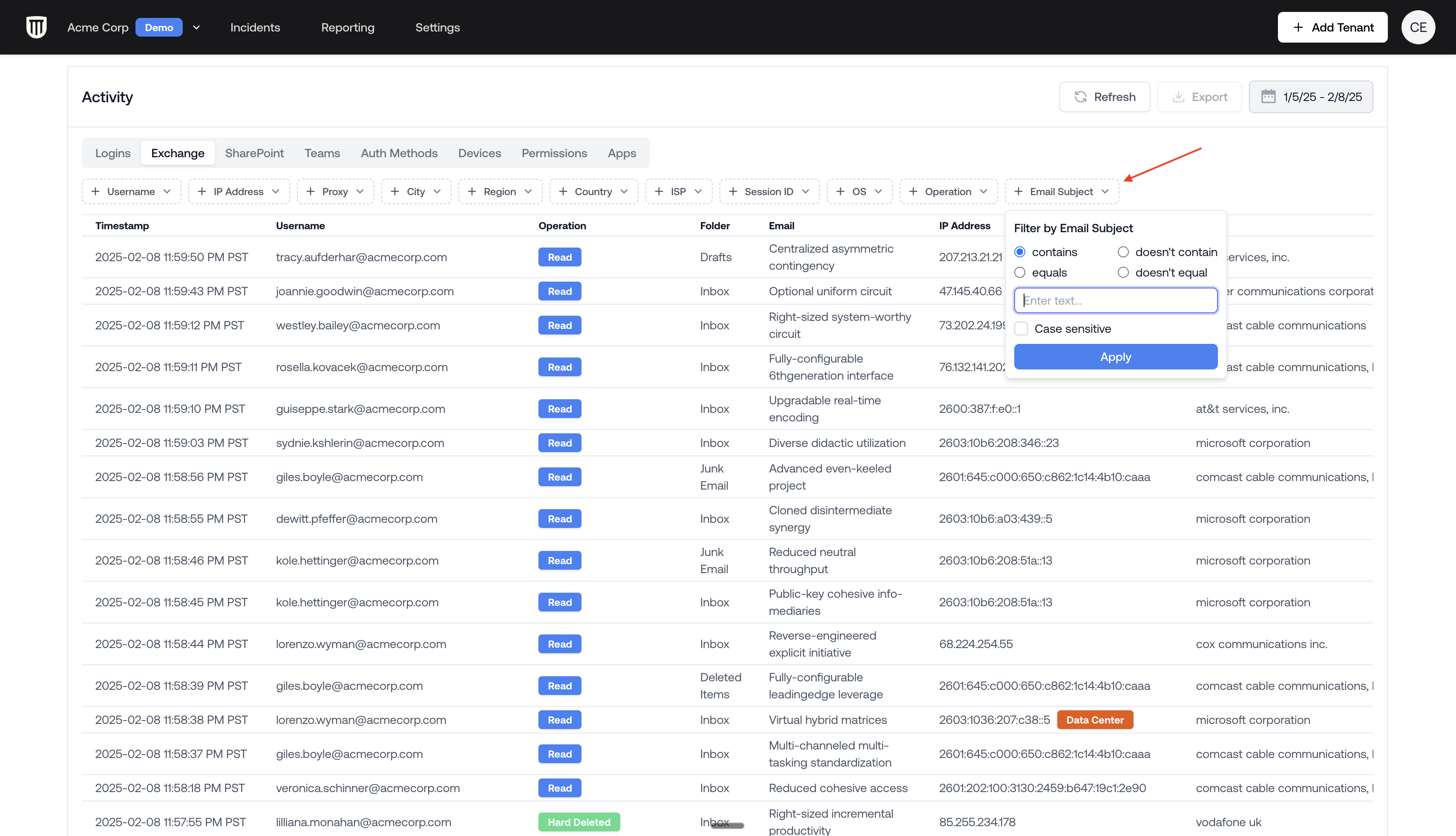
Tenant-wide Email Subject Search
April 25, 2025
Phish Similarity Search
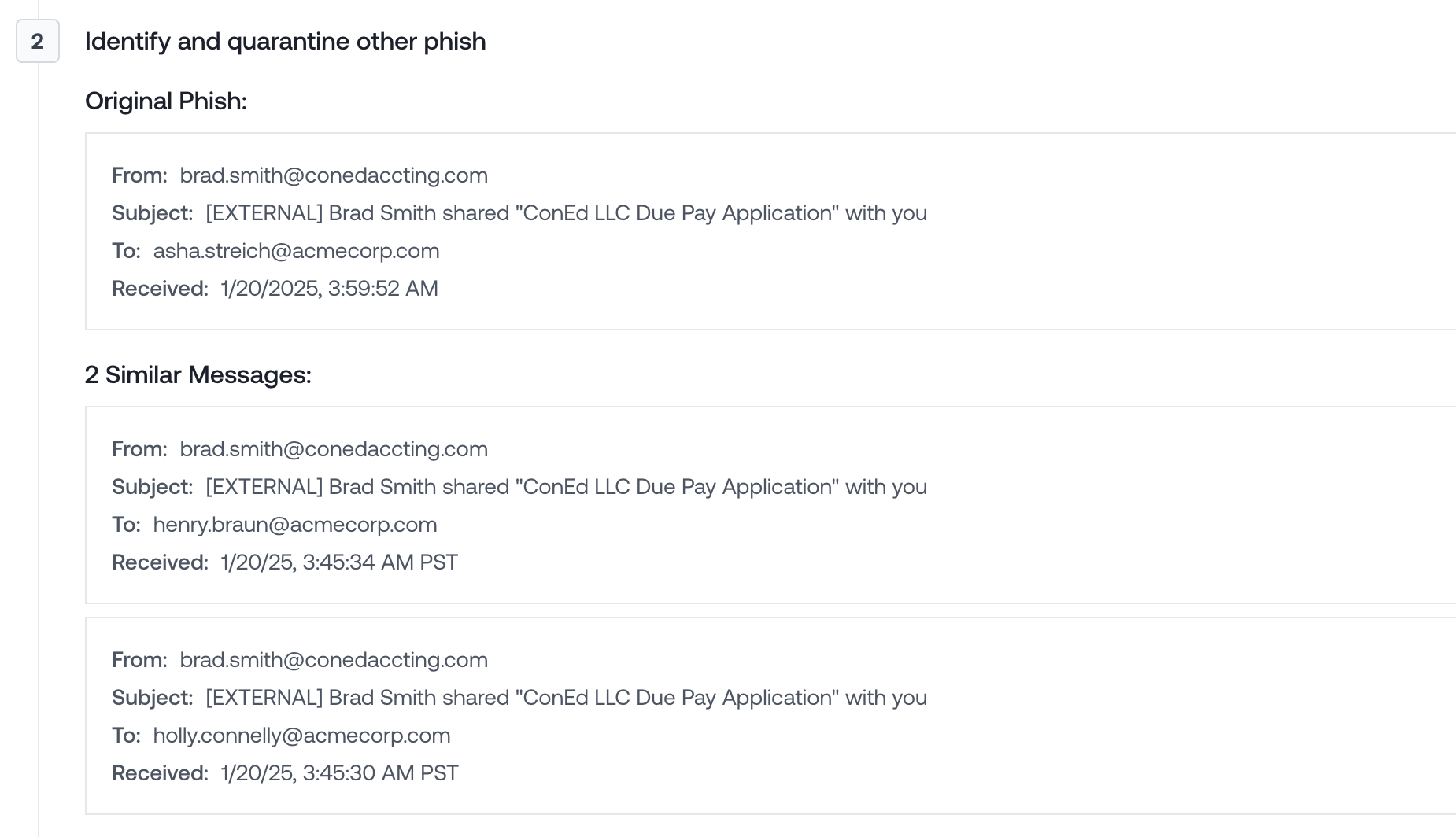
Email Interactions Panel

Other updates this week:
- Incident logs export: Export all logs from an incident as .xlsx
- User list export: Export all users in a tenant as .xlsx
April 18, 2025
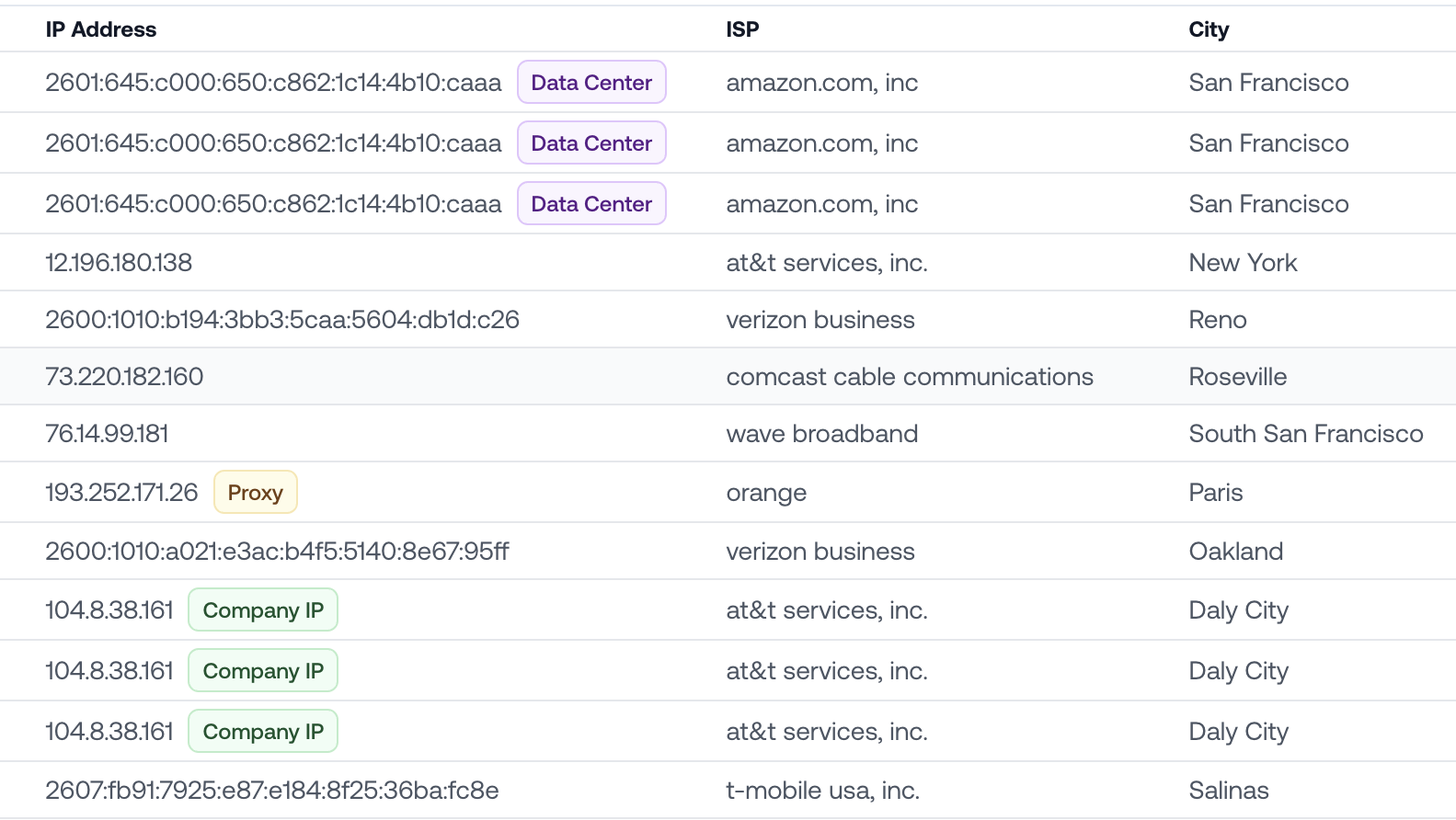
Company IP Detection
Logging Received Emails
‘Email Received’ events are now processed in addition to the traditional operations logged in the Unified Audit Log. Now, you can see who has received an email before they interact with it at all.April 11, 2025
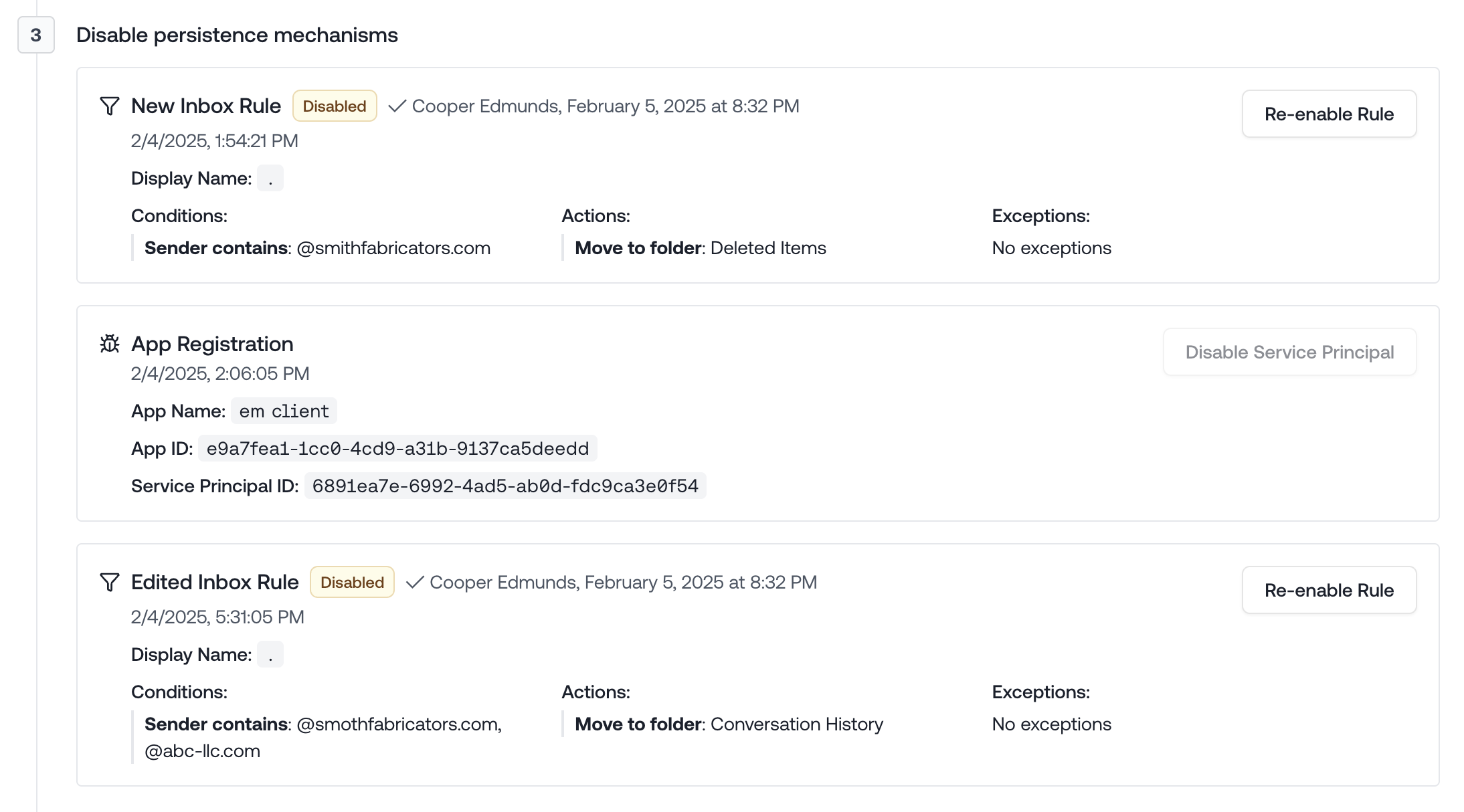
Disable Inbox Rules & App Registrations
April 3, 2025
Filter Auth Methods and Devices by username
- Search and filter authentication methods and devices by specific usernames for targeted investigations.
- Username is auto-populated to the compromised account during an incident.
Export spotlighted investigations as PDF
- Download complete records of spotlight investigations as PDF files for documentation and sharing.
- Reports are company-branded for professional presentation.
March 27, 2025
Phish Identification
- Petra identifies the email that is most likely the phish that led to the user’s compromise.
- Phish appears in attack timeline with forensic details showing when the user clicked on the phish and if the user deleted it thereafter.
- Identify if the attacker deleted the phish to cover their tracks.
Autotask Integration
- Generate tickets in an Autotask queue when there’s an incident.
Redesign tenant report
- White-labeled tenant report includes an executive summary on the first page.
Include inbox rule content in Attack Timeline
- See the contents of the inbox rules including their title, conditions, exceptions, and actions.
March 20, 2025
Added Acme Corp demo tenant to the portal
- Demo tenant now available in your portal for product exploration.
- Use this tenant to demonstrate the value of M365 monitoring to prospects.
Data Center tagging in activity viewer
- IP addresses belonging to data centers are tagged in the logs viewer.
- Easily identify traffic originating from cloud providers and hosting services.
Login stats sidebar
- View login frequency across various cities over time.
- Identify unusual login location patterns at a glance.
Multi-select filters on logs
- Add filters that match multiple values (e.g., country not equals US or Canada).
- Create complex queries to narrow down specific activity patterns.
Slack webhook integration
- Send incident notifications to Slack channels through webhooks.
Mail to UPN auto-resolution
- Searching by email address or UPN includes logs for both automatically.
March 13, 2025
Make the entire app mobile-friendly
- All Petra interfaces now fully support mobile devices.
- Control Microsoft from anywhere, even when away from your desk.
Add filters to rare activity
- Filter rare activity events by type.
User page
- View user details with complete metadata, authentication methods, and logs.
March 6, 2025
P1/P2 risk events
- If your tenant has P1/P2 risk events, you can see them in the portal.
- Investigate the activity in the context of surrounding logs.
Spotlighted investigations
- Review investigations into suspicious but ultimately benign behavior.
- Highlight this investigations to show the value of M365 monitoring.
Report Generator
- Generate comprehensive reports of tenant activity.
February 27, 2025
February 20, 2025
New failed attack types: password spray and known malicious IP
- Detection for password spray attacks against your tenant.
- Identification of connection attempts from known malicious IP addresses.
- Better visibility into failed attack attempts targeting your organization.
February 13, 2025
Apps, devices, auth methods, directory roles tables
- Track application usage, device access, authentication methods, and role assignments.
- Useful for tracking activity around an attack.
February 6, 2025
Filter by not equals
- Create exclusion filters (e.g., country not US, ISP not Comcast).
- Focus on activity from unexpected or non-standard sources.
Autocomplete some filters
- Autocomplete for username, UPN, browser, OS, etc. filters as you type.
- Faster filter creation with suggested values from your tenant data.
January 30, 2025
Share filter bar across all log sources
- Filters in activity viewer apply across all tables (logins, Exchange, SharePoint, Teams).
- Maintain consistent filtering criteria when switching between different log types.
Remediation readiness panel
- At-a-glance view of how you’ll be notified of incidents.
- Verify your notification channels are correctly configured.
API for SIEM integration
- API for pulling incidents using a cursor, designed for SIEM integration.
- Incorporate Petra incident data into your existing security workflows.
January 23, 2025
Users export
- Export all users in a tenant to spreadsheet format.
- Analyze user data outside of the Petra platform.
Failed attacks
- View targeting patterns and attack toolkits used against your organization.
- Identify which users are being targeted, typically executives.
- Use this data as a sales artifact to demonstrate M365 monitoring value.
January 16, 2025
Remediation controls
- Lock down compromised accounts with a single click.
- For hybrid tenants, Petra renews the lock repeatedly to prevent on-prem sync from unlocking the account.
Teams integration
- Send incident notifications to Microsoft Teams channels.
- Keep your security team informed through their existing communication platforms.
January 9, 2025
Third party app names
- Track third-party apps that users sign into within the activity viewer.
- See friendly application names instead of just application IDs.
ConnectWise integration
- Automatically generate tickets in ConnectWise when incidents occur.
- Streamline incident response through your established ticketing system.
January 2, 2025
Latent attacker search
- Scan for attackers already present in the tenant before monitoring began.
- Identify and remediate existing compromises during the onboarding process.
- Get immediate security value from day one of Petra implementation.
2024 Archive
An Eventful Year
- Launched initial activity viewer with login logs
- Added Exchange Online activity tracking
- Added SharePoint and OneDrive activity tracking
- Added Teams activity tracking
- Added email notifications for incidents
- Added webhook notifications for incidents
- Built investigation tools to analyze raw logs with very low latency
- Added custom geolocation data enrichment to correct Microsoft’s often incorrect IP geolocation
- Added tenant-wide activity search
- Built role-based access control for members in the portal
- Built PDF export reporting capabilities